Strongswan zu strongswan psk ikev2 site to site: Unterschied zwischen den Versionen
Zur Navigation springen
Zur Suche springen
| Zeile 41: | Zeile 41: | ||
s2s{4}: 10.82.243.0/24 === 10.82.244.0/24 | s2s{4}: 10.82.243.0/24 === 10.82.244.0/24 | ||
=TCPDump der Verbindung= | =TCPDump der Verbindung= | ||
| − | *tcpdump -ni eth0 port 500 or esp | + | *tcpdump -ni eth0 port 500 or esp |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
=Mehrere Subnetze= | =Mehrere Subnetze= | ||
Version vom 10. September 2023, 11:09 Uhr
Konfiguration
ipsec.conf
Erklärung
- /etc/ipsec.conf Erklärung
Datei
conn s2s
authby=secret
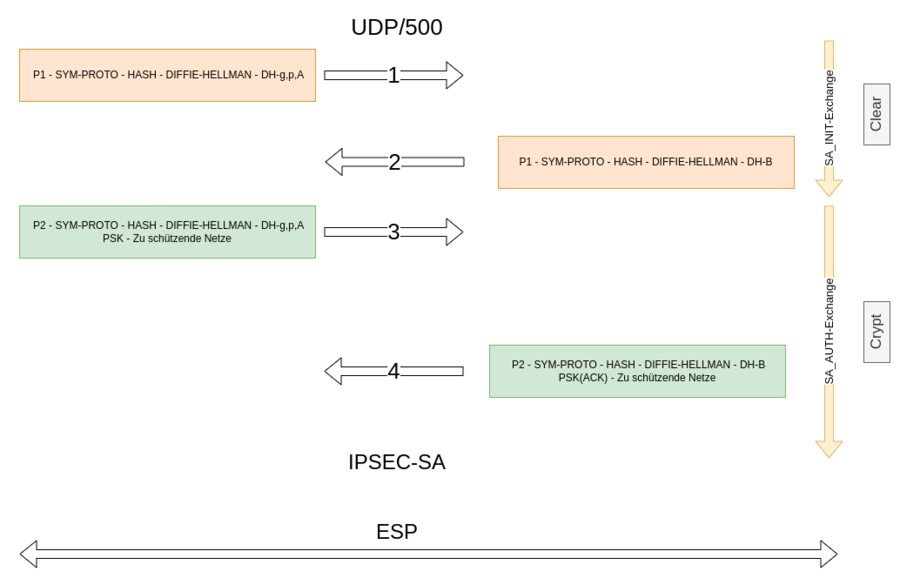
keyexchange=ikev2
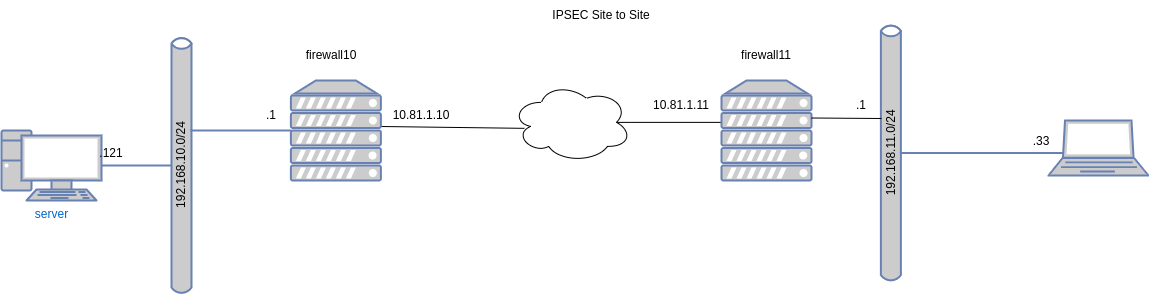
left=10.81.1.10
leftsubnet=192.168.10.0/24
mobike=no
right=10.81.1.11
rightsubnet=192.168.11.0/24
ike=aes256-sha256-modp4096!
esp=aes256-sha256-modp4096!
auto=start
ipsec.secrets
- ID Kombination mit Authentifizierungsmethodes
- cat /etc/ipsec.secrets
10.81.1.10 10.81.1.11 : PSK "suxer"
Handling
Up
- ipsec up s2s
Down
- ipsec down s2s
Status
- ipsec status s2s
Security Associations (1 up, 0 connecting):
s2s[4]: ESTABLISHED 7 seconds ago, 10.82.227.12[10.82.227.12]...10.82.227.22[10.82.227.22]
s2s{4}: INSTALLED, TUNNEL, reqid 1, ESP SPIs: cef198fc_i c4de821a_o
s2s{4}: 10.82.243.0/24 === 10.82.244.0/24
TCPDump der Verbindung
- tcpdump -ni eth0 port 500 or esp
Mehrere Subnetze
alice und tiazel
- /etc/ipsec.conf
conn s2s
authby=secret
keyexchange=ikev2
left=10.81.1.10
leftsubnet=192.168.10.0/24
mobike=no
right=10.81.1.11
rightsubnet=192.168.11.0/24,192.168.33.0/24
ike=aes256-sha256-modp4096!
esp=aes256-sha256-modp4096!
auto=start
- ipsec status
Security Associations (1 up, 0 connecting):
s2s[2]: ESTABLISHED 5 seconds ago, 10.82.227.12[10.82.227.12]...10.82.227.22[10.82.227.22]
s2s{2}: INSTALLED, TUNNEL, reqid 1, ESP SPIs: cda686f1_i c7f9fce6_o
s2s{2}: 10.82.243.0/24 192.168.20.0/24 === 10.82.244.0/24