Cyber Security II. Netzplan: Unterschied zwischen den Versionen
Zur Navigation springen
Zur Suche springen
| Zeile 3: | Zeile 3: | ||
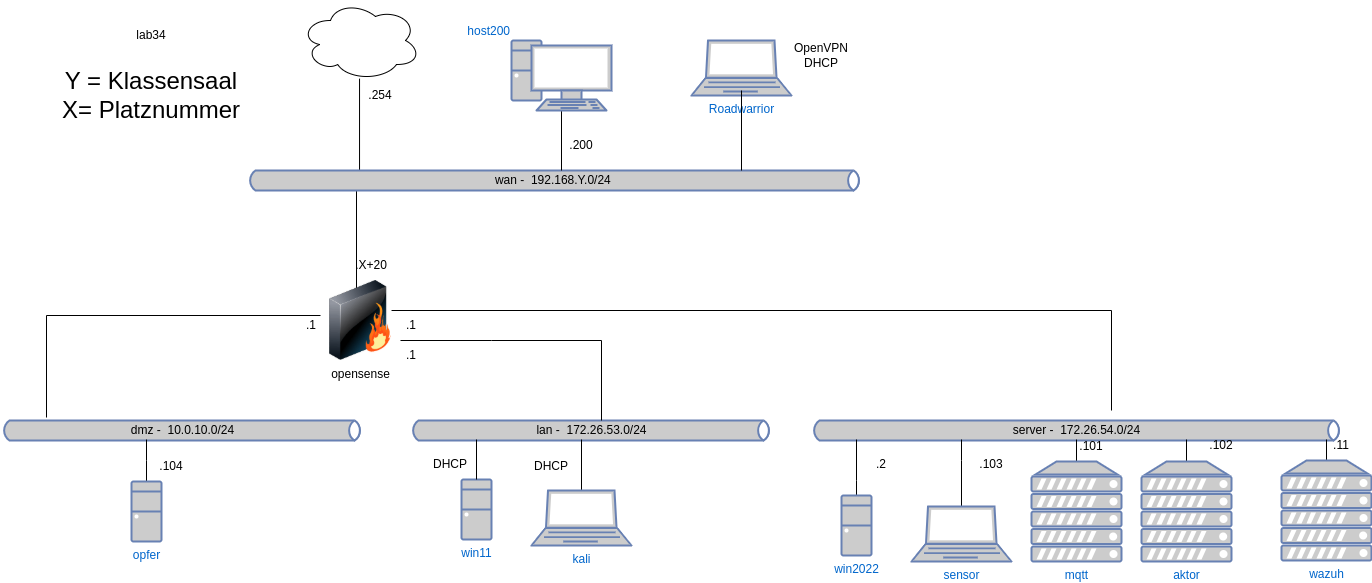
=HA Proxy= | =HA Proxy= | ||
{{#drawio:cybersec-2.2-haproxy}} | {{#drawio:cybersec-2.2-haproxy}} | ||
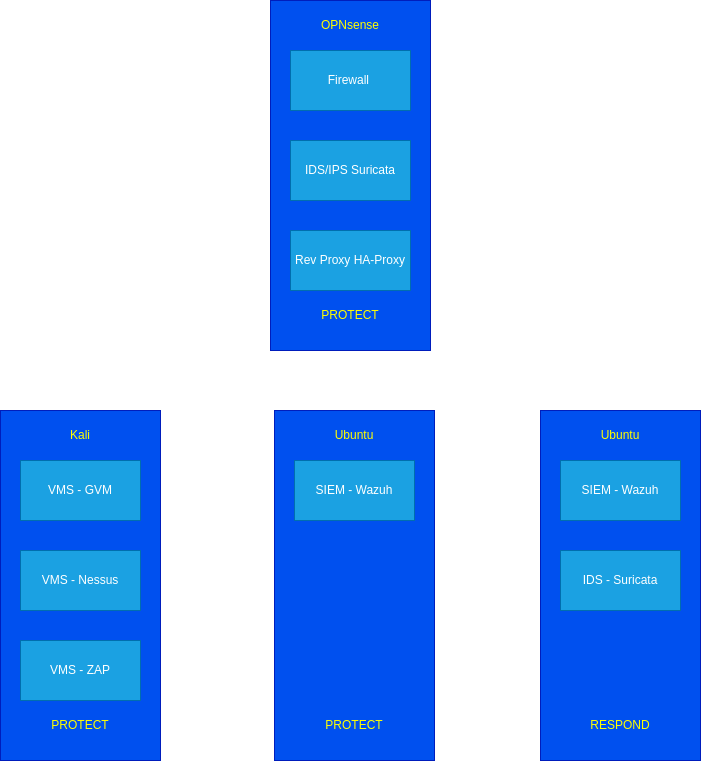
| + | =SOC= | ||
| + | {{#drawio:cybersec-2.3-soc}} | ||