Icinga2 mit puppet clients: Unterschied zwischen den Versionen
David (Diskussion | Beiträge) |
David (Diskussion | Beiträge) |
||
| Zeile 87: | Zeile 87: | ||
| − | verlinken der certifcate | + | |
| + | *kopieren der zertifikate auf den client | ||
| + | |||
| + | file { "/etc/icinga2/pki/trusted-master.crt": | ||
| + | ensure => file, | ||
| + | mode => "664", | ||
| + | owner => root, | ||
| + | group => root, | ||
| + | source => "puppet:///modules/icinga2client/trusted-master.crt", | ||
| + | require => Package["icinga2"] | ||
| + | } | ||
| + | file { '/etc/icinga2/zones.conf': | ||
| + | content => template('icinga2client/zones.conf'), | ||
| + | mode => "0644", | ||
| + | owner => root, group => root, | ||
| + | require => Package["icinga2"] | ||
| + | } | ||
| + | |||
| + | |||
| + | file { '/etc/icinga2/constants.conf': | ||
| + | content => template('icinga2client/constants.conf'), | ||
| + | mode => "0644", | ||
| + | owner => root, group => root, | ||
| + | require => Package["icinga2"] | ||
| + | |||
| + | |||
| + | |||
| + | |||
| + | *verlinken der certifcate | ||
| + | |||
| + | file { '/etc/icinga2/pki/ca.crt': | ||
| + | ensure => 'link', | ||
| + | target => '/etc/ssl/xin-ca.crt', | ||
| + | require => Package["icinga2"] | ||
| + | } | ||
| + | |||
| + | file { "/etc/icinga2/pki/${fqdn}.crt": | ||
| + | ensure => 'link', | ||
| + | target => "/etc/ssl/${fqdn}.crt", | ||
| + | require => Package["icinga2"] | ||
| + | } | ||
| + | |||
| + | file { "/etc/icinga2/pki/${fqdn}.key": | ||
| + | ensure => 'link', | ||
| + | target => "/etc/ssl/${fqdn}.key", | ||
| + | require => Package["icinga2"] | ||
| + | } | ||
Version vom 2. Oktober 2015, 07:25 Uhr
puppet zertifikate verteilen
ein modul erstellen wie unten im beispiel
class cert {
$cert = "${fqdn}.crt"
$key = "${fqdn}.key"
2 variablen setzen
damit wir die zertifikate richtig benen können
fqnd steht hier für fully qualified domain name
alls string würde der inhalt so ausehen
$key = irgendwas.xinux.org.key
file { '/etc/ssl/xin-ca.crt':
ensure => file,
mode => 664,
owner => root,
group => root,
source => 'puppet:///modules/cert/xin-ca.crt'
}
file { "/etc/ssl/$cert":
ensure => file,
mode => 664,
owner => root,
group => root,
source => "puppet:///modules/cert/$cert"
}
file { "/etc/ssl/$key":
ensure => file,
mode => 664,
owner => root,
group => root,
source => "puppet:///modules/cert/$key"
}
die source zeigt was kopiert werden soll
und file{wo es auf dem client landen soll}
mode,owner,group die rechte die auf dem client gesetzt werden sollen
icinga2 installation restart & verlinken
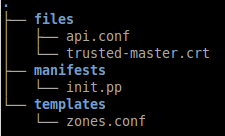
mkdir /etc/puppet/modules/icinga2-client
den ordner so strukturiern
- die init.pp
class icinga2-client {
Exec { path => [ "/bin/", "/sbin/" , "/usr/bin/", "/usr/sbin/" ] }
package { "icinga2":
ensure => present,
require => Exec["icinga_repository"],
}
exec { "add-apt-repository ppa:formorer/icinga && apt-get update":
alias => "icinga_repository",
creates => "/etc/apt/sources.list.d/formorer-icinga-trusty.list",
require => Package["software-properties-common"]
}
package { "software-properties-common":
ensure => present
}
alles was in dieser classe berücksichticht werden soll mus in den ersten {} stehen
also aufpassen das am schlus der datei mit } abgeschlosen ist
wir prüfen ob icinga2 installiert ist wenn nicht wird es installier sofern die repository stimmen
falls nicht fügen wird die repository hinzu wen software-properties-common installiert ist wen nicht installieren wir dies
- kopieren der zertifikate auf den client
file { "/etc/icinga2/pki/trusted-master.crt":
ensure => file,
mode => "664",
owner => root,
group => root,
source => "puppet:///modules/icinga2client/trusted-master.crt",
require => Package["icinga2"]
} file { '/etc/icinga2/zones.conf':
content => template('icinga2client/zones.conf'),
mode => "0644",
owner => root, group => root,
require => Package["icinga2"]
}
file { '/etc/icinga2/constants.conf':
content => template('icinga2client/constants.conf'),
mode => "0644",
owner => root, group => root,
require => Package["icinga2"]
- verlinken der certifcate
file { '/etc/icinga2/pki/ca.crt':
ensure => 'link', target => '/etc/ssl/xin-ca.crt', require => Package["icinga2"]
}
file { "/etc/icinga2/pki/${fqdn}.crt":
ensure => 'link',
target => "/etc/ssl/${fqdn}.crt",
require => Package["icinga2"]
}
file { "/etc/icinga2/pki/${fqdn}.key":
ensure => 'link',
target => "/etc/ssl/${fqdn}.key",
require => Package["icinga2"]
}