Wazuh IDS an einem Switch: Unterschied zwischen den Versionen
Zur Navigation springen
Zur Suche springen
| (36 dazwischenliegende Versionen desselben Benutzers werden nicht angezeigt) | |||
| Zeile 1: | Zeile 1: | ||
=Aufbau= | =Aufbau= | ||
{{#drawio:isd-switch}} | {{#drawio:isd-switch}} | ||
| + | =Sniffing Schnittstelle anfügen= | ||
| + | *vi /etc/network/interfaces | ||
| + | |||
| + | auto enp0s8 | ||
| + | iface enp0s8 inet manual | ||
| + | post-up ip link set enp0s8 promisc on | ||
| + | |||
=Suricata= | =Suricata= | ||
==Installation== | ==Installation== | ||
*apt update | *apt update | ||
*apt install -y suricata | *apt install -y suricata | ||
| + | ==Minimal Konfiguration== | ||
| + | ===Konfigfile=== | ||
| + | *cat /etc/suricata/suricata.yaml | ||
| + | <pre> | ||
| + | %YAML 1.1 | ||
| + | --- | ||
| + | # Standard-Log-Verzeichnis | ||
| + | default-log-dir: /var/log/suricata/ | ||
| + | |||
| + | # Statistiken aktivieren | ||
| + | stats: | ||
| + | enabled: yes | ||
| + | interval: 8 | ||
| + | |||
| + | # Ausgaben konfigurieren | ||
| + | outputs: | ||
| + | - fast: | ||
| + | enabled: yes | ||
| + | filename: fast.log | ||
| + | append: yes | ||
| + | - alert-debug: | ||
| + | enabled: yes | ||
| + | filename: alert-debug.log | ||
| + | append: yes | ||
| + | - stats: | ||
| + | enabled: yes | ||
| + | filename: stats.log | ||
| + | append: yes | ||
| + | totals: yes | ||
| + | threads: no | ||
| + | |||
| + | # Logging-Einstellungen | ||
| + | logging: | ||
| + | default-log-level: notice | ||
| + | outputs: | ||
| + | - console: | ||
| + | enabled: yes | ||
| + | - file: | ||
| + | enabled: yes | ||
| + | level: info | ||
| + | filename: suricata.log | ||
| + | |||
| + | # Netzwerkschnittstelle für Mirror-Port konfigurieren | ||
| + | af-packet: | ||
| + | - interface: enp0s8 | ||
| + | threads: auto | ||
| + | cluster-id: 99 | ||
| + | cluster-type: cluster_flow | ||
| + | defrag: yes | ||
| + | use-mmap: yes | ||
| + | ring-size: 2048 | ||
| + | buffer-size: 65535 | ||
| + | mmap-locked: yes | ||
| + | tpacket-v3: yes | ||
| + | checksum-checks: no | ||
| + | |||
| + | # Alternativ PCAP-Modus (wenn AF_PACKET nicht genutzt wird) | ||
| + | pcap: | ||
| + | - interface: enp0s8 | ||
| + | buffer-size: 65535 | ||
| + | checksum-checks: no | ||
| + | |||
| + | # PID-Datei | ||
| + | pid-file: /var/run/suricata.pid | ||
| + | |||
| + | # Coredump-Einstellungen | ||
| + | coredump: | ||
| + | max-dump: unlimited | ||
| + | |||
| + | # Host-Modus | ||
| + | host-mode: auto | ||
| + | |||
| + | # Unix-Befehlseingabe konfigurieren | ||
| + | unix-command: | ||
| + | enabled: yes | ||
| + | filename: /var/run/suricata-command.socket | ||
| + | |||
| + | # Engine-Analyse-Einstellungen | ||
| + | engine-analysis: | ||
| + | rules-fast-pattern: yes | ||
| + | rules: yes | ||
| + | |||
| + | # Defragmentierungseinstellungen | ||
| + | defrag: | ||
| + | memcap: 32mb | ||
| + | hash-size: 65536 | ||
| + | trackers: 65535 | ||
| + | max-frags: 65535 | ||
| + | prealloc: yes | ||
| + | timeout: 60 | ||
| + | |||
| + | # Standardregelverzeichnis | ||
| + | default-rule-path: /etc/suricata/rules | ||
| + | |||
| + | # Regel-Dateien | ||
| + | rule-files: | ||
| + | - local.rules | ||
| + | |||
| + | # Klassifikationsdatei | ||
| + | classification-file: /etc/suricata/classification.config | ||
| + | |||
| + | # Referenzkonfigurationsdatei | ||
| + | reference-config-file: /etc/suricata/reference.config | ||
| + | app-layer: | ||
| + | protocols: | ||
| + | http: | ||
| + | enabled: yes | ||
| + | tls: | ||
| + | enabled: yes | ||
| + | dcerpc: | ||
| + | enabled: yes | ||
| + | smb: | ||
| + | enabled: yes | ||
| + | ftp: | ||
| + | enabled: yes | ||
| + | ssh: | ||
| + | enabled: yes | ||
| + | smtp: | ||
| + | enabled: yes | ||
| + | dns: | ||
| + | enabled: yes | ||
| + | modbus: | ||
| + | enabled: yes | ||
| + | enip: | ||
| + | enabled: yes | ||
| + | dnp3: | ||
| + | enabled: yes | ||
| + | nfs: | ||
| + | enabled: yes | ||
| + | ntp: | ||
| + | enabled: yes | ||
| + | tftp: | ||
| + | enabled: yes | ||
| + | ikev2: | ||
| + | enabled: yes | ||
| + | krb5: | ||
| + | enabled: yes | ||
| + | dhcp: | ||
| + | enabled: yes | ||
| + | snmp: | ||
| + | enabled: yes | ||
| + | sip: | ||
| + | enabled: yes | ||
| + | rfb: | ||
| + | enabled: yes | ||
| + | mqtt: | ||
| + | enabled: yes | ||
| + | rdp: | ||
| + | enabled: yes | ||
| + | http2: | ||
| + | enabled: yes | ||
| + | imap: | ||
| + | enabled: yes | ||
| + | </pre> | ||
| + | ===Eigene Regeln=== | ||
| + | *cat /etc/suricata/rules/local.rules | ||
| + | alert icmp any any -> any any (msg:"ICMP Test"; flow:to_server; sid:1;) | ||
| + | alert tcp any any -> any any (flags: S; msg: "SYN packet"; sid:2;) | ||
| + | |||
| + | ==Test== | ||
| + | *suricata -T -c /etc/suricata/suricata.yaml | ||
| + | 26/2/2025 -- 09:39:13 - <Info> - Running suricata under test mode | ||
| + | 26/2/2025 -- 09:39:13 - <Notice> - This is Suricata version 6.0.10 RELEASE running in SYSTEM mode | ||
| + | 26/2/2025 -- 09:39:13 - <Notice> - Configuration provided was successfully loaded. Exiting. | ||
| + | ==Erster Start== | ||
| + | ;Vordergrund | ||
| + | suricata -c /etc/suricata/suricata.yaml --af-packet | ||
| + | ;Hintergrund | ||
| + | suricata -c /etc/suricata/suricata.yaml --af-packet -D | ||
| + | |||
| + | =Wazuh= | ||
| + | ==Installation== | ||
| + | *[[Wazuh Installation]] | ||
| + | ==Anpassen von Suricata== | ||
| + | *Nachdem Wazuh läuft, muss Suricata so konfiguriert werden, dass es die Logs an Wazuh sendet. | ||
| + | *Suricata-Logging anpassen Öffne die suricata.yaml und stelle sicher, dass die JSON-Logs aktiviert sind: | ||
| + | *vi /etc/suricata/suricata.yaml | ||
| + | outputs: | ||
| + | ... | ||
| + | - eve-log: | ||
| + | enabled: yes | ||
| + | filetype: regular | ||
| + | filename: /var/log/suricata/eve.json | ||
| + | types: | ||
| + | - alert | ||
| + | - anomaly | ||
| + | - dns | ||
| + | - tls | ||
| + | - http | ||
| + | - ssh | ||
| + | - smtp | ||
| + | ;Runterfahren | ||
| + | *suricatasc -c shutdown | ||
| + | ;Neustarten | ||
| + | *suricata -c /etc/suricata/suricata.yaml --af-packet -D | ||
| + | ;Kontrolle ob etwas geloggt wird | ||
| + | tail -f /var/log/suricata/eve.json | ||
| + | <pre> | ||
| + | {"timestamp":"2025-02- 26T10:48:17.825694+0100","flow_id":1157424342247926,"in_iface":"enp0s8","event_type":"alert","src_ip":"192.168.1.98","src_port":0,"dest_ip":"8.8.8.8","dest_port":0,"proto":"ICMP","icmp_ type":8,"icmp_code":0,"alert":{"action":"allowed","gid":1,"signature_id":1,"rev":0,"signature":"ICMP Test","category":"","severity":3},"flow" :{"pkts_toserver":2186,"pkts_toclient":2185,"bytes_toserver":214228,"bytes_toclient":214130,"start":"2025-02-26T10:11:34.272886+0100"}} | ||
| + | {"timestamp":"2025-02- | ||
| + | </pre> | ||
| + | ==Nun binden wir das IDS ein== | ||
| + | ===Wazuh-Manager so konfigurieren, dass er Suricata-Logs liest=== | ||
| + | *vi /var/ossec/etc/ossec.conf | ||
| + | <pre> | ||
| + | <localfile> | ||
| + | <log_format>json</log_format> | ||
| + | <location>/var/log/suricata/eve.json</location> | ||
| + | </localfile> | ||
| + | </pre> | ||
| + | |||
| + | ===Restart des Managers=== | ||
| + | *systemctl restart wazuh-manager | ||
| + | ===Prüfen, ob Suricata-Logs erkannt werden=== | ||
| + | *tail -n 2 /var/ossec/logs/alerts/alerts.json | grep ICMP | ||
| + | <pre> | ||
| + | {"timestamp":"2025-02-26T11:03:13.867+0100","rule":{"level":3,"description":"Suricata: Alert - ICMP Test","id":"86601","firedtimes":47,"mail":false,"groups":["ids","suricata"]},"agent":{"id":"000","name":"wazuh"},"manager":{"name":"wazuh"},"id":"1740564193.730895","decoder":{"name":"json"},"data":{"timestamp":"2025-02-26T11:03:12.418275+0100","flow_id":"1157424342247926.000000","in_iface":"enp0s8","event_type":"alert","src_ip":"192.168.1.98","src_port":"0","dest_ip":"8.8.8.8","dest_port":"0","proto":"ICMP","icmp_type":"8","icmp_code":"0","alert":{"action":"allowed","gid":"1","signature_id":"1","rev":"0","signature":"ICMP Test","severity":"3"},"flow":{"pkts_toserver":"3072","pkts_toclient":"3071","bytes_toserver":"301056","bytes_toclient":"300958","start":"2025-02-26T10:11:34.272886+0100"}},"location":"/var/log/suricata/eve.json"} | ||
| + | {"timestamp":"2025-02-26T11:03:13.867+0100","rule":{"level":3,"description":"Suricata: Alert - ICMP Test","id":"86601","firedtimes":48,"mail":false,"groups":["ids","suricata"]},"agent":{"id":"000","name":"wazuh"},"manager":{"name":"wazuh"},"id":"1740564193.732011","decoder":{"name":"json"},"data":{"timestamp":"2025-02-26T11:03:13.421060+0100","flow_id":"1157424342247926.000000","in_iface":"enp0s8","event_type":"alert","src_ip":"192.168.1.98","src_port":"0","dest_ip":"8.8.8.8","dest_port":"0","proto":"ICMP","icmp_type":"8","icmp_code":"0","alert":{"action":"allowed","gid":"1","signature_id":"1","rev":"0","signature":"ICMP Test","severity":"3"},"flow":{"pkts_toserver":"3073","pkts_toclient":"3072","bytes_toserver":"301154","bytes_toclient":"301056","start":"2025-02-26T10:11:34.272886+0100"}},"location":"/var/log/suricata/eve.json"} | ||
| + | </pre> | ||
| + | ===Tread Hunting=== | ||
| + | *Burgermenu | ||
| + | **Threat Hunting | ||
| + | ***Events | ||
| + | ****Filter: '''rule.groups:suricata''' | ||
| + | [[Datei:Ids-1001.png|800px]] | ||
| + | ===Eigenes Dashboard=== | ||
| + | ;Dashboard | ||
| + | *Burgermenu | ||
| + | **Dashboards | ||
| + | ***Create New Dasboard | ||
| + | ;Object | ||
| + | *Create New Object | ||
| + | **Data Table | ||
| + | ***Wazu-alterts | ||
| + | ;Filter | ||
| + | *Add filter | ||
| + | **rule.groups is suricata | ||
| + | ;Buckets | ||
| + | *Add bucket | ||
| + | **Split rows | ||
| + | ***Aggregation | ||
| + | ****Terms | ||
| + | *****Field | ||
| + | ******@timestamp | ||
| + | *Add bucket | ||
| + | **Split rows | ||
| + | ***Aggregation | ||
| + | ****Terms | ||
| + | *****Field | ||
| + | ******agent.name | ||
| + | *Add bucket | ||
| + | **Split rows | ||
| + | ***Aggregation | ||
| + | ****Terms | ||
| + | *****Field | ||
| + | ******rule.description | ||
| + | *Add bucket | ||
| + | **Split rows | ||
| + | ***Aggregation | ||
| + | ****Terms | ||
| + | *****Field | ||
| + | ******data.src_ip | ||
| + | **Split rows | ||
| + | ***Aggregation | ||
| + | ****Terms | ||
| + | *****Field | ||
| + | ******data.dest_ip | ||
| + | =Weiteres= | ||
| + | <pre> | ||
| + | Prüffrage: Was will ich eigentlich darstellen? Was stellt mir Wazuh zur Verfügung (Welche Datensätze lassen sich wie darstellen) | ||
| + | |||
| + | Beispiel: Rule Groups by Time | ||
| + | |||
| + | In der Rule Groups by Time wird der Aufruf von bestimmten Funktionen mitgeplottet und dort grafisch in zeitlicher Reihenfolge angezeigt. | ||
| + | |||
| + | Dashboards erstellen | ||
| + | |||
| + | Burgermenü - Explore - Dashboards | ||
| + | |||
| + | Create new -> Line -> wazuh-alerts | ||
| + | |||
| + | Wazuh-alerts | ||
| + | |||
| + | Um die Grafik richtig anzeigen zu können, bestimmt man über Metrics die Senkrechte (Y) Achse. Die lass ich in diesem Beispiel auf Count um die Zugriffe zu Zählen (COUNT). | ||
| + | Unter Buckets ist es wichtig jetzt die waagerechte (X) Achse hinzuzufügen, um dort den zeitlichen Graphen zu beginnen. Unter "Select an Aggregation" "Date Histogram" auswählen. Bei Field ist jetzt automatisch der Timestamp hinterlegt (Logisch). Unter Minimum Interval lässt sich hier der Ableserhytmus hinterlegen, wie oft er ablesen soll und unter Custom label lassen sich individuelle für den Timestamp ein eigenen Namen hinterlegen. | ||
| + | |||
| + | |||
| + | Add - Split series | ||
| + | Als Aggeregation wähle ich in diesem Beispiel Terms um die darzustellende Funktion anzeigen zu lassen. Unter Field wähle ich nun rule.groups und lasse die Sortierung mit Metric: Count. Klicke auf Update und fertig. | ||
| + | |||
| + | Save | ||
| + | |||
| + | Save | ||
| + | </pre> | ||
| + | |||
| + | |||
| + | [[Kategorie:WAZUH]] | ||
Aktuelle Version vom 12. März 2025, 12:27 Uhr
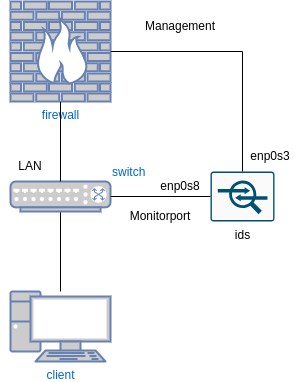
Aufbau
Sniffing Schnittstelle anfügen
- vi /etc/network/interfaces
auto enp0s8 iface enp0s8 inet manual post-up ip link set enp0s8 promisc on
Suricata
Installation
- apt update
- apt install -y suricata
Minimal Konfiguration
Konfigfile
- cat /etc/suricata/suricata.yaml
%YAML 1.1
---
# Standard-Log-Verzeichnis
default-log-dir: /var/log/suricata/
# Statistiken aktivieren
stats:
enabled: yes
interval: 8
# Ausgaben konfigurieren
outputs:
- fast:
enabled: yes
filename: fast.log
append: yes
- alert-debug:
enabled: yes
filename: alert-debug.log
append: yes
- stats:
enabled: yes
filename: stats.log
append: yes
totals: yes
threads: no
# Logging-Einstellungen
logging:
default-log-level: notice
outputs:
- console:
enabled: yes
- file:
enabled: yes
level: info
filename: suricata.log
# Netzwerkschnittstelle für Mirror-Port konfigurieren
af-packet:
- interface: enp0s8
threads: auto
cluster-id: 99
cluster-type: cluster_flow
defrag: yes
use-mmap: yes
ring-size: 2048
buffer-size: 65535
mmap-locked: yes
tpacket-v3: yes
checksum-checks: no
# Alternativ PCAP-Modus (wenn AF_PACKET nicht genutzt wird)
pcap:
- interface: enp0s8
buffer-size: 65535
checksum-checks: no
# PID-Datei
pid-file: /var/run/suricata.pid
# Coredump-Einstellungen
coredump:
max-dump: unlimited
# Host-Modus
host-mode: auto
# Unix-Befehlseingabe konfigurieren
unix-command:
enabled: yes
filename: /var/run/suricata-command.socket
# Engine-Analyse-Einstellungen
engine-analysis:
rules-fast-pattern: yes
rules: yes
# Defragmentierungseinstellungen
defrag:
memcap: 32mb
hash-size: 65536
trackers: 65535
max-frags: 65535
prealloc: yes
timeout: 60
# Standardregelverzeichnis
default-rule-path: /etc/suricata/rules
# Regel-Dateien
rule-files:
- local.rules
# Klassifikationsdatei
classification-file: /etc/suricata/classification.config
# Referenzkonfigurationsdatei
reference-config-file: /etc/suricata/reference.config
app-layer:
protocols:
http:
enabled: yes
tls:
enabled: yes
dcerpc:
enabled: yes
smb:
enabled: yes
ftp:
enabled: yes
ssh:
enabled: yes
smtp:
enabled: yes
dns:
enabled: yes
modbus:
enabled: yes
enip:
enabled: yes
dnp3:
enabled: yes
nfs:
enabled: yes
ntp:
enabled: yes
tftp:
enabled: yes
ikev2:
enabled: yes
krb5:
enabled: yes
dhcp:
enabled: yes
snmp:
enabled: yes
sip:
enabled: yes
rfb:
enabled: yes
mqtt:
enabled: yes
rdp:
enabled: yes
http2:
enabled: yes
imap:
enabled: yes
Eigene Regeln
- cat /etc/suricata/rules/local.rules
alert icmp any any -> any any (msg:"ICMP Test"; flow:to_server; sid:1;) alert tcp any any -> any any (flags: S; msg: "SYN packet"; sid:2;)
Test
- suricata -T -c /etc/suricata/suricata.yaml
26/2/2025 -- 09:39:13 - <Info> - Running suricata under test mode 26/2/2025 -- 09:39:13 - <Notice> - This is Suricata version 6.0.10 RELEASE running in SYSTEM mode 26/2/2025 -- 09:39:13 - <Notice> - Configuration provided was successfully loaded. Exiting.
Erster Start
- Vordergrund
suricata -c /etc/suricata/suricata.yaml --af-packet
- Hintergrund
suricata -c /etc/suricata/suricata.yaml --af-packet -D
Wazuh
Installation
Anpassen von Suricata
- Nachdem Wazuh läuft, muss Suricata so konfiguriert werden, dass es die Logs an Wazuh sendet.
- Suricata-Logging anpassen Öffne die suricata.yaml und stelle sicher, dass die JSON-Logs aktiviert sind:
- vi /etc/suricata/suricata.yaml
outputs:
...
- eve-log:
enabled: yes
filetype: regular
filename: /var/log/suricata/eve.json
types:
- alert
- anomaly
- dns
- tls
- http
- ssh
- smtp
- Runterfahren
- suricatasc -c shutdown
- Neustarten
- suricata -c /etc/suricata/suricata.yaml --af-packet -D
- Kontrolle ob etwas geloggt wird
tail -f /var/log/suricata/eve.json
{"timestamp":"2025-02- 26T10:48:17.825694+0100","flow_id":1157424342247926,"in_iface":"enp0s8","event_type":"alert","src_ip":"192.168.1.98","src_port":0,"dest_ip":"8.8.8.8","dest_port":0,"proto":"ICMP","icmp_ type":8,"icmp_code":0,"alert":{"action":"allowed","gid":1,"signature_id":1,"rev":0,"signature":"ICMP Test","category":"","severity":3},"flow" :{"pkts_toserver":2186,"pkts_toclient":2185,"bytes_toserver":214228,"bytes_toclient":214130,"start":"2025-02-26T10:11:34.272886+0100"}}
{"timestamp":"2025-02-
Nun binden wir das IDS ein
Wazuh-Manager so konfigurieren, dass er Suricata-Logs liest
- vi /var/ossec/etc/ossec.conf
<localfile> <log_format>json</log_format> <location>/var/log/suricata/eve.json</location> </localfile>
Restart des Managers
- systemctl restart wazuh-manager
Prüfen, ob Suricata-Logs erkannt werden
- tail -n 2 /var/ossec/logs/alerts/alerts.json | grep ICMP
{"timestamp":"2025-02-26T11:03:13.867+0100","rule":{"level":3,"description":"Suricata: Alert - ICMP Test","id":"86601","firedtimes":47,"mail":false,"groups":["ids","suricata"]},"agent":{"id":"000","name":"wazuh"},"manager":{"name":"wazuh"},"id":"1740564193.730895","decoder":{"name":"json"},"data":{"timestamp":"2025-02-26T11:03:12.418275+0100","flow_id":"1157424342247926.000000","in_iface":"enp0s8","event_type":"alert","src_ip":"192.168.1.98","src_port":"0","dest_ip":"8.8.8.8","dest_port":"0","proto":"ICMP","icmp_type":"8","icmp_code":"0","alert":{"action":"allowed","gid":"1","signature_id":"1","rev":"0","signature":"ICMP Test","severity":"3"},"flow":{"pkts_toserver":"3072","pkts_toclient":"3071","bytes_toserver":"301056","bytes_toclient":"300958","start":"2025-02-26T10:11:34.272886+0100"}},"location":"/var/log/suricata/eve.json"}
{"timestamp":"2025-02-26T11:03:13.867+0100","rule":{"level":3,"description":"Suricata: Alert - ICMP Test","id":"86601","firedtimes":48,"mail":false,"groups":["ids","suricata"]},"agent":{"id":"000","name":"wazuh"},"manager":{"name":"wazuh"},"id":"1740564193.732011","decoder":{"name":"json"},"data":{"timestamp":"2025-02-26T11:03:13.421060+0100","flow_id":"1157424342247926.000000","in_iface":"enp0s8","event_type":"alert","src_ip":"192.168.1.98","src_port":"0","dest_ip":"8.8.8.8","dest_port":"0","proto":"ICMP","icmp_type":"8","icmp_code":"0","alert":{"action":"allowed","gid":"1","signature_id":"1","rev":"0","signature":"ICMP Test","severity":"3"},"flow":{"pkts_toserver":"3073","pkts_toclient":"3072","bytes_toserver":"301154","bytes_toclient":"301056","start":"2025-02-26T10:11:34.272886+0100"}},"location":"/var/log/suricata/eve.json"}
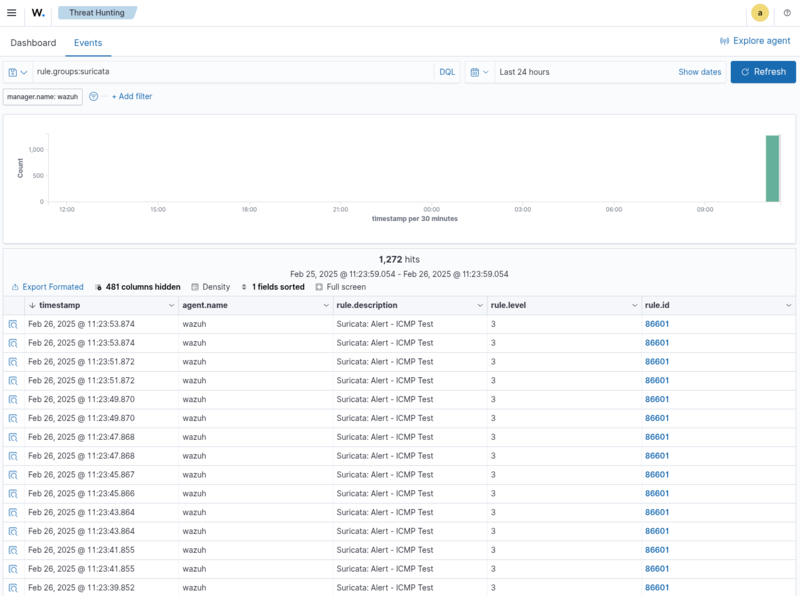
Tread Hunting
- Burgermenu
- Threat Hunting
- Events
- Filter: rule.groups:suricata
- Events
- Threat Hunting
Eigenes Dashboard
- Dashboard
- Burgermenu
- Dashboards
- Create New Dasboard
- Dashboards
- Object
- Create New Object
- Data Table
- Wazu-alterts
- Data Table
- Filter
- Add filter
- rule.groups is suricata
- Buckets
- Add bucket
- Split rows
- Aggregation
- Terms
- Field
- @timestamp
- Field
- Terms
- Aggregation
- Split rows
- Add bucket
- Split rows
- Aggregation
- Terms
- Field
- agent.name
- Field
- Terms
- Aggregation
- Split rows
- Add bucket
- Split rows
- Aggregation
- Terms
- Field
- rule.description
- Field
- Terms
- Aggregation
- Split rows
- Add bucket
- Split rows
- Aggregation
- Terms
- Field
- data.src_ip
- Field
- Terms
- Aggregation
- Split rows
- Aggregation
- Terms
- Field
- data.dest_ip
- Field
- Terms
- Aggregation
- Split rows
Weiteres
Prüffrage: Was will ich eigentlich darstellen? Was stellt mir Wazuh zur Verfügung (Welche Datensätze lassen sich wie darstellen) Beispiel: Rule Groups by Time In der Rule Groups by Time wird der Aufruf von bestimmten Funktionen mitgeplottet und dort grafisch in zeitlicher Reihenfolge angezeigt. Dashboards erstellen Burgermenü - Explore - Dashboards Create new -> Line -> wazuh-alerts Wazuh-alerts Um die Grafik richtig anzeigen zu können, bestimmt man über Metrics die Senkrechte (Y) Achse. Die lass ich in diesem Beispiel auf Count um die Zugriffe zu Zählen (COUNT). Unter Buckets ist es wichtig jetzt die waagerechte (X) Achse hinzuzufügen, um dort den zeitlichen Graphen zu beginnen. Unter "Select an Aggregation" "Date Histogram" auswählen. Bei Field ist jetzt automatisch der Timestamp hinterlegt (Logisch). Unter Minimum Interval lässt sich hier der Ableserhytmus hinterlegen, wie oft er ablesen soll und unter Custom label lassen sich individuelle für den Timestamp ein eigenen Namen hinterlegen. Add - Split series Als Aggeregation wähle ich in diesem Beispiel Terms um die darzustellende Funktion anzeigen zu lassen. Unter Field wähle ich nun rule.groups und lasse die Sortierung mit Metric: Count. Klicke auf Update und fertig. Save Save