Sophos 2 cisco asa: Unterschied zwischen den Versionen
Zur Navigation springen
Zur Suche springen
David (Diskussion | Beiträge) |
David (Diskussion | Beiträge) |
||
| (11 dazwischenliegende Versionen desselben Benutzers werden nicht angezeigt) | |||
| Zeile 1: | Zeile 1: | ||
| − | = | + | =sophos site= |
| − | configure terminal | + | [[Datei:soph-asa1.png]] |
| + | |||
| + | |||
| + | |||
| + | [[Datei:soph-asa2.png]] | ||
| + | |||
| + | =asa site= | ||
| + | ==interfaces einrichten== | ||
| + | configure terminal | ||
interface Vlan2 | interface Vlan2 | ||
ip address 192.168.244.185 255.255.248.0 | ip address 192.168.244.185 255.255.248.0 | ||
| Zeile 14: | Zeile 22: | ||
name-server 192.168.240.200 | name-server 192.168.240.200 | ||
end | end | ||
| − | + | ==nach ausen freigeben== | |
| − | + | object network obj-lan | |
| + | subnet 10.20.170.0 255.255.255.0 | ||
| + | nat (if-inside,if-outside) dynamic interface | ||
| + | end | ||
| + | ==phase1== | ||
configure terminal | configure terminal | ||
| − | access-list acl-asa- | + | crypto ikev1 policy 10 |
| + | authentication pre-share | ||
| + | encryption aes-256 | ||
| + | hash md5 | ||
| + | group 5 | ||
| + | lifetime 28800 | ||
| + | crypto ikev1 enable if-outside | ||
| + | ==phase2== | ||
| + | access-list acl-asa-soph extended permit ip 10.20.170.0 255.255.255.0 10.20.0.0 255.255.0.0 | ||
crypto isakmp identity address | crypto isakmp identity address | ||
crypto isakmp enable if-outside | crypto isakmp enable if-outside | ||
crypto ipsec transform-set AES256-MD5 esp-aes-256 esp-md5-hmac | crypto ipsec transform-set AES256-MD5 esp-aes-256 esp-md5-hmac | ||
| − | crypto map vpn-asa- | + | crypto map vpn-asa-soph 10 match address acl-asa-soph |
| − | crypto map vpn-asa- | + | crypto map vpn-asa-soph 10 set pfs group5 |
| − | crypto map vpn-asa- | + | crypto map vpn-asa-soph 10 set peer 192.168.244.130 |
| − | crypto map vpn-asa- | + | crypto map vpn-asa-soph 10 set ikev1 transform-set AES256-MD5 |
| − | crypto map vpn-asa- | + | crypto map vpn-asa-soph interface if-outside |
tunnel-group 192.168.244.130 type ipsec-l2l | tunnel-group 192.168.244.130 type ipsec-l2l | ||
tunnel-group 192.168.244.130 ipsec-attributes | tunnel-group 192.168.244.130 ipsec-attributes | ||
pre-shared-key streng-geheim | pre-shared-key streng-geheim | ||
| + | end | ||
| + | ==nat ausnahme== | ||
object network no-nat | object network no-nat | ||
subnet 10.20.0.0 255.255.0.0 | subnet 10.20.0.0 255.255.0.0 | ||
nat (if-inside,if-outside) source static obj-lan obj-lan destination static no-nat no-nat | nat (if-inside,if-outside) source static obj-lan obj-lan destination static no-nat no-nat | ||
| + | ==ping freischalten== | ||
| + | configure terminal | ||
| + | policy-map icmp_policy | ||
| + | policy-map global_policy | ||
| + | class inspection_default | ||
| + | inspect icmp | ||
| + | end | ||
| + | |||
| + | |||
| + | * so sollte es aussehen wenn die vpn steht | ||
| + | [[Datei:soph-asa3.png]] | ||
Aktuelle Version vom 18. März 2016, 11:13 Uhr
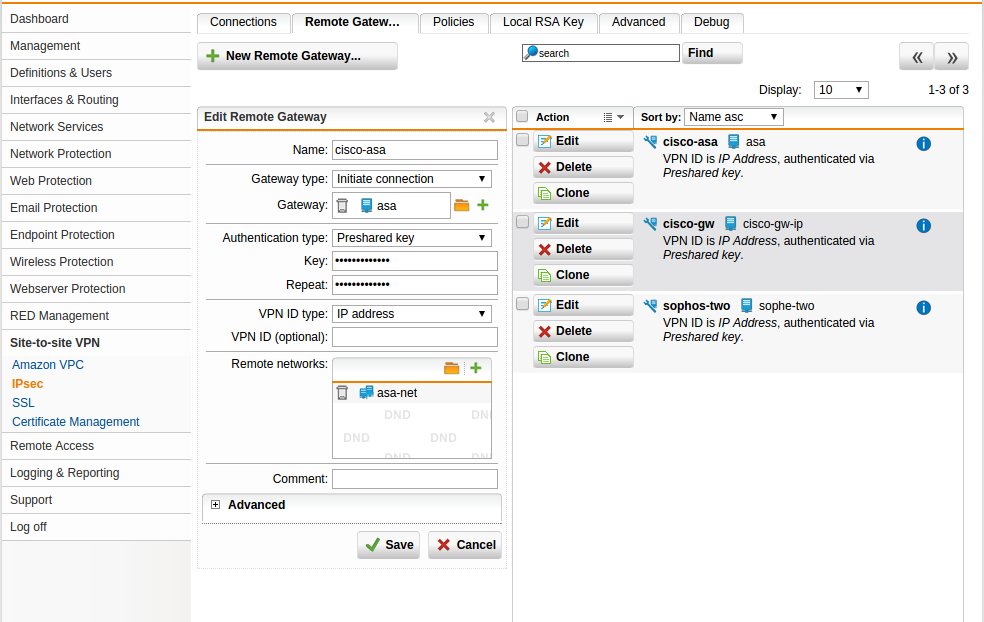
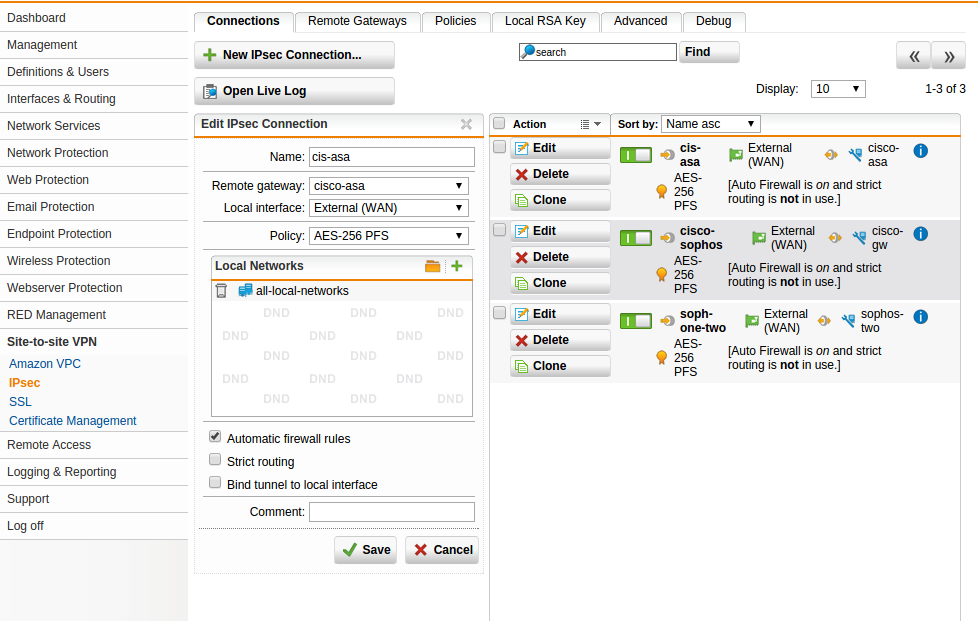
sophos site
asa site
interfaces einrichten
configure terminal interface Vlan2 ip address 192.168.244.185 255.255.248.0 nameif if-outside interface Vlan1 nameif if-inside ip address 10.20.170.1 255.255.255.0 route if-outside 0.0.0.0 0.0.0.0 192.168.240.100 domain-name xinux.org dns domain-lookup if-outside dns server-group DefaultDNS name-server 192.168.240.200 end
nach ausen freigeben
object network obj-lan subnet 10.20.170.0 255.255.255.0 nat (if-inside,if-outside) dynamic interface end
phase1
configure terminal crypto ikev1 policy 10 authentication pre-share encryption aes-256 hash md5 group 5 lifetime 28800 crypto ikev1 enable if-outside
phase2
access-list acl-asa-soph extended permit ip 10.20.170.0 255.255.255.0 10.20.0.0 255.255.0.0 crypto isakmp identity address crypto isakmp enable if-outside crypto ipsec transform-set AES256-MD5 esp-aes-256 esp-md5-hmac crypto map vpn-asa-soph 10 match address acl-asa-soph crypto map vpn-asa-soph 10 set pfs group5 crypto map vpn-asa-soph 10 set peer 192.168.244.130 crypto map vpn-asa-soph 10 set ikev1 transform-set AES256-MD5 crypto map vpn-asa-soph interface if-outside tunnel-group 192.168.244.130 type ipsec-l2l tunnel-group 192.168.244.130 ipsec-attributes pre-shared-key streng-geheim end
nat ausnahme
object network no-nat subnet 10.20.0.0 255.255.0.0 nat (if-inside,if-outside) source static obj-lan obj-lan destination static no-nat no-nat
ping freischalten
configure terminal policy-map icmp_policy policy-map global_policy class inspection_default inspect icmp end
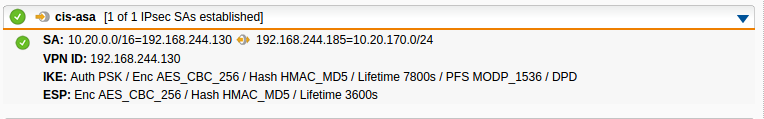
- so sollte es aussehen wenn die vpn steht