Nftables Firewall Basis Konfiguration: Unterschied zwischen den Versionen
Zur Navigation springen
Zur Suche springen
| (42 dazwischenliegende Versionen von einem anderen Benutzer werden nicht angezeigt) | |||
| Zeile 1: | Zeile 1: | ||
=Die Basis Konfiguration= | =Die Basis Konfiguration= | ||
*Die Basiskonfiguration besagt das von der Firewall nach aussen alles erlaubt ist. | *Die Basiskonfiguration besagt das von der Firewall nach aussen alles erlaubt ist. | ||
| − | * | + | *Das Loopbackinterface schalten frei um den localen Netwerkverkehr zu ermöglichen. |
| + | *Wir schalten hier auch noch den 22 Zugang frei. | ||
#!/usr/sbin/nft -f | #!/usr/sbin/nft -f | ||
flush ruleset | flush ruleset | ||
define local_tcp_ports = { 22 } | define local_tcp_ports = { 22 } | ||
| − | + | ||
table inet filter { | table inet filter { | ||
chain input { | chain input { | ||
| Zeile 13: | Zeile 14: | ||
'''ct state new tcp dport $local_tcp_ports accept''' | '''ct state new tcp dport $local_tcp_ports accept''' | ||
} | } | ||
| − | + | ||
chain forward { | chain forward { | ||
type filter hook forward priority filter; policy drop; | type filter hook forward priority filter; policy drop; | ||
| Zeile 23: | Zeile 24: | ||
'''ct state new accept''' | '''ct state new accept''' | ||
} | } | ||
| + | |||
| + | } | ||
| + | =Weiter gehts= | ||
| + | *Wir schalten die lokalen Netze gegenseitig frei. | ||
| + | *So wie auch den Zugriff auf unsere Firewall | ||
| + | *In der Praxis sollte man das genau überlegen. | ||
| + | *Für unsere Übung ist das aber ok. | ||
| + | #!/usr/sbin/nft -f | ||
| + | flush ruleset | ||
| + | define local_tcp_ports = { 22 } | ||
| + | '''define save_interfaces = { enp0s8, enp0s9, enp0s10 }''' | ||
| + | table inet filter { | ||
| + | chain input { | ||
| + | type filter hook input priority filter; policy drop; | ||
| + | ct state established,related accept | ||
| + | ct state new iif "lo" accept | ||
| + | ct state new tcp dport $local_tcp_ports accept | ||
| + | '''ct state new iif $save_interfaces accept''' | ||
| + | } | ||
| + | |||
| + | chain forward { | ||
| + | type filter hook forward priority filter; policy drop; | ||
| + | ct state established,related accept | ||
| + | '''ct state new iif $save_interfaces accept''' | ||
| + | } | ||
| + | chain output { | ||
| + | type filter hook output priority filter; policy drop; | ||
| + | ct state established,related accept | ||
| + | ct state new accept | ||
| + | } | ||
| + | |||
} | } | ||
| + | =Das Logging= | ||
| + | *Kurz vor dem erreichen der Default Policy wird geloggt | ||
| + | #!/usr/sbin/nft -f | ||
| + | flush ruleset | ||
| + | define local_tcp_ports = { 22 } | ||
| + | define save_interfaces = { enp0s8, enp0s9, enp0s10 } | ||
| + | table inet filter { | ||
| + | chain input { | ||
| + | type filter hook input priority filter; policy drop; | ||
| + | ct state established,related accept | ||
| + | ct state new iif "lo" accept | ||
| + | ct state new tcp dport $local_tcp_ports accept | ||
| + | ct state new iif $save_interfaces accept | ||
| + | '''log prefix "--nftables-drop-input--"''' | ||
| + | } | ||
| + | |||
| + | chain forward { | ||
| + | type filter hook forward priority filter; policy drop; | ||
| + | ct state established,related accept | ||
| + | ct state new iif $save_interfaces accept | ||
| + | '''log prefix "--nftables-drop-forward--"''' | ||
| + | } | ||
| + | chain output { | ||
| + | type filter hook output priority filter; policy drop; | ||
| + | ct state established,related accept | ||
| + | ct state new accept | ||
| + | '''log prefix "--nftables-drop-output--"''' | ||
| + | } | ||
| + | |||
| + | } | ||
| + | ==Logging in einer separate Datei== | ||
| + | *[[Rsyslog firewall Regel]] | ||
| + | |||
| + | ==Wir gucken== | ||
| + | *tail -f /var/log/syslog | grep nft | ||
| + | Feb 28 17:30:09 firewall kernel: [ 2119.005002] --nftables-drop-input--IN=enp0s9 OUT= MAC=08:00:27:08:29:61:08:00:27:47:d1:33:08:00 SRC=172.16.100.151 DST=172.16.100.1 LEN=356 TOS=0x10 PREC=0xC0 TTL=64 ID=35132 PROTO=ICMP TYPE=3 CODE=3 [SRC=172.16.100.1 DST=172.16.100.151 LEN=328 TOS=0x10 PREC=0x00 TTL=128 ID=0 PROTO=UDP SPT=67 DPT=68 LEN=308 ] | ||
| + | |||
| + | =Wir Snaten= | ||
| + | *[[Arten von NAT]] | ||
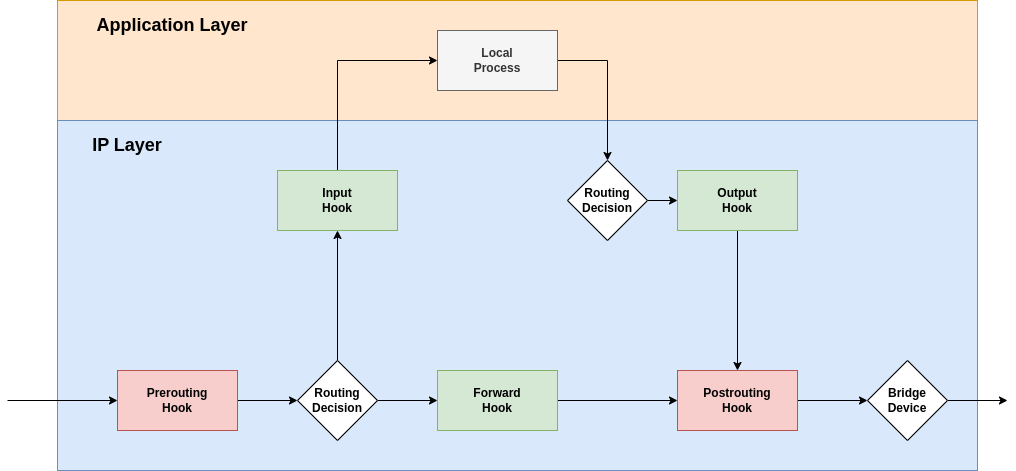
| + | {{#drawio:nft-inet1}} | ||
| + | *Wir müssen hier eine neue Tabelle anlegen | ||
| + | *Snat gehört zur nat-Tabelle | ||
| + | *Wir müssen das Paket verändern kurz vor dem verlassen des Rechners | ||
| + | *Der richtige Ort ist der postrouting Haken | ||
| + | #!/usr/sbin/nft -f | ||
| + | flush ruleset | ||
| + | define local_tcp_ports = { 22 } | ||
| + | define save_interfaces = { enp0s8, enp0s9, enp0s10 } | ||
| + | '''define wandev = enp0s3''' | ||
| + | '''define wanip = 192.168.6.100''' | ||
| + | '''define lan-nets = { 172.16.100.0/24 , 172.17.100.0/24 }''' | ||
| + | table inet filter { | ||
| + | chain input { | ||
| + | type filter hook input priority filter; policy drop; | ||
| + | ct state established,related accept | ||
| + | ct state new iif "lo" accept | ||
| + | ct state new tcp dport $local_tcp_ports accept | ||
| + | ct state new iif $save_interfaces accept | ||
| + | log prefix "--nftables-drop-input--" | ||
| + | } | ||
| + | |||
| + | chain forward { | ||
| + | type filter hook forward priority filter; policy drop; | ||
| + | ct state established,related accept | ||
| + | ct state new iif $save_interfaces accept | ||
| + | log prefix "--nftables-drop-forward--" | ||
| + | } | ||
| + | chain output { | ||
| + | type filter hook output priority filter; policy drop; | ||
| + | ct state established,related accept | ||
| + | ct state new accept | ||
| + | log prefix "--nftables-drop-output--" | ||
| + | } | ||
| + | |||
| + | } | ||
| + | '''table inet nat {''' | ||
| + | '''chain postrouting {''' | ||
| + | '''type nat hook postrouting priority srcnat; policy accept;''' | ||
| + | '''oif $wandev ip saddr $lan-nets snat ip to $wanip''' | ||
| + | '''}''' | ||
| + | '''}''' | ||
| + | |||
| + | =Der Counter= | ||
| + | *Man kann auch Counter einbauen. | ||
| + | *Diese sind im Vorgänger iptables automatisch dabei | ||
| + | *Es werden Pakete und Bytes gezählt. | ||
| + | <pre> | ||
| + | #!/usr/sbin/nft -f | ||
| + | flush ruleset | ||
| + | define local_tcp_ports = { 22 } | ||
| + | define save_interfaces = { enp0s8, enp0s9, enp0s10 } | ||
| + | define wandev = enp0s3 | ||
| + | define wanip = 192.168.6.100 | ||
| + | define lan-nets = { 172.16.100.0/24 , 172.17.100.0/24 } | ||
| + | table inet filter { | ||
| + | chain input { | ||
| + | type filter hook input priority filter; policy drop; | ||
| + | ct state established,related counter accept | ||
| + | ct state new iif "lo" counter accept | ||
| + | ct state new tcp dport $local_tcp_ports counter accept | ||
| + | ct state new iif $save_interfaces counter accept | ||
| + | log prefix "--nftables-drop-input--" | ||
| + | } | ||
| + | |||
| + | chain forward { | ||
| + | type filter hook forward priority filter; policy drop; | ||
| + | ct state established,related counter accept | ||
| + | ct state new iif $save_interfaces counter accept | ||
| + | log prefix "--nftables-drop-forward--" | ||
| + | } | ||
| + | chain output { | ||
| + | type filter hook output priority filter; policy drop; | ||
| + | ct state established,related counter accept | ||
| + | ct state new counter accept | ||
| + | log prefix "--nftables-drop-output--" | ||
| + | } | ||
| + | |||
| + | } | ||
| + | table inet nat { | ||
| + | chain postrouting { | ||
| + | type nat hook postrouting priority srcnat; policy accept; | ||
| + | oif $wandev ip saddr $lan-nets counter snat ip to $wanip | ||
| + | } | ||
| + | } | ||
| + | </pre> | ||
| + | |||
| + | =Frage= | ||
| + | *Wieso geht ein '''ssh server''' aber kein '''ssh ns'''? | ||
| + | =Forwarding= | ||
| + | *Wir schalten nun die Nameserver Ports als auch den SSH Zugang frei | ||
| + | *DNS arbeitet sowohl auf tcp und udp | ||
| + | *Des weiteren lassen wir einen ping zu. | ||
| + | |||
| + | #!/usr/sbin/nft -f | ||
| + | flush ruleset | ||
| + | define local_tcp_ports = { 22 } | ||
| + | define save_interfaces = { enp0s8, enp0s9, enp0s10 } | ||
| + | define wandev = enp0s3 | ||
| + | define wanip = 192.168.6.100 | ||
| + | define ns = 10.88.100.21 | ||
| + | '''define ns-tcp-ports = { 22, 53 }''' | ||
| + | '''define ns-udp-ports = { 53 }''' | ||
| + | '''define dmzdev = enp0s8''' | ||
| + | |||
| + | define lan-nets = { 172.16.100.0/24 , 172.17.100.0/24 } | ||
| + | table inet filter { | ||
| + | chain input { | ||
| + | type filter hook input priority filter; policy drop; | ||
| + | ct state established,related counter accept | ||
| + | ct state new iif "lo" counter accept | ||
| + | ct state new tcp dport $local_tcp_ports counter accept | ||
| + | ct state new iif $save_interfaces counter accept | ||
| + | log prefix "--nftables-drop-input--" | ||
| + | } | ||
| + | |||
| + | chain forward { | ||
| + | type filter hook forward priority filter; policy drop; | ||
| + | ct state established,related counter accept | ||
| + | ct state new iif $save_interfaces counter accept | ||
| + | '''ct state new iif $wandev oif $dmzdev ip daddr $ns tcp dport $ns-tcp-ports counter accept''' | ||
| + | '''ct state new iif $wandev oif $dmzdev ip daddr $ns udp dport $ns-udp-ports counter accept''' | ||
| + | '''ct state new iif $wandev oif $dmzdev ip daddr $ns icmp type echo-request counter accept''' | ||
| + | log prefix "--nftables-drop-forward--" | ||
| + | } | ||
| + | chain output { | ||
| + | type filter hook output priority filter; policy drop; | ||
| + | ct state established,related counter accept | ||
| + | ct state new counter accept | ||
| + | log prefix "--nftables-drop-output--" | ||
| + | } | ||
| + | |||
| + | } | ||
| + | table inet nat { | ||
| + | chain postrouting { | ||
| + | type nat hook postrouting priority srcnat; policy accept; | ||
| + | oif $wandev ip saddr $lan-nets counter snat ip to $wanip | ||
| + | } | ||
| + | } | ||
| + | |||
| + | =Die fehlende Kette= | ||
| + | *Um die Ketten im Schaubild zu kompletieren verbinden wir uns noch mit dem Prerouting Haken. | ||
| + | *Dort werden die Pakete '''gednattet''' :-) | ||
| + | *Regeln legen wir keine an. | ||
| + | |||
| + | #!/usr/sbin/nft -f | ||
| + | flush ruleset | ||
| + | define local_tcp_ports = { 22 } | ||
| + | define save_interfaces = { enp0s8, enp0s9, enp0s10 } | ||
| + | define wandev = enp0s3 | ||
| + | define wanip = 192.168.6.100 | ||
| + | define ns = 10.88.100.21 | ||
| + | define ns-tcp-ports = { 22, 53 } | ||
| + | define ns-udp-ports = { 53 } | ||
| + | define dmzdev = enp0s8 | ||
| + | |||
| + | define lan-nets = { 172.16.100.0/24 , 172.17.100.0/24 } | ||
| + | table inet filter { | ||
| + | chain input { | ||
| + | type filter hook input priority filter; policy drop; | ||
| + | ct state established,related counter accept | ||
| + | ct state new iif "lo" counter accept | ||
| + | ct state new tcp dport $local_tcp_ports counter accept | ||
| + | ct state new iif $save_interfaces counter accept | ||
| + | log prefix "--nftables-drop-input--" | ||
| + | } | ||
| + | |||
| + | chain forward { | ||
| + | type filter hook forward priority filter; policy drop; | ||
| + | ct state established,related counter accept | ||
| + | ct state new iif $save_interfaces counter accept | ||
| + | ct state new iif $wandev oif $dmzdev ip daddr $ns tcp dport $ns-tcp-ports counter accept | ||
| + | ct state new iif $wandev oif $dmzdev ip daddr $ns udp dport $ns-udp-ports counter accept | ||
| + | ct state new iif $wandev oif $dmzdev ip daddr $ns icmp type echo-request counter accept | ||
| + | |||
| + | log prefix "--nftables-drop-forward--" | ||
| + | } | ||
| + | chain output { | ||
| + | type filter hook output priority filter; policy drop; | ||
| + | ct state established,related counter accept | ||
| + | ct state new counter accept | ||
| + | log prefix "--nftables-drop-output--" | ||
| + | } | ||
| + | |||
| + | } | ||
| + | '''table inet nat {''' | ||
| + | '''chain prerouting {''' | ||
| + | '''type nat hook prerouting priority dstnat; policy accept;''' | ||
| + | '''}''' | ||
| + | chain postrouting { | ||
| + | type nat hook postrouting priority srcnat; policy accept; | ||
| + | oif $wandev ip saddr $lan-nets counter snat ip to $wanip | ||
| + | } | ||
| + | } | ||
| + | =Einbinden in systemd= | ||
| + | ;Dies ist sehr einfach, da es schon eine Unit Datei gibt. | ||
| + | ;Es reicht ein: | ||
| + | *systemctl enable nftables.service | ||
| + | |||
| + | =Aufgaben= | ||
| + | *Installieren sie einen debian Rechner in der dmz | ||
| + | *Er sollte die IP 10.88.X.33/24 | ||
| + | *Der Name sollte debian.itX.int lauten | ||
| + | *Die restlichen Daten sollten bekannt sein. | ||
| + | *Vorm installieren ein Reboot | ||
| + | *Installieren sie hier folgende Pakete | ||
| + | *apache2 dovecot-imapd postfix (Bei Fragen, alles mit yes beantworten) | ||
| + | *Welche ipv4 Ports sind nun geöffnet? | ||
| + | *Schalten sie diese aut der firewall frei. | ||
| + | *Schalten sie zusätzlich auch noch icmp echo-requests frei. | ||
| + | *Testen sie mit nmap. (Wenn icmp abgeschaltet ist bitte Option -Pn nutzen) | ||
| + | |||
| + | =Zusatzaufgabe= | ||
| + | *Installieren sie auf dem Rechner debian dovecot-pop3d | ||
| + | *Welche zusätzlichen Ports sind offen? | ||
| + | *Schalten sie diese in der Firewall frei. | ||
| + | *nmap Test von hostX | ||
| + | *Bringen sie ihre ssh-pub-keys von hostX auf den Rechner debian. | ||
| + | *Installieren sie diese für root und xinux, so das man sich passwortlos anmelden kann- | ||
Aktuelle Version vom 19. April 2023, 14:10 Uhr
Die Basis Konfiguration
- Die Basiskonfiguration besagt das von der Firewall nach aussen alles erlaubt ist.
- Das Loopbackinterface schalten frei um den localen Netwerkverkehr zu ermöglichen.
- Wir schalten hier auch noch den 22 Zugang frei.
#!/usr/sbin/nft -f
flush ruleset
define local_tcp_ports = { 22 }
table inet filter {
chain input {
type filter hook input priority filter; policy drop;
ct state established,related accept
ct state new iif "lo" accept
ct state new tcp dport $local_tcp_ports accept
}
chain forward {
type filter hook forward priority filter; policy drop;
ct state established,related accept
}
chain output {
type filter hook output priority filter; policy drop;
ct state established,related accept
ct state new accept
}
}
Weiter gehts
- Wir schalten die lokalen Netze gegenseitig frei.
- So wie auch den Zugriff auf unsere Firewall
- In der Praxis sollte man das genau überlegen.
- Für unsere Übung ist das aber ok.
#!/usr/sbin/nft -f
flush ruleset
define local_tcp_ports = { 22 }
define save_interfaces = { enp0s8, enp0s9, enp0s10 }
table inet filter {
chain input {
type filter hook input priority filter; policy drop;
ct state established,related accept
ct state new iif "lo" accept
ct state new tcp dport $local_tcp_ports accept
ct state new iif $save_interfaces accept
}
chain forward {
type filter hook forward priority filter; policy drop;
ct state established,related accept
ct state new iif $save_interfaces accept
}
chain output {
type filter hook output priority filter; policy drop;
ct state established,related accept
ct state new accept
}
}
Das Logging
- Kurz vor dem erreichen der Default Policy wird geloggt
#!/usr/sbin/nft -f
flush ruleset
define local_tcp_ports = { 22 }
define save_interfaces = { enp0s8, enp0s9, enp0s10 }
table inet filter {
chain input {
type filter hook input priority filter; policy drop;
ct state established,related accept
ct state new iif "lo" accept
ct state new tcp dport $local_tcp_ports accept
ct state new iif $save_interfaces accept
log prefix "--nftables-drop-input--"
}
chain forward {
type filter hook forward priority filter; policy drop;
ct state established,related accept
ct state new iif $save_interfaces accept
log prefix "--nftables-drop-forward--"
}
chain output {
type filter hook output priority filter; policy drop;
ct state established,related accept
ct state new accept
log prefix "--nftables-drop-output--"
}
}
Logging in einer separate Datei
Wir gucken
- tail -f /var/log/syslog | grep nft
Feb 28 17:30:09 firewall kernel: [ 2119.005002] --nftables-drop-input--IN=enp0s9 OUT= MAC=08:00:27:08:29:61:08:00:27:47:d1:33:08:00 SRC=172.16.100.151 DST=172.16.100.1 LEN=356 TOS=0x10 PREC=0xC0 TTL=64 ID=35132 PROTO=ICMP TYPE=3 CODE=3 [SRC=172.16.100.1 DST=172.16.100.151 LEN=328 TOS=0x10 PREC=0x00 TTL=128 ID=0 PROTO=UDP SPT=67 DPT=68 LEN=308 ]
Wir Snaten
- Wir müssen hier eine neue Tabelle anlegen
- Snat gehört zur nat-Tabelle
- Wir müssen das Paket verändern kurz vor dem verlassen des Rechners
- Der richtige Ort ist der postrouting Haken
#!/usr/sbin/nft -f
flush ruleset
define local_tcp_ports = { 22 }
define save_interfaces = { enp0s8, enp0s9, enp0s10 }
define wandev = enp0s3
define wanip = 192.168.6.100
define lan-nets = { 172.16.100.0/24 , 172.17.100.0/24 }
table inet filter {
chain input {
type filter hook input priority filter; policy drop;
ct state established,related accept
ct state new iif "lo" accept
ct state new tcp dport $local_tcp_ports accept
ct state new iif $save_interfaces accept
log prefix "--nftables-drop-input--"
}
chain forward {
type filter hook forward priority filter; policy drop;
ct state established,related accept
ct state new iif $save_interfaces accept
log prefix "--nftables-drop-forward--"
}
chain output {
type filter hook output priority filter; policy drop;
ct state established,related accept
ct state new accept
log prefix "--nftables-drop-output--"
}
}
table inet nat {
chain postrouting {
type nat hook postrouting priority srcnat; policy accept;
oif $wandev ip saddr $lan-nets snat ip to $wanip
}
}
Der Counter
- Man kann auch Counter einbauen.
- Diese sind im Vorgänger iptables automatisch dabei
- Es werden Pakete und Bytes gezählt.
#!/usr/sbin/nft -f
flush ruleset
define local_tcp_ports = { 22 }
define save_interfaces = { enp0s8, enp0s9, enp0s10 }
define wandev = enp0s3
define wanip = 192.168.6.100
define lan-nets = { 172.16.100.0/24 , 172.17.100.0/24 }
table inet filter {
chain input {
type filter hook input priority filter; policy drop;
ct state established,related counter accept
ct state new iif "lo" counter accept
ct state new tcp dport $local_tcp_ports counter accept
ct state new iif $save_interfaces counter accept
log prefix "--nftables-drop-input--"
}
chain forward {
type filter hook forward priority filter; policy drop;
ct state established,related counter accept
ct state new iif $save_interfaces counter accept
log prefix "--nftables-drop-forward--"
}
chain output {
type filter hook output priority filter; policy drop;
ct state established,related counter accept
ct state new counter accept
log prefix "--nftables-drop-output--"
}
}
table inet nat {
chain postrouting {
type nat hook postrouting priority srcnat; policy accept;
oif $wandev ip saddr $lan-nets counter snat ip to $wanip
}
}
Frage
- Wieso geht ein ssh server aber kein ssh ns?
Forwarding
- Wir schalten nun die Nameserver Ports als auch den SSH Zugang frei
- DNS arbeitet sowohl auf tcp und udp
- Des weiteren lassen wir einen ping zu.
#!/usr/sbin/nft -f
flush ruleset
define local_tcp_ports = { 22 }
define save_interfaces = { enp0s8, enp0s9, enp0s10 }
define wandev = enp0s3
define wanip = 192.168.6.100
define ns = 10.88.100.21
define ns-tcp-ports = { 22, 53 }
define ns-udp-ports = { 53 }
define dmzdev = enp0s8
define lan-nets = { 172.16.100.0/24 , 172.17.100.0/24 }
table inet filter {
chain input {
type filter hook input priority filter; policy drop;
ct state established,related counter accept
ct state new iif "lo" counter accept
ct state new tcp dport $local_tcp_ports counter accept
ct state new iif $save_interfaces counter accept
log prefix "--nftables-drop-input--"
}
chain forward {
type filter hook forward priority filter; policy drop;
ct state established,related counter accept
ct state new iif $save_interfaces counter accept
ct state new iif $wandev oif $dmzdev ip daddr $ns tcp dport $ns-tcp-ports counter accept
ct state new iif $wandev oif $dmzdev ip daddr $ns udp dport $ns-udp-ports counter accept
ct state new iif $wandev oif $dmzdev ip daddr $ns icmp type echo-request counter accept
log prefix "--nftables-drop-forward--"
}
chain output {
type filter hook output priority filter; policy drop;
ct state established,related counter accept
ct state new counter accept
log prefix "--nftables-drop-output--"
}
}
table inet nat {
chain postrouting {
type nat hook postrouting priority srcnat; policy accept;
oif $wandev ip saddr $lan-nets counter snat ip to $wanip
}
}
Die fehlende Kette
- Um die Ketten im Schaubild zu kompletieren verbinden wir uns noch mit dem Prerouting Haken.
- Dort werden die Pakete gednattet :-)
- Regeln legen wir keine an.
#!/usr/sbin/nft -f
flush ruleset
define local_tcp_ports = { 22 }
define save_interfaces = { enp0s8, enp0s9, enp0s10 }
define wandev = enp0s3
define wanip = 192.168.6.100
define ns = 10.88.100.21
define ns-tcp-ports = { 22, 53 }
define ns-udp-ports = { 53 }
define dmzdev = enp0s8
define lan-nets = { 172.16.100.0/24 , 172.17.100.0/24 }
table inet filter {
chain input {
type filter hook input priority filter; policy drop;
ct state established,related counter accept
ct state new iif "lo" counter accept
ct state new tcp dport $local_tcp_ports counter accept
ct state new iif $save_interfaces counter accept
log prefix "--nftables-drop-input--"
}
chain forward {
type filter hook forward priority filter; policy drop;
ct state established,related counter accept
ct state new iif $save_interfaces counter accept
ct state new iif $wandev oif $dmzdev ip daddr $ns tcp dport $ns-tcp-ports counter accept
ct state new iif $wandev oif $dmzdev ip daddr $ns udp dport $ns-udp-ports counter accept
ct state new iif $wandev oif $dmzdev ip daddr $ns icmp type echo-request counter accept
log prefix "--nftables-drop-forward--"
}
chain output {
type filter hook output priority filter; policy drop;
ct state established,related counter accept
ct state new counter accept
log prefix "--nftables-drop-output--"
}
}
table inet nat {
chain prerouting {
type nat hook prerouting priority dstnat; policy accept;
}
chain postrouting {
type nat hook postrouting priority srcnat; policy accept;
oif $wandev ip saddr $lan-nets counter snat ip to $wanip
}
}
Einbinden in systemd
- Dies ist sehr einfach, da es schon eine Unit Datei gibt.
- Es reicht ein
- systemctl enable nftables.service
Aufgaben
- Installieren sie einen debian Rechner in der dmz
- Er sollte die IP 10.88.X.33/24
- Der Name sollte debian.itX.int lauten
- Die restlichen Daten sollten bekannt sein.
- Vorm installieren ein Reboot
- Installieren sie hier folgende Pakete
- apache2 dovecot-imapd postfix (Bei Fragen, alles mit yes beantworten)
- Welche ipv4 Ports sind nun geöffnet?
- Schalten sie diese aut der firewall frei.
- Schalten sie zusätzlich auch noch icmp echo-requests frei.
- Testen sie mit nmap. (Wenn icmp abgeschaltet ist bitte Option -Pn nutzen)
Zusatzaufgabe
- Installieren sie auf dem Rechner debian dovecot-pop3d
- Welche zusätzlichen Ports sind offen?
- Schalten sie diese in der Firewall frei.
- nmap Test von hostX
- Bringen sie ihre ssh-pub-keys von hostX auf den Rechner debian.
- Installieren sie diese für root und xinux, so das man sich passwortlos anmelden kann-