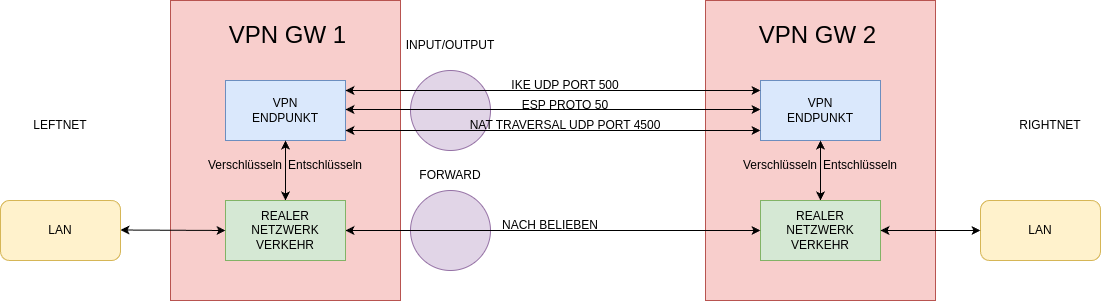
iptables
- Diese Regeln gehen davon aus, dass $LEFTNET das eigene Netz ist
- Ein Skript sollte die Befehle nach existierenden Regeln sortieren
iptables -A INPUT -m multiport -p udp --dport 500,4500 -o $WANDEV -j ACCEPT
iptables -A INPUT -i $WANDEV -p esp -j ACCEPT
iptables -A OUTPUT -m multiport -p udp --dport 500,4500 -o $WANDEV -j ACCEPT
iptables -A OUTPUT -i $WANDEV -p esp -j ACCEPT
iptables -A FORWARD -i $WANDEV -o $LANDEV -m policy --dir in --pol ipsec -j ACCEPT
iptables -A FORWARD -i $LANDEV -o $WANDEV -m policy --dir out --pol ipsec -j ACCEPT
iptables -t nat -A PREROUTING -i $WANDEV -s $RIGHTNET -j RETURN
iptables -t nat -A POSTROUTING -s $LEFTNET -o $WANDEV -d $RIGHTNET -j RETURN
nftables
- Diesselben Annahmen wie bei iptables
- vim /etc/nftables.conf
table inet filter {
chain input {
type filter hook input priority 0; policy drop;
iif $wandev udp dport { 500, 4500 } accept
iif $wandev ip protocol esp accept
}
chain output {
type filter hook output priority 0; policy drop;
oif $wandev udp dport { 500, 4500 } accept
oif $wandev ip protocol esp accept
}
chain forward {
type filter hook forward priority 0; policy drop;
iif $wandev oif $landev ipsec in ip daddr $leftnet accept
iif $landev oif $wandev ipsec in ip daddr $rightnet accept
}
}
table inet nat {
chain prerouting {
type nat hook prerouting priority -100;
iif $wandev ip saddr $rightnet return
}
chain postrouting {
type nat hook postrouting priority 100;
oif $wandev ip saddr $leftnet ip daddr $rightnet return
}
}