Snort Install Windows: Unterschied zwischen den Versionen
Zur Navigation springen
Zur Suche springen
Thomas (Diskussion | Beiträge) |
Thomas (Diskussion | Beiträge) |
||
| (15 dazwischenliegende Versionen von 2 Benutzern werden nicht angezeigt) | |||
| Zeile 1: | Zeile 1: | ||
=Download= | =Download= | ||
| + | *http://www.winpcap.org/install/default.htm | ||
*https://www.snort.org/downloads | *https://www.snort.org/downloads | ||
| + | |||
=Install= | =Install= | ||
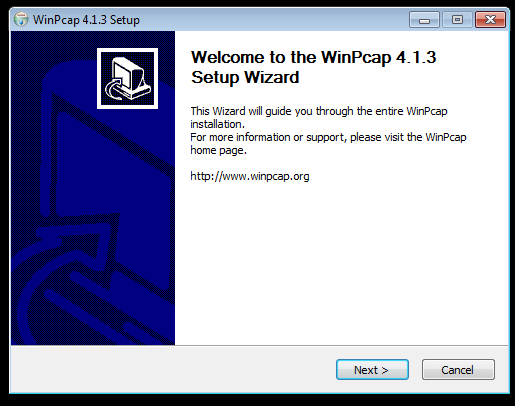
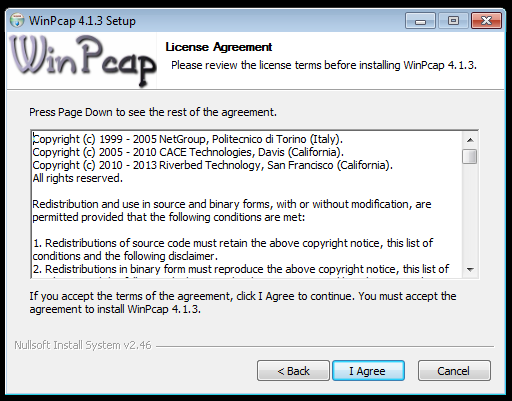
| + | ==Winpcap== | ||
| + | [[Datei:winpcap-windows-1.png]] | ||
| + | [[Datei:winpcap-windows-2.png]] | ||
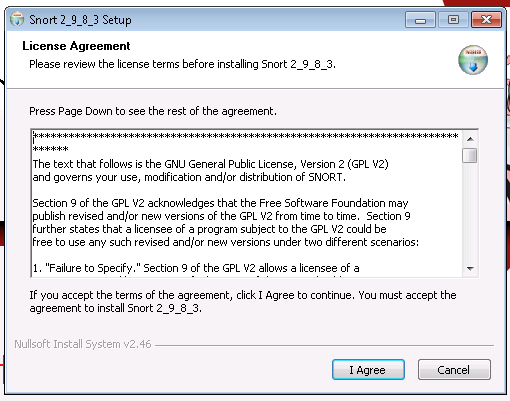
| + | ==Snort== | ||
[[Datei:snort-windows-1.png]] | [[Datei:snort-windows-1.png]] | ||
[[Datei:snort-windows-2.png]] | [[Datei:snort-windows-2.png]] | ||
| + | |||
| + | |||
==Test== | ==Test== | ||
| − | [[ | + | ===Interface Nummer herausfinden=== |
| + | *C:\Snort\bin>snort -W | ||
| + | <pre> | ||
| + | ,,_ -*> Snort! <*- | ||
| + | o" )~ Version 2.9.8.3-WIN32 GRE (Build 383) | ||
| + | '''' By Martin Roesch & The Snort Team: http://www.snort.org/contact#team | ||
| + | Copyright (C) 2014-2015 Cisco and/or its affiliates. All rights reserved. | ||
| + | Copyright (C) 1998-2013 Sourcefire, Inc., et al. | ||
| + | Using PCRE version: 8.10 2010-06-25 | ||
| + | Using ZLIB version: 1.2.3 | ||
| + | |||
| + | Index Physical Address IP Address Device Name Description | ||
| + | ----- ---------------- ---------- ----------- ----------- | ||
| + | 1 08:00:27:5A:CD:4E 0000:0000:fe80:0000:0000:0000:0c88:4afd \Device\ | ||
| + | NPF_{769A54CE-2839-4D39-A753-C36840BB3EB3} Intel(R) PRO/1000 MT-Desktopadap | ||
| + | ter | ||
| + | 2 00:FF:D2:11:5E:C4 0000:0000:fe80:0000:0000:0000:2df0:da06 \Device\ | ||
| + | NPF_{D2115EC4-8770-4D98-83E9-AC63C3480AE6} Sophos SSL VPN Adapter | ||
| + | </pre> | ||
| + | ===Modifzierte snort.conf zu Testzwecken=== | ||
| + | [[Media:snort.conf|snort.conf]] | ||
| + | |||
| + | ===Version anzeigen=== | ||
| + | *C:\snort\bin\snort -V | ||
| + | ===local.rules anlegen=== | ||
| + | C:\snort\rules\local.rules | ||
| + | <pre> | ||
| + | Alert icmp any any -> any any (msg:"Snort Test"; sid:1000000001;) | ||
| + | #Alert udp any any -> any any (msg:"Snort Test UDP"; sid:1000000002;) | ||
| + | #Alert tcp any any -> any any (msg:"Snort Test TCP"; sid:1000000003;) | ||
| + | </pre> | ||
| + | ===Konfiguration testen=== | ||
| + | *C:\snort\bin\snort -i 1 -c c:\Snort\etc\snort.conf -T | ||
| + | |||
| + | ==Snort starten und ping vom 172.18.180.1 auf die 172.18.180.157== | ||
| + | *cd c:\snort\bin | ||
| + | *snort -A console -i 1 -c c:\snort\etc\snort.conf -l c:\snort\log | ||
| + | <pre> | ||
| + | .... | ||
| + | Commencing packet processing (pid=2444) | ||
| + | 08/24-11:33:15.535069 [**] [1:1000000001:0] Snort Test [**] [Priority: 0] {ICMP} 172.18.180.1 -> 172.18.180.157 | ||
| + | 08/24-11:33:15.535451 [**] [1:1000000001:0] Snort Test [**] [Priority: 0] {ICMP} 172.18.180.157 -> 172.18.180.1 | ||
| + | 08/24-11:33:16.536607 [**] [1:1000000001:0] Snort Test [**] [Priority: 0] {ICMP} 172.18.180.1 -> 172.18.180.157 | ||
| + | 08/24-11:33:16.536705 [**] [1:1000000001:0] Snort Test [**] [Priority: 0] {ICMP} 172.18.180.157 -> 172.18.180.1 | ||
| + | 08/24-11:33:17.535307 [**] [1:1000000001:0] Snort Test [**] [Priority: 0] {ICMP} 172.18.180.1 -> 172.18.180.157 | ||
| + | 08/24-11:33:17.535307 [**] [1:1000000001:0] Snort Test [**] [Priority: 0] {ICMP} 172.18.180.157 -> 172.18.180.1 | ||
| + | *** Caught Int-Signal | ||
| + | </pre> | ||
| + | |||
| + | =Snort im Einsatz= | ||
| + | Für den normalen Einsatz sollte man sich auf www.snort.org registieren und die dortigen rules runterladen und einsetzen. Es gibt 3 Varianten: | ||
| + | *Community | ||
| + | *Registered | ||
| + | *Subscription (kostenfplichtig) | ||
| + | Man muss dann in der snort.conf noch die entspechenden rules aktivieren: | ||
| + | <pre> | ||
| + | #include $RULE_PATH/app-detect.rules | ||
| + | #include $RULE_PATH/attack-responses.rules | ||
| + | #include $RULE_PATH/backdoor.rules | ||
| + | #include $RULE_PATH/bad-traffic.rules | ||
| + | #include $RULE_PATH/blacklist.rules | ||
| + | #include $RULE_PATH/botnet-cnc.rules | ||
| + | #include $RULE_PATH/browser-chrome.rules | ||
| + | #include $RULE_PATH/browser-firefox.rules | ||
| + | #include $RULE_PATH/browser-ie.rules | ||
| + | #include $RULE_PATH/browser-other.rules | ||
| + | #include $RULE_PATH/browser-plugins.rules | ||
| + | #include $RULE_PATH/browser-webkit.rules | ||
| + | #include $RULE_PATH/chat.rules | ||
| + | #include $RULE_PATH/content-replace.rules | ||
| + | #include $RULE_PATH/ddos.rules | ||
| + | #include $RULE_PATH/dns.rules | ||
| + | #include $RULE_PATH/dos.rules | ||
| + | #include $RULE_PATH/experimental.rules | ||
| + | #include $RULE_PATH/exploit-kit.rules | ||
| + | #include $RULE_PATH/exploit.rules | ||
| + | #include $RULE_PATH/file-executable.rules | ||
| + | #include $RULE_PATH/file-flash.rules | ||
| + | #include $RULE_PATH/file-identify.rules | ||
| + | #include $RULE_PATH/file-image.rules | ||
| + | #include $RULE_PATH/file-java.rules | ||
| + | #include $RULE_PATH/file-multimedia.rules | ||
| + | #include $RULE_PATH/file-office.rules | ||
| + | #include $RULE_PATH/file-other.rules | ||
| + | #include $RULE_PATH/file-pdf.rules | ||
| + | #include $RULE_PATH/finger.rules | ||
| + | #include $RULE_PATH/ftp.rules | ||
| + | #include $RULE_PATH/icmp-info.rules | ||
| + | #include $RULE_PATH/icmp.rules | ||
| + | #include $RULE_PATH/imap.rules | ||
| + | #include $RULE_PATH/indicator-compromise.rules | ||
| + | #include $RULE_PATH/indicator-obfuscation.rules | ||
| + | #include $RULE_PATH/indicator-scan.rules | ||
| + | #include $RULE_PATH/indicator-shellcode.rules | ||
| + | #include $RULE_PATH/info.rules | ||
| + | #include $RULE_PATH/malware-backdoor.rules | ||
| + | #include $RULE_PATH/malware-cnc.rules | ||
| + | #include $RULE_PATH/malware-other.rules | ||
| + | #include $RULE_PATH/malware-tools.rules | ||
| + | #include $RULE_PATH/misc.rules | ||
| + | #include $RULE_PATH/multimedia.rules | ||
| + | #include $RULE_PATH/mysql.rules | ||
| + | #include $RULE_PATH/netbios.rules | ||
| + | #include $RULE_PATH/nntp.rules | ||
| + | #include $RULE_PATH/oracle.rules | ||
| + | #include $RULE_PATH/os-linux.rules | ||
| + | #include $RULE_PATH/os-mobile.rules | ||
| + | #include $RULE_PATH/os-other.rules | ||
| + | #include $RULE_PATH/os-solaris.rules | ||
| + | #include $RULE_PATH/os-windows.rules | ||
| + | #include $RULE_PATH/other-ids.rules | ||
| + | #include $RULE_PATH/p2p.rules | ||
| + | #include $RULE_PATH/phishing-spam.rules | ||
| + | #include $RULE_PATH/policy-multimedia.rules | ||
| + | #include $RULE_PATH/policy-other.rules | ||
| + | #include $RULE_PATH/policy.rules | ||
| + | #include $RULE_PATH/policy-social.rules | ||
| + | #include $RULE_PATH/policy-spam.rules | ||
| + | #include $RULE_PATH/pop2.rules | ||
| + | #include $RULE_PATH/pop3.rules | ||
| + | #include $RULE_PATH/protocol-dns.rules | ||
| + | #include $RULE_PATH/protocol-finger.rules | ||
| + | #include $RULE_PATH/protocol-ftp.rules | ||
| + | #include $RULE_PATH/protocol-icmp.rules | ||
| + | #include $RULE_PATH/protocol-imap.rules | ||
| + | #include $RULE_PATH/protocol-nntp.rules | ||
| + | #include $RULE_PATH/protocol-pop.rules | ||
| + | #include $RULE_PATH/protocol-rpc.rules | ||
| + | #include $RULE_PATH/protocol-scada.rules | ||
| + | #include $RULE_PATH/protocol-services.rules | ||
| + | #include $RULE_PATH/protocol-snmp.rules | ||
| + | #include $RULE_PATH/protocol-telnet.rules | ||
| + | #include $RULE_PATH/protocol-tftp.rules | ||
| + | #include $RULE_PATH/protocol-voip.rules | ||
| + | #include $RULE_PATH/pua-adware.rules | ||
| + | #include $RULE_PATH/pua-other.rules | ||
| + | #include $RULE_PATH/pua-p2p.rules | ||
| + | #include $RULE_PATH/pua-toolbars.rules | ||
| + | #include $RULE_PATH/rpc.rules | ||
| + | #include $RULE_PATH/rservices.rules | ||
| + | #include $RULE_PATH/scada.rules | ||
| + | #include $RULE_PATH/scan.rules | ||
| + | #include $RULE_PATH/server-apache.rules | ||
| + | #include $RULE_PATH/server-iis.rules | ||
| + | #include $RULE_PATH/server-mail.rules | ||
| + | #include $RULE_PATH/server-mssql.rules | ||
| + | #include $RULE_PATH/server-mysql.rules | ||
| + | #include $RULE_PATH/server-oracle.rules | ||
| + | #include $RULE_PATH/server-other.rules | ||
| + | #include $RULE_PATH/server-samba.rules | ||
| + | #include $RULE_PATH/server-webapp.rules | ||
| + | #include $RULE_PATH/shellcode.rules | ||
| + | #include $RULE_PATH/smtp.rules | ||
| + | #include $RULE_PATH/snmp.rules | ||
| + | #include $RULE_PATH/specific-threats.rules | ||
| + | #include $RULE_PATH/spyware-put.rules | ||
| + | #include $RULE_PATH/sql.rules | ||
| + | #include $RULE_PATH/telnet.rules | ||
| + | #include $RULE_PATH/tftp.rules | ||
| + | #include $RULE_PATH/virus.rules | ||
| + | #include $RULE_PATH/voip.rules | ||
| + | #include $RULE_PATH/web-activex.rules | ||
| + | #include $RULE_PATH/web-attacks.rules | ||
| + | #include $RULE_PATH/web-cgi.rules | ||
| + | #include $RULE_PATH/web-client.rules | ||
| + | #include $RULE_PATH/web-coldfusion.rules | ||
| + | #include $RULE_PATH/web-frontpage.rules | ||
| + | #include $RULE_PATH/web-iis.rules | ||
| + | #include $RULE_PATH/web-misc.rules | ||
| + | #include $RULE_PATH/web-php.rules | ||
| + | #include $RULE_PATH/x11.rules | ||
| + | </pre> | ||
| + | |||
| + | |||
| + | =Links= | ||
| + | *http://www.tecchannel.de/a/netzwerke-wirkungsvoll-absichern,3277633,3 | ||
| + | *http://kailaspatil.blogspot.de/2013/07/tutorial-to-configure-and-use-snort-ids.html | ||
Aktuelle Version vom 24. August 2016, 09:41 Uhr
Download
Install
Winpcap
Snort
Test
Interface Nummer herausfinden
- C:\Snort\bin>snort -W
,,_ -*> Snort! <*-
o" )~ Version 2.9.8.3-WIN32 GRE (Build 383)
'''' By Martin Roesch & The Snort Team: http://www.snort.org/contact#team
Copyright (C) 2014-2015 Cisco and/or its affiliates. All rights reserved.
Copyright (C) 1998-2013 Sourcefire, Inc., et al.
Using PCRE version: 8.10 2010-06-25
Using ZLIB version: 1.2.3
Index Physical Address IP Address Device Name Description
----- ---------------- ---------- ----------- -----------
1 08:00:27:5A:CD:4E 0000:0000:fe80:0000:0000:0000:0c88:4afd \Device\
NPF_{769A54CE-2839-4D39-A753-C36840BB3EB3} Intel(R) PRO/1000 MT-Desktopadap
ter
2 00:FF:D2:11:5E:C4 0000:0000:fe80:0000:0000:0000:2df0:da06 \Device\
NPF_{D2115EC4-8770-4D98-83E9-AC63C3480AE6} Sophos SSL VPN Adapter
Modifzierte snort.conf zu Testzwecken
Version anzeigen
- C:\snort\bin\snort -V
local.rules anlegen
C:\snort\rules\local.rules
Alert icmp any any -> any any (msg:"Snort Test"; sid:1000000001;) #Alert udp any any -> any any (msg:"Snort Test UDP"; sid:1000000002;) #Alert tcp any any -> any any (msg:"Snort Test TCP"; sid:1000000003;)
Konfiguration testen
- C:\snort\bin\snort -i 1 -c c:\Snort\etc\snort.conf -T
Snort starten und ping vom 172.18.180.1 auf die 172.18.180.157
- cd c:\snort\bin
- snort -A console -i 1 -c c:\snort\etc\snort.conf -l c:\snort\log
....
Commencing packet processing (pid=2444)
08/24-11:33:15.535069 [**] [1:1000000001:0] Snort Test [**] [Priority: 0] {ICMP} 172.18.180.1 -> 172.18.180.157
08/24-11:33:15.535451 [**] [1:1000000001:0] Snort Test [**] [Priority: 0] {ICMP} 172.18.180.157 -> 172.18.180.1
08/24-11:33:16.536607 [**] [1:1000000001:0] Snort Test [**] [Priority: 0] {ICMP} 172.18.180.1 -> 172.18.180.157
08/24-11:33:16.536705 [**] [1:1000000001:0] Snort Test [**] [Priority: 0] {ICMP} 172.18.180.157 -> 172.18.180.1
08/24-11:33:17.535307 [**] [1:1000000001:0] Snort Test [**] [Priority: 0] {ICMP} 172.18.180.1 -> 172.18.180.157
08/24-11:33:17.535307 [**] [1:1000000001:0] Snort Test [**] [Priority: 0] {ICMP} 172.18.180.157 -> 172.18.180.1
*** Caught Int-Signal
Snort im Einsatz
Für den normalen Einsatz sollte man sich auf www.snort.org registieren und die dortigen rules runterladen und einsetzen. Es gibt 3 Varianten:
- Community
- Registered
- Subscription (kostenfplichtig)
Man muss dann in der snort.conf noch die entspechenden rules aktivieren:
#include $RULE_PATH/app-detect.rules #include $RULE_PATH/attack-responses.rules #include $RULE_PATH/backdoor.rules #include $RULE_PATH/bad-traffic.rules #include $RULE_PATH/blacklist.rules #include $RULE_PATH/botnet-cnc.rules #include $RULE_PATH/browser-chrome.rules #include $RULE_PATH/browser-firefox.rules #include $RULE_PATH/browser-ie.rules #include $RULE_PATH/browser-other.rules #include $RULE_PATH/browser-plugins.rules #include $RULE_PATH/browser-webkit.rules #include $RULE_PATH/chat.rules #include $RULE_PATH/content-replace.rules #include $RULE_PATH/ddos.rules #include $RULE_PATH/dns.rules #include $RULE_PATH/dos.rules #include $RULE_PATH/experimental.rules #include $RULE_PATH/exploit-kit.rules #include $RULE_PATH/exploit.rules #include $RULE_PATH/file-executable.rules #include $RULE_PATH/file-flash.rules #include $RULE_PATH/file-identify.rules #include $RULE_PATH/file-image.rules #include $RULE_PATH/file-java.rules #include $RULE_PATH/file-multimedia.rules #include $RULE_PATH/file-office.rules #include $RULE_PATH/file-other.rules #include $RULE_PATH/file-pdf.rules #include $RULE_PATH/finger.rules #include $RULE_PATH/ftp.rules #include $RULE_PATH/icmp-info.rules #include $RULE_PATH/icmp.rules #include $RULE_PATH/imap.rules #include $RULE_PATH/indicator-compromise.rules #include $RULE_PATH/indicator-obfuscation.rules #include $RULE_PATH/indicator-scan.rules #include $RULE_PATH/indicator-shellcode.rules #include $RULE_PATH/info.rules #include $RULE_PATH/malware-backdoor.rules #include $RULE_PATH/malware-cnc.rules #include $RULE_PATH/malware-other.rules #include $RULE_PATH/malware-tools.rules #include $RULE_PATH/misc.rules #include $RULE_PATH/multimedia.rules #include $RULE_PATH/mysql.rules #include $RULE_PATH/netbios.rules #include $RULE_PATH/nntp.rules #include $RULE_PATH/oracle.rules #include $RULE_PATH/os-linux.rules #include $RULE_PATH/os-mobile.rules #include $RULE_PATH/os-other.rules #include $RULE_PATH/os-solaris.rules #include $RULE_PATH/os-windows.rules #include $RULE_PATH/other-ids.rules #include $RULE_PATH/p2p.rules #include $RULE_PATH/phishing-spam.rules #include $RULE_PATH/policy-multimedia.rules #include $RULE_PATH/policy-other.rules #include $RULE_PATH/policy.rules #include $RULE_PATH/policy-social.rules #include $RULE_PATH/policy-spam.rules #include $RULE_PATH/pop2.rules #include $RULE_PATH/pop3.rules #include $RULE_PATH/protocol-dns.rules #include $RULE_PATH/protocol-finger.rules #include $RULE_PATH/protocol-ftp.rules #include $RULE_PATH/protocol-icmp.rules #include $RULE_PATH/protocol-imap.rules #include $RULE_PATH/protocol-nntp.rules #include $RULE_PATH/protocol-pop.rules #include $RULE_PATH/protocol-rpc.rules #include $RULE_PATH/protocol-scada.rules #include $RULE_PATH/protocol-services.rules #include $RULE_PATH/protocol-snmp.rules #include $RULE_PATH/protocol-telnet.rules #include $RULE_PATH/protocol-tftp.rules #include $RULE_PATH/protocol-voip.rules #include $RULE_PATH/pua-adware.rules #include $RULE_PATH/pua-other.rules #include $RULE_PATH/pua-p2p.rules #include $RULE_PATH/pua-toolbars.rules #include $RULE_PATH/rpc.rules #include $RULE_PATH/rservices.rules #include $RULE_PATH/scada.rules #include $RULE_PATH/scan.rules #include $RULE_PATH/server-apache.rules #include $RULE_PATH/server-iis.rules #include $RULE_PATH/server-mail.rules #include $RULE_PATH/server-mssql.rules #include $RULE_PATH/server-mysql.rules #include $RULE_PATH/server-oracle.rules #include $RULE_PATH/server-other.rules #include $RULE_PATH/server-samba.rules #include $RULE_PATH/server-webapp.rules #include $RULE_PATH/shellcode.rules #include $RULE_PATH/smtp.rules #include $RULE_PATH/snmp.rules #include $RULE_PATH/specific-threats.rules #include $RULE_PATH/spyware-put.rules #include $RULE_PATH/sql.rules #include $RULE_PATH/telnet.rules #include $RULE_PATH/tftp.rules #include $RULE_PATH/virus.rules #include $RULE_PATH/voip.rules #include $RULE_PATH/web-activex.rules #include $RULE_PATH/web-attacks.rules #include $RULE_PATH/web-cgi.rules #include $RULE_PATH/web-client.rules #include $RULE_PATH/web-coldfusion.rules #include $RULE_PATH/web-frontpage.rules #include $RULE_PATH/web-iis.rules #include $RULE_PATH/web-misc.rules #include $RULE_PATH/web-php.rules #include $RULE_PATH/x11.rules