SELinux Policy
Version vom 12. Januar 2023, 10:13 Uhr von Linkai.zhang (Diskussion | Beiträge)
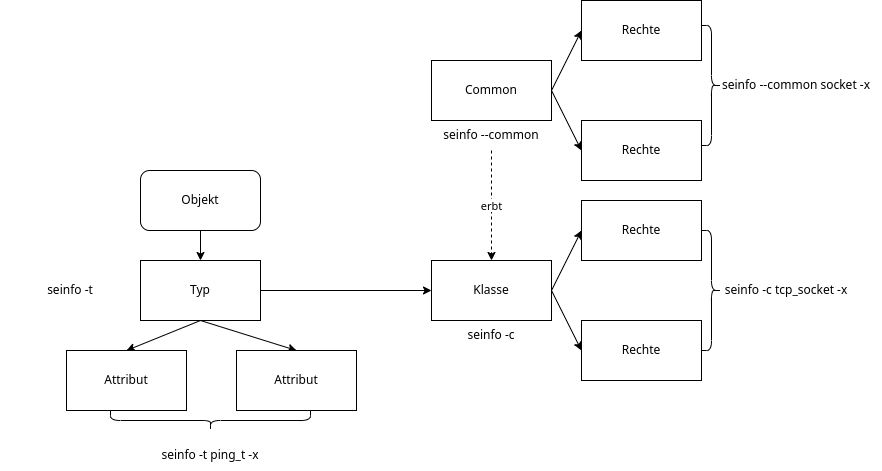
Regelstruktur
- sesearch -t ping_t -c tcp_socket --allow -dt
- Attribute werden benutzt, um Typen zu gruppieren.
- Attribute wirken sich nicht direkt auf Berechtigungen aus, sondern entscheiden über Dinge wie File- und Portlabeling
- Klassen werden in allow/disallow Regeln bestimmten Typen zugeordnet
- Klassen fassen Berechtigungen zusammen
Regeln suchen
- mit sesearch können SELinux-Regeln gesucht werden
- suchbare Felder sind Quell (-s)-/Zieltypen (-t), Objektklasse (-c), Berechtigungen (-p) und mit der Regel assoziierte Booleans (-b)
- mit -ds und -dt wird explizit nach dem Namen des jeweiligen Quell- und Zieltyp gesucht, statt nur nach passenden Attributen zu matchen
- Man muss angeben, ob man nach allow-Regeln (--allow) oder nach Typentransitionsregeln (-T) sucht
allow-Regeln und Domänentranstion anhand von user_t und dem ping-Programm
Welche Programme darf user_t ausführen?
- sesearch -s user_t -p execute --allow -ds | head
allow user_t application_exec_type:file { execute execute_no_trans getattr ioctl lock map open read };
allow user_t bin_t:file { entrypoint execute execute_no_trans getattr ioctl lock map open read };
allow user_t bluetooth_helper_exec_t:file { execute getattr ioctl map open read };
allow user_t cdrecord_exec_t:file { execute getattr ioctl map open read };
allow user_t checkpolicy_exec_t:file { execute execute_no_trans getattr ioctl lock map open read };
allow user_t chfn_exec_t:file { execute getattr ioctl map open read };
allow user_t chkpwd_exec_t:file { execute getattr ioctl map open read };
allow user_t chromium_exec_t:file { execute getattr ioctl map open read };
allow user_t chroot_exec_t:file { execute execute_no_trans getattr ioctl lock map open read };
allow user_t cifs_t:file { execute execute_no_trans getattr ioctl map open read }; [ use_samba_home_dirs ]:True
- sesearch -s user_t -p execute --allow -ds | grep ping_
allow user_t ping_exec_t:file { execute getattr ioctl map open read }; [ user_ping ]:True
Domänentransition
- Für eine Domänentransition muss der Übergang definiert und explicit erlaubt werden
- sesearch -s user_t -t ping_exec_t -T
type_transition user_t ping_exec_t:process ping_t; [ user_ping ]:True
- sesearch -s user_t -t ping_t -p transition --allow
allow user_t ping_t:process transition; [ user_ping ]:True
- Beim Aufruf von ping_exec_t über user_t geht der Prozess somit in ping_t über
Berechtigungen von ping_t anzeigen
- sesearch -s ping_t --allow -ds | head
allow ping_t auditadm_t:fd use; [ user_ping ]:True
allow ping_t auditadm_t:fifo_file { append getattr ioctl lock read write }; [ user_ping ]:True
allow ping_t auditadm_t:process sigchld; [ user_ping ]:True
allow ping_t console_device_t:chr_file { append getattr ioctl lock open write };
allow ping_t device_t:dir { getattr ioctl lock open read search };
allow ping_t device_t:lnk_file { getattr read };
allow ping_t devlog_t:sock_file { append getattr open write };
allow ping_t devpts_t:dir { getattr ioctl lock open read search };
allow ping_t dhcpc_t:fd use;
allow ping_t dhcpc_t:fifo_file { append getattr ioctl lock read write };
- sesearch -s ping_t --allow -ds | grep socket
allow ping_t init_t:unix_dgram_socket sendto;
allow ping_t init_t:unix_stream_socket { getattr ioctl read write };
allow ping_t kernel_t:unix_dgram_socket sendto;
allow ping_t netlabel_peer_t:rawip_socket recvfrom;
allow ping_t netlabel_peer_t:tcp_socket recvfrom;
allow ping_t netlabel_peer_t:udp_socket recvfrom;
allow ping_t node_t:rawip_socket node_bind;
allow ping_t ping_t:icmp_socket create;
allow ping_t ping_t:netlink_route_socket { append bind connect create getattr getopt ioctl nlmsg_read nlmsg_write read setattr setopt shutdown write };
allow ping_t ping_t:packet_socket { bind create getopt ioctl read setopt write };
allow ping_t ping_t:rawip_socket { bind create getattr getopt ioctl read setopt write };
allow ping_t ping_t:tcp_socket { accept append bind connect create getattr getopt ioctl listen read setattr setopt shutdown write }; [ allow_ypbind ]:True
allow ping_t ping_t:tcp_socket { append bind connect create getattr getopt ioctl read setattr setopt shutdown write };
allow ping_t ping_t:tcp_socket { append bind connect create getattr getopt ioctl read setattr setopt shutdown write }; [ allow_kerberos ]:True
allow ping_t ping_t:tcp_socket { append bind connect create getattr getopt ioctl read setattr setopt shutdown write }; [ authlogin_nsswitch_use_ldap ]:True
allow ping_t ping_t:udp_socket { append bind connect create getattr getopt ioctl read setattr setopt shutdown write };
allow ping_t ping_t:udp_socket { append bind connect create getattr getopt ioctl read setattr setopt shutdown write }; [ allow_kerberos ]:True
allow ping_t ping_t:udp_socket { append bind connect create getattr getopt ioctl read setattr setopt shutdown write }; [ allow_ypbind ]:True
allow ping_t ping_t:unix_dgram_socket { append bind connect create getattr getopt ioctl read setattr setopt shutdown write };
allow ping_t ping_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen read setattr setopt shutdown write };
allow ping_t ping_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen read setattr setopt shutdown write }; [ nscd_use_shm ]:True
allow ping_t ping_t:unix_stream_socket { accept append bind connect create getattr getopt ioctl listen read setattr setopt shutdown write }; [ nscd_use_shm ]:True
allow ping_t ping_t:unix_stream_socket { append bind connect create getattr getopt ioctl read setattr setopt shutdown write }; [ nscd_use_shm ]:False
allow ping_t ping_t:unix_stream_socket { append bind connect create getattr getopt ioctl read setattr setopt shutdown write }; [ nscd_use_shm ]:False
allow ping_t syslogd_t:unix_dgram_socket sendto;
allow ping_t syslogd_t:unix_stream_socket connectto;
Infos zum Objekt tcp_socket
- seinfo -c tcp_socket -x
Classes: 1
class tcp_socket
inherits socket
{
node_bind
name_connect
}
- seinfo --common socket -x
Commons: 1
common socket
{
lock
setattr
relabelto
shutdown
setopt
read
ioctl
listen
name_bind
bind
connect
recvfrom
getattr
write
getopt
append
create
relabelfrom
sendto
map
accept
}
Installierte Policy Module anschauen
- Die Policy Module liegen in kompilierte Form vor
- Man kann geladene Module extrahieren und dekompilieren
- semodule -l | grep ssh
- semodule -E ssh
- semodule_unpackage ssh.pp ssh.mod ssh.fc
ssh.fc enthält die file-contexts + head ssh.fc
ssh.mod enthält alle allow-Regeln, Booleans, Rollen, Typen, etc. in binärer Form + sedismod ssh.mod
Reading policy...
libsepol.policydb_index_others: security: 0 users, 2 roles, 313 types, 13 bools
libsepol.policydb_index_others: security: 1 sens, 1024 cats
libsepol.policydb_index_others: security: 112 classes, 0 rules, 0 cond rules
libsepol.policydb_index_others: security: 0 users, 2 roles, 313 types, 13 bools
libsepol.policydb_index_others: security: 1 sens, 1024 cats
libsepol.policydb_index_others: security: 112 classes, 0 rules, 0 cond rules
Binary policy module file loaded.
Module name: ssh
Module version: 2.4.2
Policy version: 21
Select a command:
1) display unconditional AVTAB
2) display conditional AVTAB
3) display users
4) display bools
5) display roles
6) display types, attributes, and aliases
7) display role transitions
8) display role allows
9) Display policycon
0) Display initial SIDs
a) Display avrule requirements
b) Display avrule declarations
c) Display policy capabilities
l) Link in a module
u) Display the unknown handling setting
F) Display filename_trans rules
f) set output file
m) display menu
q) quit
Command ('m' for menu):
- Die Regeln kann man mit 1 oder 2 anschauen
- bedingungslose Regeln
unconditional avtab:
--- begin avrule block ---
decl 1:
allow ssh_keygen_t ssh_keygen_exec_t : [file] { entrypoint };
allow ssh_keygen_t ssh_keygen_exec_t : [file] { ioctl read getattr lock map execute open };
type_transition [initrc_domain] ssh_keygen_exec_t : [process] ssh_keygen_t;
allow sshd_keygen_t sshd_keygen_exec_t : [file] { entrypoint };
allow sshd_keygen_t sshd_keygen_exec_t : [file] { ioctl read getattr lock map execute open };
type_transition [initrc_domain] sshd_keygen_exec_t : [process] sshd_keygen_t;
allow sshd_t [security_t] : [lnk_file] { read getattr };
...
- bedingte Regeln conditional avtab: — begin avrule block — decl 1: expression: use_samba_home_dirs current state: 0 True list: allow chroot_user_t [cifs_t] : [lnk_file] { read getattr }; allow chroot_user_t [cifs_t] : [dir] { getattr open search }; allow chroot_user_t [cifs_t] : [dir] { ioctl read getattr lock open search }; allow chroot_user_t [cifs_t] : [file] { ioctl read getattr lock open }; allow chroot_user_t [cifs_t] : [dir] { getattr open search }; allow chroot_user_t [cifs_t] : [dir] { ioctl read getattr lock open search }; …