Sophos-Konsole: Unterschied zwischen den Versionen
Zur Navigation springen
Zur Suche springen
Thomas (Diskussion | Beiträge) |
Thomas (Diskussion | Beiträge) |
||
| (6 dazwischenliegende Versionen desselben Benutzers werden nicht angezeigt) | |||
| Zeile 7: | Zeile 7: | ||
=cc= | =cc= | ||
command-line client | command-line client | ||
| + | ==password reset== | ||
| + | *cc system_password_reset | ||
| + | next login | ||
| + | |||
| + | [[Datei:sophos-konsole2.png]] | ||
| + | ==factory reset== | ||
| + | *cc | ||
| + | 127.0.0.1 MAIN > RAW | ||
| + | Switched to RAW mode. | ||
| + | 127.0.0.1 RAW > system_factory_reset | ||
| + | Calling Confd function system_factory_reset() | ||
| + | result: 1 | ||
| + | 127.0.0.1 RAW > exit | ||
| + | *reboot | ||
| + | |||
=ifstat= | =ifstat= | ||
*ifstat | *ifstat | ||
| Zeile 56: | Zeile 71: | ||
CONFIRMED tcp -- 192.168.2.0/24 anywhere tcp spts:tcpmux:65535 multiport dports http-alt,http,ndl-aas,https | CONFIRMED tcp -- 192.168.2.0/24 anywhere tcp spts:tcpmux:65535 multiport dports http-alt,http,ndl-aas,https | ||
</pre> | </pre> | ||
| − | ==number of established connections= | + | ==number of established connections== |
*less /proc/net/ip_conntrack | grep ESTA | wc -l | *less /proc/net/ip_conntrack | grep ESTA | wc -l | ||
1907 | 1907 | ||
| Zeile 88: | Zeile 103: | ||
000 "L_REF_IpsL2tForTic_0": 192.168.2.199[192.168.2.199]:17/1701...%any[%any]:17/%any==={0.0.0.0/0}; unrouted; eroute owner: #0 | 000 "L_REF_IpsL2tForTic_0": 192.168.2.199[192.168.2.199]:17/1701...%any[%any]:17/%any==={0.0.0.0/0}; unrouted; eroute owner: #0 | ||
000 "L_REF_IpsL2tForTic_0": newest ISAKMP SA: #0; newest IPsec SA: #0; | 000 "L_REF_IpsL2tForTic_0": newest ISAKMP SA: #0; newest IPsec SA: #0; | ||
| + | ==view tunnel status== | ||
| + | *cc get_ipsec_status | ||
| + | <pre> | ||
| + | { | ||
| + | 'REF_IpsSitVpnasasop' => { | ||
| + | 0 => { | ||
| + | 0 => { | ||
| + | 'established' => 1, | ||
| + | 'ike_auth' => 'psk', | ||
| + | 'ike_dh' => 'MODP_1024', | ||
| + | 'ike_dpd' => 1, | ||
| + | 'ike_encryption' => 'AES_CBC_256', | ||
| + | 'ike_hash' => 'HMAC_MD5', | ||
| + | 'ike_lifetime' => '7800s', | ||
| + | 'ike_natt' => 0, | ||
| + | 'ike_pfs' => 'MODP_1536', | ||
| + | 'ipsec_encryption' => 'AES_CBC_256', | ||
| + | 'ipsec_hash' => 'HMAC_MD5', | ||
| + | 'ipsec_lifetime' => '3600s', | ||
| + | 'ipsec_sa' => 46, | ||
| + | 'ipsec_spi_in' => '85efc153', | ||
| + | 'ipsec_spi_out' => '5e91d523', | ||
| + | 'isakmp_sa' => 45, | ||
| + | 'left' => '192.168.2.199', | ||
| + | 'leftid' => '192.168.2.199', | ||
| + | 'leftsubnet' => '10.2.2.0/24', | ||
| + | 'right' => '192.168.2.198', | ||
| + | 'rightid' => '192.168.2.198', | ||
| + | 'rightsubnet' => '192.168.3.0/24' | ||
| + | } | ||
| + | }, | ||
| + | 'all_established' => 1, | ||
| + | 'established' => 1, | ||
| + | 'expected' => 1 | ||
| + | } | ||
| + | } | ||
| + | </pre> | ||
=links= | =links= | ||
*https://community.sophos.com/products/unified-threat-management/f/51/t/21326 | *https://community.sophos.com/products/unified-threat-management/f/51/t/21326 | ||
*http://www.greenvalleyconsulting.org/2013/07/09/sophos-utm-command-line-useful-shell-commands-and-processes/?doing_wp_cron=1474373506.6931669712066650390625 | *http://www.greenvalleyconsulting.org/2013/07/09/sophos-utm-command-line-useful-shell-commands-and-processes/?doing_wp_cron=1474373506.6931669712066650390625 | ||
| + | *https://valentin-laett.ch/projekte/sophos-utm_tipps.php | ||
Aktuelle Version vom 20. September 2016, 12:45 Uhr
ssh
- ssh loginuser@sophos30
loginuser@sophos30:/home/login >
root access
- su -
sophos30:/root #
cc
command-line client
password reset
- cc system_password_reset
next login
factory reset
- cc
127.0.0.1 MAIN > RAW Switched to RAW mode. 127.0.0.1 RAW > system_factory_reset Calling Confd function system_factory_reset() result: 1 127.0.0.1 RAW > exit
- reboot
ifstat
- ifstat
#kernel
Interface RX Pkts/Rate TX Pkts/Rate RX Data/Rate TX Data/Rate
RX Errs/Drop TX Errs/Drop RX Over/Rate TX Coll/Rate
lo 0 0 0 0 0 0 0 0
0 0 0 0 0 0 0 0
eth0 17 0 15 0 1218 0 2254 0
0 0 0 0 0 0 0 0
eth1 0 0 0 0 0 0 0 0
0 0 0 0 0 0 0 0
eth2 0 0 0 0 0 0 0 0
0 0 0 0 0 0 0 0
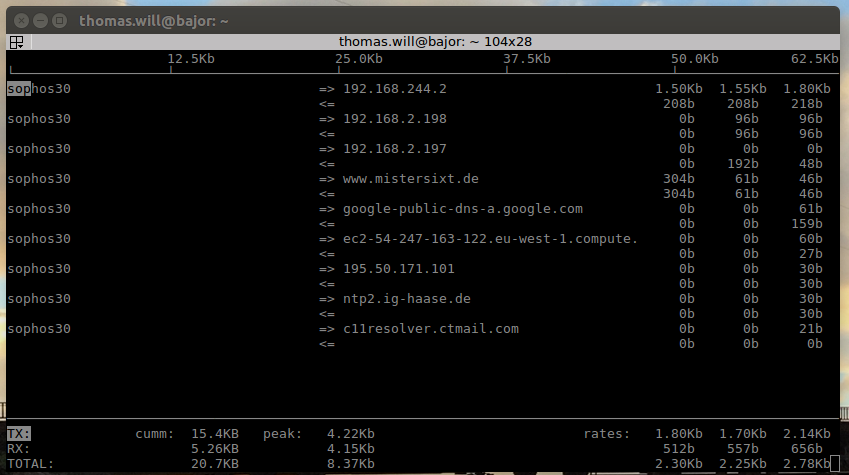
iftop
- iftop
iptables
view automatic firewall rules
- iptables -L AUTO_FORWARD
Chain AUTO_FORWARD (1 references) target prot opt source destination CONFIRMED all -- 192.168.3.0/24 10.2.2.0/24 policy match dir in pol ipsec mode tunnel CONFIRMED all -- 10.2.2.0/24 192.168.3.0/24 policy match dir out pol ipsec mode tunnel CONFIRMED all -- 192.168.77.0/24 10.2.2.0/24 policy match dir in pol ipsec mode tunnel CONFIRMED all -- 10.2.2.0/24 192.168.77.0/24 policy match dir out pol ipsec mode tunnel DROP icmp -- anywhere anywhere icmptype 8 code 0 policy match dir in pol none CONFIRMED icmp -- anywhere anywhere icmptype 8 code 0 DROP icmp -- anywhere anywhere icmptype 0 code 0 policy match dir in pol none CONFIRMED icmp -- anywhere anywhere icmptype 0 code 0
view own firewall rules
- iptables -L USR_FORWARD
Chain USR_FORWARD (1 references) target prot opt source destination CONFIRMED tcp -- 10.2.2.0/24 anywhere tcp spts:tcpmux:65535 multiport dports http,https CONFIRMED tcp -- 192.168.2.0/24 anywhere tcp spts:tcpmux:65535 dpt:domain CONFIRMED udp -- 192.168.2.0/24 anywhere udp spts:tcpmux:65535 dpt:domain CONFIRMED tcp -- 192.168.2.0/24 anywhere tcp spts:tcpmux:65535 dpt:net-assistant CONFIRMED udp -- 192.168.2.0/24 anywhere udp spts:tcpmux:65535 dpt:net-assistant CONFIRMED tcp -- 192.168.2.0/24 anywhere tcp spts:tcpmux:65535 multiport dports ms-wbt-server,5900,ms-wbt-server,5900,ssh,telnet,ica CONFIRMED tcp -- 192.168.2.0/24 anywhere tcp spts:tcpmux:65535 multiport dports smtps,imaps,imap,pop3,smtp,pop3s CONFIRMED udp -- 192.168.2.0/24 anywhere udp spts:tcpmux:65535 dpt:tftp CONFIRMED tcp -- 192.168.2.0/24 anywhere tcp spts:tcpmux:65535 dpt:ftp CONFIRMED tcp -- 192.168.2.0/24 anywhere tcp spts:tcpmux:65535 multiport dports http-alt,http,ndl-aas,https
number of established connections
- less /proc/net/ip_conntrack | grep ESTA | wc -l
1907
number of all connections
- less /proc/net/ip_conntrack | wc -l
3315
number of connections with status WAIT (close_wait)
- less /proc/net/ip_conntrack | grep WAIT | wc -l
39
ipsec
status
- ipsec status
000 "L_REF_IpsL2tForTic_0": 192.168.2.199[192.168.2.199]:17/1701...%any[%any]:17/%any==={0.0.0.0/0}; unrouted; eroute owner: #0
000 "L_REF_IpsL2tForTic_0": newest ISAKMP SA: #0; newest IPsec SA: #0;
000 "L_REF_IpsL2tForTic_1": 192.168.2.199[192.168.2.199]:17/0...%any[%any]:17/%any==={0.0.0.0/0}; unrouted; eroute owner: #0
000 "L_REF_IpsL2tForTic_1": newest ISAKMP SA: #0; newest IPsec SA: #0;
000 "S_REF_IpsSitSophosipfi_0": 10.2.2.0/24===192.168.2.199[192.168.2.199]...192.168.2.151[192.168.2.151]===192.168.77.0/24; unrouted; eroute owner: #0
000 "S_REF_IpsSitSophosipfi_0": newest ISAKMP SA: #0; newest IPsec SA: #0;
000 "S_REF_IpsSitVpnasasop_0": 10.2.2.0/24===192.168.2.199[192.168.2.199]...192.168.2.198[192.168.2.198]===192.168.3.0/24; erouted; eroute owner: #43
000 "S_REF_IpsSitVpnasasop_0": newest ISAKMP SA: #42; newest IPsec SA: #43;
000
000 #44: "S_REF_IpsSitSophosipfi_0" STATE_MAIN_I1 (sent MI1, expecting MR1); EVENT_RETRANSMIT in 13s
000 #44: pending Phase 2 for "S_REF_IpsSitSophosipfi_0" replacing #0
000 #43: "S_REF_IpsSitVpnasasop_0" STATE_QUICK_I2 (sent QI2, IPsec SA established); EVENT_SA_REPLACE in 1919s; newest IPSEC; eroute owner
000 #43: "S_REF_IpsSitVpnasasop_0" esp.4bfe2b0a@192.168.2.198 (0 bytes) esp.73ee7324@192.168.2.199 (0 bytes); tunnel
000 #42: "S_REF_IpsSitVpnasasop_0" STATE_MAIN_I4 (ISAKMP SA established); EVENT_SA_REPLACE in 6243s; newest ISAKMP
- ipsec status L_REF_IpsL2tForTic_0
000 "L_REF_IpsL2tForTic_0": 192.168.2.199[192.168.2.199]:17/1701...%any[%any]:17/%any==={0.0.0.0/0}; unrouted; eroute owner: #0
000 "L_REF_IpsL2tForTic_0": newest ISAKMP SA: #0; newest IPsec SA: #0;
view tunnel status
- cc get_ipsec_status
{
'REF_IpsSitVpnasasop' => {
0 => {
0 => {
'established' => 1,
'ike_auth' => 'psk',
'ike_dh' => 'MODP_1024',
'ike_dpd' => 1,
'ike_encryption' => 'AES_CBC_256',
'ike_hash' => 'HMAC_MD5',
'ike_lifetime' => '7800s',
'ike_natt' => 0,
'ike_pfs' => 'MODP_1536',
'ipsec_encryption' => 'AES_CBC_256',
'ipsec_hash' => 'HMAC_MD5',
'ipsec_lifetime' => '3600s',
'ipsec_sa' => 46,
'ipsec_spi_in' => '85efc153',
'ipsec_spi_out' => '5e91d523',
'isakmp_sa' => 45,
'left' => '192.168.2.199',
'leftid' => '192.168.2.199',
'leftsubnet' => '10.2.2.0/24',
'right' => '192.168.2.198',
'rightid' => '192.168.2.198',
'rightsubnet' => '192.168.3.0/24'
}
},
'all_established' => 1,
'established' => 1,
'expected' => 1
}
}