Iptables Failover: Unterschied zwischen den Versionen
Zur Navigation springen
Zur Suche springen
| Zeile 11: | Zeile 11: | ||
** IP: 3.3.3.3 | ** IP: 3.3.3.3 | ||
** Lokales Netz: 10.0.10.0/24 | ** Lokales Netz: 10.0.10.0/24 | ||
| − | * | + | |
| + | <span id="firewall"></span> | ||
| + | = Firewall = | ||
| + | |||
| + | * vi /usr/local/sbin/firewall | ||
| + | |||
| + | <!-----> | ||
| + | #!/bin/bash | ||
| + | #Einlesen der Konfigurationsdatei | ||
| + | source /usr/local/etc/firewall.cfg | ||
| + | echo normal > /tmp/fw.status | ||
| + | case $1 in | ||
| + | start) | ||
| + | echo "starte firewall" | ||
| + | #Löschen aller Reglen | ||
| + | iptables -F | ||
| + | iptables -F -t nat | ||
| + | iptables -F -t mangle | ||
| + | |||
| + | iptables -X | ||
| + | iptables -X -t nat | ||
| + | iptables -X -t mangle | ||
| + | |||
| + | #Setzen der Default Policy auf DROP | ||
| + | iptables -P INPUT DROP | ||
| + | iptables -P OUTPUT DROP | ||
| + | iptables -P FORWARD DROP | ||
| + | #Aktivieren des Connection Tracking Konzeptes | ||
| + | iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT | ||
| + | iptables -A FORWARD -m state --state ESTABLISHED,RELATED -j ACCEPT | ||
| + | iptables -A OUTPUT -m state --state ESTABLISHED,RELATED -j ACCEPT | ||
| + | #Verkehr von Rechner hinaus freischalten | ||
| + | iptables -A OUTPUT -m state --state NEW -j ACCEPT | ||
| + | #Verkehr über das loopback device freischalten | ||
| + | iptables -A INPUT -i lo -m state --state NEW -j ACCEPT | ||
| + | #Verkehr zum Rechner ZUM TCP PORT 22 erlauben | ||
| + | iptables -A INPUT -p tcp --dport 22 -m state --state NEW -j ACCEPT | ||
| + | #ICMP echo-request freigeschaltet | ||
| + | iptables -A INPUT -p icmp --icmp-type echo-request -m state --state NEW -j ACCEPT | ||
| + | |||
| + | iptables -A FORWARD -m state --state NEW -j ACCEPT | ||
| + | |||
| + | iptables -t mangle -N tel | ||
| + | iptables -t mangle -A tel -j MARK --set-mark 200 | ||
| + | |||
| + | if test "$2" = "backup" | ||
| + | then | ||
| + | echo backup > /tmp/fw.status | ||
| + | iptables -A PREROUTING -t mangle -s $LAN ! -d $LAN -j tel | ||
| + | iptables -A OUTPUT -t mangle -s $LANIP ! -d $LAN -j tel | ||
| + | fi | ||
| + | |||
| + | iptables -t nat -A POSTROUTING -j SNAT -s $LAN -d 10.0.10.0/24 -o $TELDEV --to-source 172.30.28.2 | ||
| + | iptables -t nat -A POSTROUTING -j SNAT -s $LAN -o $TELDEV --to-source $TELIP | ||
| + | iptables -t nat -A POSTROUTING -j SNAT -s $LAN -d 10.0.10.0/24 -o $VODDEV --to-source 172.30.28.1 | ||
| + | iptables -t nat -A POSTROUTING -j SNAT -s $LAN -o $VODDEV --to-source $VODIP | ||
| + | |||
| + | |||
| + | iptables -A INPUT -j LOG --log-prefix "--iptables-drop-in--" | ||
| + | iptables -A OUTPUT -j LOG --log-prefix "--iptables-drop-out--" | ||
| + | iptables -A FORWARD -j LOG --log-prefix "--iptables-drop-for--" | ||
| + | |||
| + | ;; | ||
| + | stop) | ||
| + | echo "stoppe firewall" | ||
| + | #Löschen aller Reglen | ||
| + | iptables -F | ||
| + | iptables -F -t nat | ||
| + | iptables -F -t mangle | ||
| + | iptables -X | ||
| + | iptables -X -t nat | ||
| + | iptables -X -t mangle | ||
| + | #Setzen der Default Policy auf ACCEPT | ||
| + | iptables -P INPUT ACCEPT | ||
| + | iptables -P OUTPUT ACCEPT | ||
| + | iptables -P FORWARD ACCEPT | ||
| + | ;; | ||
| + | *) | ||
| + | echo "usage: $0 start|stop" | ||
| + | ;; | ||
| + | esac | ||
Version vom 15. Dezember 2022, 15:41 Uhr
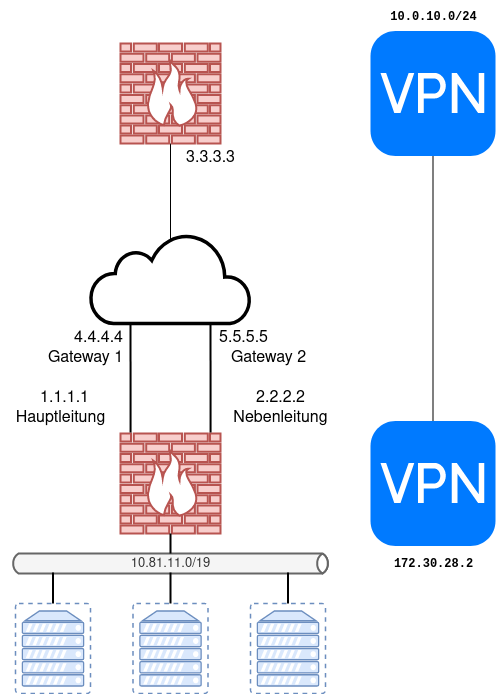
Ziel
- Eine Firewall hat zwei Internetleitungen
- Eine Hauptleitung 1.1.1.1
- Eine Nebenleitung 2.2.2.2
- Falls die Hauptleitung ausfällt sollen alle Pakete (Pings, Webanfragen, VPNs) automatisch über die Nebenleitung laufen.
- VPN:
- IP: 3.3.3.3
- Lokales Netz: 10.0.10.0/24
Firewall
- vi /usr/local/sbin/firewall
#!/bin/bash #Einlesen der Konfigurationsdatei source /usr/local/etc/firewall.cfg echo normal > /tmp/fw.status case $1 in start) echo "starte firewall" #Löschen aller Reglen iptables -F iptables -F -t nat iptables -F -t mangle iptables -X iptables -X -t nat iptables -X -t mangle #Setzen der Default Policy auf DROP iptables -P INPUT DROP iptables -P OUTPUT DROP iptables -P FORWARD DROP #Aktivieren des Connection Tracking Konzeptes iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT iptables -A FORWARD -m state --state ESTABLISHED,RELATED -j ACCEPT iptables -A OUTPUT -m state --state ESTABLISHED,RELATED -j ACCEPT #Verkehr von Rechner hinaus freischalten iptables -A OUTPUT -m state --state NEW -j ACCEPT #Verkehr über das loopback device freischalten iptables -A INPUT -i lo -m state --state NEW -j ACCEPT #Verkehr zum Rechner ZUM TCP PORT 22 erlauben iptables -A INPUT -p tcp --dport 22 -m state --state NEW -j ACCEPT #ICMP echo-request freigeschaltet iptables -A INPUT -p icmp --icmp-type echo-request -m state --state NEW -j ACCEPT iptables -A FORWARD -m state --state NEW -j ACCEPT iptables -t mangle -N tel iptables -t mangle -A tel -j MARK --set-mark 200 if test "$2" = "backup" then echo backup > /tmp/fw.status iptables -A PREROUTING -t mangle -s $LAN ! -d $LAN -j tel iptables -A OUTPUT -t mangle -s $LANIP ! -d $LAN -j tel fi iptables -t nat -A POSTROUTING -j SNAT -s $LAN -d 10.0.10.0/24 -o $TELDEV --to-source 172.30.28.2 iptables -t nat -A POSTROUTING -j SNAT -s $LAN -o $TELDEV --to-source $TELIP iptables -t nat -A POSTROUTING -j SNAT -s $LAN -d 10.0.10.0/24 -o $VODDEV --to-source 172.30.28.1 iptables -t nat -A POSTROUTING -j SNAT -s $LAN -o $VODDEV --to-source $VODIP iptables -A INPUT -j LOG --log-prefix "--iptables-drop-in--" iptables -A OUTPUT -j LOG --log-prefix "--iptables-drop-out--" iptables -A FORWARD -j LOG --log-prefix "--iptables-drop-for--" ;; stop) echo "stoppe firewall" #Löschen aller Reglen iptables -F iptables -F -t nat iptables -F -t mangle iptables -X iptables -X -t nat iptables -X -t mangle #Setzen der Default Policy auf ACCEPT iptables -P INPUT ACCEPT iptables -P OUTPUT ACCEPT iptables -P FORWARD ACCEPT ;; *) echo "usage: $0 start|stop" ;; esac