Unix-/Linux Netz: Unterschied zwischen den Versionen
Zur Navigation springen
Zur Suche springen
| Zeile 11: | Zeile 11: | ||
{{#drawio:ul2}} | {{#drawio:ul2}} | ||
| + | |||
| + | =TCPDUMP auf rechter Firewall mit und ohne IP FORWARDING= | ||
| + | ;ip_forward an | ||
| + | *echo 1 > /proc/sys/net/ip4/ip_forward | ||
| + | ;äussere Schnittstelle | ||
| + | *tcpdump -n -c 2 -i enp0s8 icmp | ||
| + | tcpdump: verbose output suppressed, use -v[v]... for full protocol decode | ||
| + | listening on enp0s8, link-type EN10MB (Ethernet), snapshot length 262144 bytes | ||
| + | 09:12:55.057180 IP 10.0.21.21 > 10.0.22.21: ICMP echo request, id 11437, seq 500, length 64 | ||
| + | 09:12:55.057909 IP 10.0.22.21 > 10.0.21.21: ICMP echo reply, id 11437, seq 500, length 64 | ||
| + | 2 packets captured | ||
| + | 2 packets received by filter | ||
| + | 0 packets dropped by kernel | ||
| + | ;innere Schnittstelle | ||
| + | *tcpdump -n -c 2 -i enp0s8 icmp | ||
| + | tcpdump: verbose output suppressed, use -v[v]... for full protocol decode | ||
| + | listening on enp0s8, link-type EN10MB (Ethernet), snapshot length 262144 bytes | ||
| + | 09:12:55.057180 IP 10.0.21.21 > 10.0.22.21: ICMP echo request, id 11437, seq 500, length 64 | ||
| + | 09:12:55.057909 IP 10.0.22.21 > 10.0.21.21: ICMP echo reply, id 11437, seq 500, length 64 | ||
| + | 2 packets captured | ||
| + | 2 packets received by filter | ||
| + | 0 packets dropped by kernel | ||
| + | ;ip_forward aus | ||
| + | *echo 0 > /proc/sys/net/ip4/ip_forward | ||
| + | ;äussere Schnittstelle | ||
| + | *tcpdump -n -c 2 -i enp0s3 icmp | ||
| + | tcpdump: verbose output suppressed, use -v[v]... for full protocol decode | ||
| + | listening on enp0s3, link-type EN10MB (Ethernet), snapshot length 262144 bytes | ||
| + | 09:13:54.225813 IP 10.0.21.21 > 10.0.22.21: ICMP echo request, id 11437, seq 559, length 64 | ||
| + | 09:13:55.249847 IP 10.0.21.21 > 10.0.22.21: ICMP echo request, id 11437, seq 560, length 64 | ||
| + | 2 packets captured | ||
| + | 2 packets received by filter | ||
| + | 0 packets dropped by kernel | ||
| + | ;innere Schnittstelle | ||
| + | *tcpdump -n -c 2 -i enp0s8 icmp | ||
| + | tcpdump: verbose output suppressed, use -v[v]... for full protocol decode | ||
| + | listening on enp0s8, link-type EN10MB (Ethernet), snapshot length 262144 bytes | ||
Version vom 13. September 2022, 07:17 Uhr
Vorarbeiten
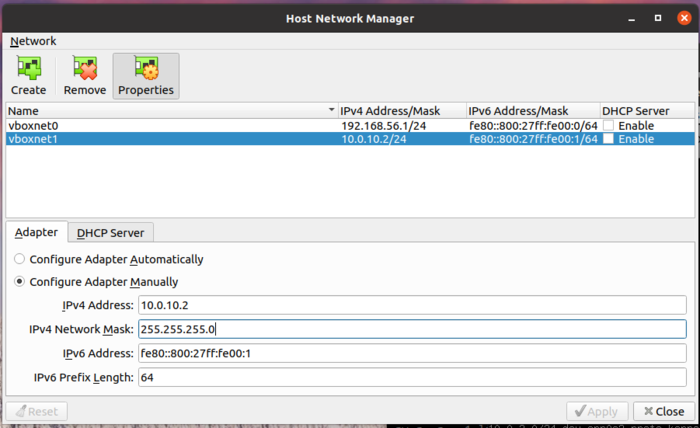
Hostadapter
- File
- Host Network Manager
- Create
- Host Network Manager
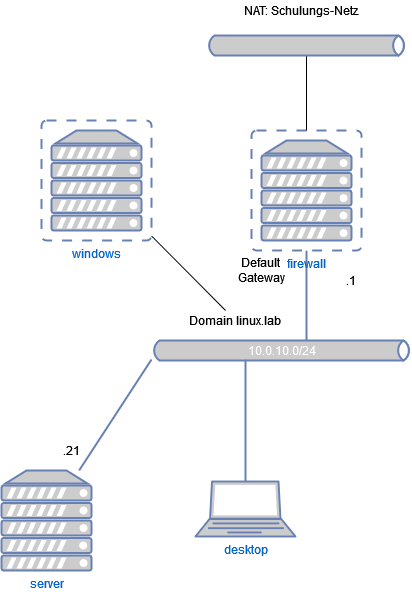
Schaubild
TCPDUMP auf rechter Firewall mit und ohne IP FORWARDING
- ip_forward an
- echo 1 > /proc/sys/net/ip4/ip_forward
- äussere Schnittstelle
- tcpdump -n -c 2 -i enp0s8 icmp
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode listening on enp0s8, link-type EN10MB (Ethernet), snapshot length 262144 bytes 09:12:55.057180 IP 10.0.21.21 > 10.0.22.21: ICMP echo request, id 11437, seq 500, length 64 09:12:55.057909 IP 10.0.22.21 > 10.0.21.21: ICMP echo reply, id 11437, seq 500, length 64 2 packets captured 2 packets received by filter 0 packets dropped by kernel
- innere Schnittstelle
- tcpdump -n -c 2 -i enp0s8 icmp
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode listening on enp0s8, link-type EN10MB (Ethernet), snapshot length 262144 bytes 09:12:55.057180 IP 10.0.21.21 > 10.0.22.21: ICMP echo request, id 11437, seq 500, length 64 09:12:55.057909 IP 10.0.22.21 > 10.0.21.21: ICMP echo reply, id 11437, seq 500, length 64 2 packets captured 2 packets received by filter 0 packets dropped by kernel
- ip_forward aus
- echo 0 > /proc/sys/net/ip4/ip_forward
- äussere Schnittstelle
- tcpdump -n -c 2 -i enp0s3 icmp
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode listening on enp0s3, link-type EN10MB (Ethernet), snapshot length 262144 bytes 09:13:54.225813 IP 10.0.21.21 > 10.0.22.21: ICMP echo request, id 11437, seq 559, length 64 09:13:55.249847 IP 10.0.21.21 > 10.0.22.21: ICMP echo request, id 11437, seq 560, length 64 2 packets captured 2 packets received by filter 0 packets dropped by kernel
- innere Schnittstelle
- tcpdump -n -c 2 -i enp0s8 icmp
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode listening on enp0s8, link-type EN10MB (Ethernet), snapshot length 262144 bytes