Nftables Netze absichern: Unterschied zwischen den Versionen
Zur Navigation springen
Zur Suche springen
| (132 dazwischenliegende Versionen von 2 Benutzern werden nicht angezeigt) | |||
| Zeile 1: | Zeile 1: | ||
| − | =Einleitung= | + | = Einleitung = |
| − | *Nachdem wir ein Hostsystem abgesichert haben, kommen wir nun zum Absichern von Netzen. | + | |
| − | *Die Firewall agiert als Vermittler zwischen verschiedenen Netzen. | + | * Nachdem wir ein Hostsystem abgesichert haben, kommen wir nun zum Absichern von Netzen. |
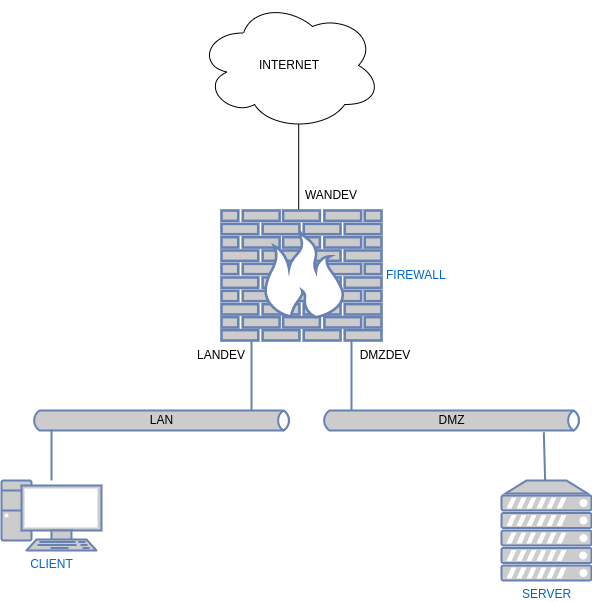
| − | *In unserem Beispiel haben wir 3 Netzbereiche. | + | * Die Firewall agiert als Vermittler zwischen verschiedenen Netzen. |
| + | * In unserem Beispiel haben wir 3 Netzbereiche. | ||
| + | |||
| + | = WAN = | ||
| + | |||
| + | * Wide Area Net steht für alles was nicht die anderen beiden Netze betrifft | ||
| + | |||
| + | = LAN = | ||
| + | |||
| + | * Local Area Net steht in der Regel für ein Netz das von aussen nicht erreichbar ist. | ||
| + | * Meist ist es über Network Address Translation (NAT) angebunden. | ||
| + | |||
| + | = DMZ = | ||
| + | |||
| + | * Demilitarized Zone ist ein Netz welches von außen erreichbar ist. | ||
| + | * Die Zugriffe werden aber durch die Firewall abgesichert. | ||
| + | * Dort werden meistens Dienste wie Mail oder Web gehostet. Teilweise auch Proxy Server. | ||
| + | |||
| + | = Der Plan = | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
{{#drawio:netzplan-nftables-1}} | {{#drawio:netzplan-nftables-1}} | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | flush ruleset | + | = Das Grundgerüst = |
| − | table inet filter { | + | |
| + | * Wir nutzen unsere Host Firewall als Ausgangsskript | ||
| + | * Wir wollen aber von vorneherein verstärkt mit Variablen arbeiten. | ||
| + | * Dies macht die Skripte universeller. | ||
| + | * '''vim /etc/nftables.conf''' | ||
| + | |||
| + | #!/usr/sbin/nft -f | ||
| + | define wandev = enp0s3 | ||
| + | define wanip = 192.168.5.213 | ||
| + | define lan = 172.17.213.0/24 | ||
| + | define server = 172.16.213.0/24 | ||
| + | define mgmt = 172.18.213.0/24 | ||
| + | define dmz = 10.88.213.0/24 | ||
| + | |||
| + | define local_tcp_ports = { 22 } | ||
| + | |||
| + | flush ruleset | ||
| + | table inet filter { | ||
chain input { | chain input { | ||
type filter hook input priority filter; policy drop; | type filter hook input priority filter; policy drop; | ||
ct state established,related accept | ct state established,related accept | ||
| + | ct state new iifname "lo" accept | ||
ct state new tcp dport $local_tcp_ports accept | ct state new tcp dport $local_tcp_ports accept | ||
| + | ct state new icmp type echo-request accept | ||
log prefix "--nftables-drop-input--" | log prefix "--nftables-drop-input--" | ||
} | } | ||
| − | + | <span style="color:#FF0000">chain forward {</span> | |
| − | type filter hook forward priority filter; policy drop; | + | <span style="color:#FF0000">type filter hook forward priority filter; policy drop;</span> |
| − | ct state established,related accept | + | <span style="color:#FF0000">ct state established,related accept</span> |
| − | log prefix "--nftables-drop-forward--" | + | <span style="color:#FF0000">log prefix "--nftables-drop-forward--"</span> |
| − | + | <span style="color:#FF0000">}</span> | |
| − | + | ||
chain output { | chain output { | ||
type filter hook output priority filter; policy drop; | type filter hook output priority filter; policy drop; | ||
ct state established,related accept | ct state established,related accept | ||
ct state new oifname "lo" accept | ct state new oifname "lo" accept | ||
| − | ct state new | + | ct state new accept |
| − | |||
log prefix "--nftables-drop-output--" | log prefix "--nftables-drop-output--" | ||
} | } | ||
| − | } | + | } |
| + | |||
| + | table inet nat { | ||
| + | chain postrouting { | ||
| + | type nat hook postrouting priority 100; policy accept; | ||
| + | |||
| + | oif $wandev ip saddr $lan snat to $wanip | ||
| + | oif $wandev ip saddr $server snat to $wanip | ||
| + | oif $wandev ip saddr $mgmt snat to $wanip | ||
| + | # DMZ wird genattet, außer zu 10.88.0.0/16 und 10.82.89.0/24 | ||
| + | oif $wandev ip saddr $dmz ip daddr != { 10.88.0.0/16, 10.82.89.0/24 } snat to $wanip | ||
| + | } | ||
| + | |||
| + | = Forwarding = | ||
| + | |||
| + | Damit Pakete weitergeleitet werden können, muss als erstes FORWARDING im Kernel aktiviert werden. | ||
| + | |||
| + | == Aktivierung == | ||
| + | |||
| + | * '''echo "net.ipv4.ip_forward = 1" >> /etc/sysctl.conf''' | ||
| + | * '''sysctl -p''' | ||
| + | |||
| + | == Weitere Tabellen == | ||
| + | |||
| + | * Eine Skizze über die Reihenfolge der Hooks. | ||
| + | * Als erstes greift der Prerouting-Hook | ||
| + | * Je nachdem wie geroutet wird greift dann entweder Input- oder Fowrward-Hook | ||
| + | * Falls ein lokaler Prozess ein Paket sendet, dann greift der Output-Hook | ||
| + | * Als letztes kann man das Paket mit dem Postrouting-Hook beeinflußen | ||
| + | |||
| + | {{#drawio:nft-inet1}} | ||
| + | |||
| + | == SNAT == | ||
| + | |||
| + | * Rechner in einem LAN können nicht ohne weiteres mit dem WAN kommunizieren, da an die lokale IP-Adresse der Rechner im LAN nicht von außen geroutet werden kann. | ||
| + | * Um eine Internetverbindung aufzubauen, muss die Adresse aus dem LAN in eine öffentliche umgeschrieben werden. | ||
| + | |||
| + | #!/usr/sbin/nft -f | ||
| + | define wandev = enp0s3 | ||
| + | define wanip = 192.168.5.213 | ||
| + | define lan = 172.17.213.0/24 | ||
| + | define server = 172.16.213.0/24 | ||
| + | define mgmt = 172.18.213.0/24 | ||
| + | define dmz = 10.88.213.0/24 | ||
| + | define local_tcp_ports = { 22 } | ||
| + | |||
| + | flush ruleset | ||
| + | table inet filter { | ||
| + | chain input { | ||
| + | type filter hook input priority filter; policy drop; | ||
| + | ct state established,related accept | ||
| + | ct state new iifname "lo" accept | ||
| + | ct state new tcp dport $local_tcp_ports accept | ||
| + | ct state new icmp type echo-request accept | ||
| + | log prefix "--nftables-drop-input--" | ||
| + | } | ||
| + | |||
| + | chain forward { | ||
| + | type filter hook forward priority filter; policy drop; | ||
| + | log prefix "--nftables-drop-forward--" | ||
| + | } | ||
| + | |||
| + | chain output { | ||
| + | type filter hook output priority filter; policy drop; | ||
| + | ct state established,related accept | ||
| + | ct state new oifname "lo" accept | ||
| + | ct state new accept | ||
| + | log prefix "--nftables-drop-output--" | ||
| + | } | ||
| + | } | ||
| + | |||
| + | <span style="color:#FF0000">table inet nat {</span> | ||
| + | <span style="color:#FF0000"> chain postrouting {</span> | ||
| + | <span style="color:#FF0000"> type nat hook postrouting priority 100; policy accept;</span> | ||
| + | <span style="color:#FF0000"> oif $wandev ip saddr $lan snat to $wanip</span> | ||
| + | <span style="color:#FF0000"> oif $wandev ip saddr $server snat to $wanip</span> | ||
| + | <span style="color:#FF0000"> oif $wandev ip saddr $mgmt snat to $wanip</span> | ||
| + | <span style="color:#FF0000"> # DMZ wird genattet, außer zu 10.88.0.0/16 und 10.82.89.0/24</span> | ||
| + | <span style="color:#FF0000"> oif $wandev ip saddr $dmz ip daddr != { 10.88.0.0/16, 10.82.89.0/24 } snat to $wanip</span> | ||
| + | <span style="color:#FF0000"> }</span> | ||
| + | <span style="color:#FF0000">}</span> | ||
| + | |||
| + | Neu verwendete Syntax: | ||
| + | |||
| + | * Definieren einer Variable | ||
| + | |||
| + | define ''variable_name'' = ''value'' | ||
| + | |||
| + | * Interface des herausgehenden Paketes: | ||
| + | |||
| + | oif ''device_name'' | ||
| + | |||
| + | * matche IPv4-Adresse des Ursprungpaketes | ||
| + | |||
| + | ip saddr ''<source_ip>'' | ||
| + | |||
| + | * Die Ursprungs-IP auf eine andere Adresse natten | ||
| + | |||
| + | snat ip to ''<new_source_ip>'' | ||
| + | |||
| + | =Forward von innen nach aussen= | ||
| + | *Wir wollen das unsere Clients und die Server vorerst nach aussen alles dürfen. | ||
| + | #!/usr/sbin/nft -f | ||
| + | define wandev = enp0s3 | ||
| + | define wanip = 192.168.5.213 | ||
| + | define lan = 172.17.213.0/24 | ||
| + | define server = 172.16.213.0/24 | ||
| + | define mgmt = 172.18.213.0/24 | ||
| + | define dmz = 10.88.213.0/24 | ||
| + | define local_tcp_ports = { 22 } | ||
| + | <span style="color:#FF0000">define localnets = { $lan , $server , $dmz, $mgmt}</span> | ||
| + | |||
| + | flush ruleset | ||
| + | table inet filter { | ||
| + | chain input { | ||
| + | type filter hook input priority filter; policy drop; | ||
| + | ct state established,related accept | ||
| + | ct state new iifname "lo" accept | ||
| + | ct state new tcp dport $local_tcp_ports accept | ||
| + | ct state new icmp type echo-request accept | ||
| + | log prefix "--nftables-drop-input--" | ||
| + | } | ||
| + | |||
| + | chain forward { | ||
| + | type filter hook forward priority filter; policy drop; | ||
| + | <span style="color:#FF0000">ct state established,related accept</span> | ||
| + | <span style="color:#FF0000">ct state new ip saddr $localnets accept</span> | ||
| + | log prefix "--nftables-drop-forward--" | ||
| + | } | ||
| + | |||
| + | chain output { | ||
| + | type filter hook output priority filter; policy drop; | ||
| + | ct state established,related accept | ||
| + | ct state new oifname "lo" accept | ||
| + | ct state new accept | ||
| + | log prefix "--nftables-drop-output--" | ||
| + | } | ||
| + | } | ||
| + | |||
| + | table inet nat { | ||
| + | chain postrouting { | ||
| + | type nat hook postrouting priority 100; policy accept; | ||
| + | oif $wandev ip saddr $lan snat to $wanip | ||
| + | oif $wandev ip saddr $server snat to $wanip | ||
| + | oif $wandev ip saddr $mgmt snat to $wanip | ||
| + | # DMZ wird genattet, außer zu 10.88.0.0/16 und 10.82.89.0/24 | ||
| + | oif $wandev ip saddr $dmz ip daddr != { 10.88.0.0/16, 10.82.89.0/24 } snat to $wanip | ||
| + | } | ||
| + | } | ||
| + | |||
| + | =Unsere Netze dürfen auf die Firewall andere nicht= | ||
| + | *Wir wollen das unsere Clients und die Server vorerst nach aussen alles dürfen. | ||
| + | #!/usr/sbin/nft -f | ||
| + | define wandev = enp0s3 | ||
| + | <span style="color:#FF0000">define dmzdev = enp0s9</span> | ||
| + | <span style="color:#FF0000">define landev = enp0s8</span> | ||
| + | <span style="color:#FF0000">define serverdev = enp0s10</span> | ||
| + | define wanip = 192.168.5.213 | ||
| + | define lan = 172.17.213.0/24 | ||
| + | define server = 172.16.213.0/24 | ||
| + | define mgmt = 172.18.213.0/24 | ||
| + | define dmz = 10.88.213.0/24 | ||
| + | define local_tcp_ports = { 22 } | ||
| + | define localnets = { $lan , $server , $dmz, $server} | ||
| + | <span style="color:#FF0000">define host = 192.168.10.200</span> | ||
| + | flush ruleset | ||
| + | table inet filter { | ||
| + | chain input { | ||
| + | type filter hook input priority filter; policy drop; | ||
| + | ct state established,related accept | ||
| + | ct state new iifname "lo" accept | ||
| + | <span style="color:#FF0000">ct state new iif $landev ip saddr $lan tcp dport $local_tcp_ports accept</span> | ||
| + | <span style="color:#FF0000">ct state new iif $dmzdev ip saddr $dmz tcp dport $local_tcp_ports accept</span> | ||
| + | <span style="color:#FF0000">ct state new iif $serverdev ip saddr $server tcp dport $local_tcp_ports accept</span> | ||
| + | <span style="color:#FF0000">ct state new iif $wandev ip saddr $host tcp dport $local_tcp_ports accept</span> | ||
| + | ct state new icmp type echo-request accept | ||
| + | log prefix "--nftables-drop-input--" | ||
| + | } | ||
| + | |||
| + | chain forward { | ||
| + | type filter hook forward priority filter; policy drop; | ||
| + | ct state established,related accept | ||
| + | ct state new saddr $localnets accept | ||
| + | log prefix "--nftables-drop-forward--" | ||
| + | } | ||
| + | |||
| + | chain output { | ||
| + | type filter hook output priority filter; policy drop; | ||
| + | ct state established,related accept | ||
| + | ct state new oifname "lo" accept | ||
| + | ct state new accept | ||
| + | log prefix "--nftables-drop-output--" | ||
| + | } | ||
| + | } | ||
| + | |||
| + | table inet nat { | ||
| + | chain postrouting { | ||
| + | type nat hook postrouting priority 100; policy accept; | ||
| + | oif $wandev ip saddr $lan snat to $wanip | ||
| + | oif $wandev ip saddr $server snat to $wanip | ||
| + | oif $wandev ip saddr $mgmt snat to $wanip | ||
| + | # DMZ wird genattet, außer zu 10.88.0.0/16 und 10.82.89.0/24 | ||
| + | oif $wandev ip saddr $dmz ip daddr != { 10.88.0.0/16, 10.82.89.0/24 } snat to $wanip | ||
| + | } | ||
| + | } | ||
| + | |||
| + | =Regeln von aussen nach innen= | ||
| + | *Die Regel die eingefügt wurde bedeutet folgendes: | ||
| + | *Ein Paket welches in die Schnittstelle enp0s3 reingeht und den Rechner über enp0s9 verlässt. | ||
| + | *und die Absendeadresse Host hat, sowie an die Zieladresse des Nameserver und an den Zielport 22 gerichtet ist. | ||
| + | *wird durch gelassen und in den Conntrack Tabelle aufgenommen. | ||
| + | |||
| + | #!/usr/sbin/nft -f | ||
| + | define wandev = enp0s3 | ||
| + | define landev = enp0s9 | ||
| + | define serverdev = enp0s8 | ||
| + | define mgmtdev = enp0s10 | ||
| + | define wanip = 192.168.5.213 | ||
| + | define lan = 172.17.213.0/24 | ||
| + | define server = 172.16.213.0/24 | ||
| + | define mgmt = 172.18.213.0/24 | ||
| + | define dmz = 10.88.213.0/24 | ||
| + | define local_tcp_ports = { 22 } | ||
| + | define localnets = { $lan , $server , $dmz, $server } | ||
| + | define host = 192.168.10.200 | ||
| + | define ns = 10.88.213.21 | ||
| + | |||
| + | flush ruleset | ||
| + | table inet filter { | ||
| + | chain input { | ||
| + | type filter hook input priority filter; policy drop; | ||
| + | ct state established,related accept | ||
| + | ct state new iifname "lo" accept | ||
| + | ct state new iifname $landev ip saddr $lan tcp dport $local_tcp_ports accept | ||
| + | ct state new iifname $dmzdev ip saddr $dmz tcp dport $local_tcp_ports accept | ||
| + | ct state new iifname $serverdev ip saddr $server tcp dport $local_tcp_ports accept | ||
| + | ct state new icmp type echo-request accept | ||
| + | log prefix "--nftables-drop-input--" | ||
| + | } | ||
| + | |||
| + | chain forward { | ||
| + | type filter hook forward priority filter; policy drop; | ||
| + | ct state established,related accept | ||
| + | <span style="color:#FF0000"> ct state new iif $wandev oif $dmzdev ip saddr $host ip daddr $ns tcp dport 22 accept | ||
| + | </span> | ||
| + | |||
| + | ct state new ip saddr $localnets accept | ||
| + | log prefix "--nftables-drop-forward--" | ||
| + | } | ||
| + | |||
| + | chain output { | ||
| + | type filter hook output priority filter; policy drop; | ||
| + | ct state established,related accept | ||
| + | ct state new oifname "lo" accept | ||
| + | ct state new accept | ||
| + | log prefix "--nftables-drop-output--" | ||
| + | } | ||
| + | } | ||
| + | |||
| + | table inet nat { | ||
| + | chain postrouting { | ||
| + | type nat hook postrouting priority 100; policy accept; | ||
| + | oif $wandev ip saddr $lan snat to $wanip | ||
| + | oif $wandev ip saddr $server snat to $wanip | ||
| + | oif $wandev ip saddr $mgmt snat to $wanip | ||
| + | # DMZ wird genattet, außer zu 10.88.0.0/16 und 10.82.89.0/24 | ||
| + | oif $wandev ip saddr $dmz ip daddr != { 10.88.0.0/16, 10.82.89.0/24 } snat to $wanip | ||
| + | } | ||
| + | } | ||
| − | + | =Man kann die Variablen auch auslagern= | |
| + | ;Wichtig sind die Anführungszeichen | ||
| + | include "/etc/nftables.var" | ||
| + | =old stuff= | ||
| + | *[[nftables-net-oldstuff]] | ||
Aktuelle Version vom 25. Juli 2025, 12:11 Uhr
Einleitung
- Nachdem wir ein Hostsystem abgesichert haben, kommen wir nun zum Absichern von Netzen.
- Die Firewall agiert als Vermittler zwischen verschiedenen Netzen.
- In unserem Beispiel haben wir 3 Netzbereiche.
WAN
- Wide Area Net steht für alles was nicht die anderen beiden Netze betrifft
LAN
- Local Area Net steht in der Regel für ein Netz das von aussen nicht erreichbar ist.
- Meist ist es über Network Address Translation (NAT) angebunden.
DMZ
- Demilitarized Zone ist ein Netz welches von außen erreichbar ist.
- Die Zugriffe werden aber durch die Firewall abgesichert.
- Dort werden meistens Dienste wie Mail oder Web gehostet. Teilweise auch Proxy Server.
Der Plan
Das Grundgerüst
- Wir nutzen unsere Host Firewall als Ausgangsskript
- Wir wollen aber von vorneherein verstärkt mit Variablen arbeiten.
- Dies macht die Skripte universeller.
- vim /etc/nftables.conf
#!/usr/sbin/nft -f
define wandev = enp0s3
define wanip = 192.168.5.213
define lan = 172.17.213.0/24
define server = 172.16.213.0/24
define mgmt = 172.18.213.0/24
define dmz = 10.88.213.0/24
define local_tcp_ports = { 22 }
flush ruleset
table inet filter {
chain input {
type filter hook input priority filter; policy drop;
ct state established,related accept
ct state new iifname "lo" accept
ct state new tcp dport $local_tcp_ports accept
ct state new icmp type echo-request accept
log prefix "--nftables-drop-input--"
}
chain forward {
type filter hook forward priority filter; policy drop;
ct state established,related accept
log prefix "--nftables-drop-forward--"
}
chain output {
type filter hook output priority filter; policy drop;
ct state established,related accept
ct state new oifname "lo" accept
ct state new accept
log prefix "--nftables-drop-output--"
}
}
table inet nat {
chain postrouting {
type nat hook postrouting priority 100; policy accept;
oif $wandev ip saddr $lan snat to $wanip
oif $wandev ip saddr $server snat to $wanip
oif $wandev ip saddr $mgmt snat to $wanip
# DMZ wird genattet, außer zu 10.88.0.0/16 und 10.82.89.0/24
oif $wandev ip saddr $dmz ip daddr != { 10.88.0.0/16, 10.82.89.0/24 } snat to $wanip
}
Forwarding
Damit Pakete weitergeleitet werden können, muss als erstes FORWARDING im Kernel aktiviert werden.
Aktivierung
- echo "net.ipv4.ip_forward = 1" >> /etc/sysctl.conf
- sysctl -p
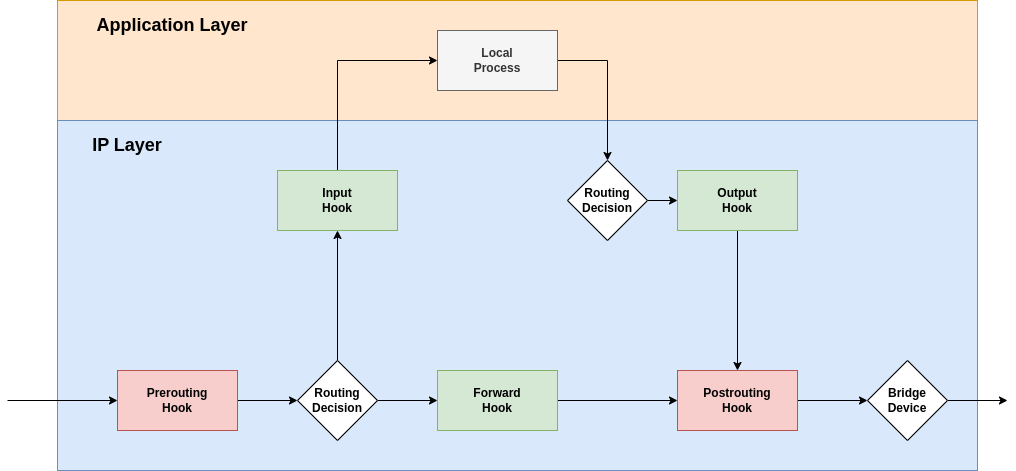
Weitere Tabellen
- Eine Skizze über die Reihenfolge der Hooks.
- Als erstes greift der Prerouting-Hook
- Je nachdem wie geroutet wird greift dann entweder Input- oder Fowrward-Hook
- Falls ein lokaler Prozess ein Paket sendet, dann greift der Output-Hook
- Als letztes kann man das Paket mit dem Postrouting-Hook beeinflußen
SNAT
- Rechner in einem LAN können nicht ohne weiteres mit dem WAN kommunizieren, da an die lokale IP-Adresse der Rechner im LAN nicht von außen geroutet werden kann.
- Um eine Internetverbindung aufzubauen, muss die Adresse aus dem LAN in eine öffentliche umgeschrieben werden.
#!/usr/sbin/nft -f
define wandev = enp0s3
define wanip = 192.168.5.213
define lan = 172.17.213.0/24
define server = 172.16.213.0/24
define mgmt = 172.18.213.0/24
define dmz = 10.88.213.0/24
define local_tcp_ports = { 22 }
flush ruleset
table inet filter {
chain input {
type filter hook input priority filter; policy drop;
ct state established,related accept
ct state new iifname "lo" accept
ct state new tcp dport $local_tcp_ports accept
ct state new icmp type echo-request accept
log prefix "--nftables-drop-input--"
}
chain forward {
type filter hook forward priority filter; policy drop;
log prefix "--nftables-drop-forward--"
}
chain output {
type filter hook output priority filter; policy drop;
ct state established,related accept
ct state new oifname "lo" accept
ct state new accept
log prefix "--nftables-drop-output--"
}
}
table inet nat {
chain postrouting {
type nat hook postrouting priority 100; policy accept;
oif $wandev ip saddr $lan snat to $wanip
oif $wandev ip saddr $server snat to $wanip
oif $wandev ip saddr $mgmt snat to $wanip
# DMZ wird genattet, außer zu 10.88.0.0/16 und 10.82.89.0/24
oif $wandev ip saddr $dmz ip daddr != { 10.88.0.0/16, 10.82.89.0/24 } snat to $wanip
}
}
Neu verwendete Syntax:
- Definieren einer Variable
define variable_name = value
- Interface des herausgehenden Paketes:
oif device_name
- matche IPv4-Adresse des Ursprungpaketes
ip saddr <source_ip>
- Die Ursprungs-IP auf eine andere Adresse natten
snat ip to <new_source_ip>
Forward von innen nach aussen
- Wir wollen das unsere Clients und die Server vorerst nach aussen alles dürfen.
#!/usr/sbin/nft -f
define wandev = enp0s3
define wanip = 192.168.5.213
define lan = 172.17.213.0/24
define server = 172.16.213.0/24
define mgmt = 172.18.213.0/24
define dmz = 10.88.213.0/24
define local_tcp_ports = { 22 }
define localnets = { $lan , $server , $dmz, $mgmt}
flush ruleset
table inet filter {
chain input {
type filter hook input priority filter; policy drop;
ct state established,related accept
ct state new iifname "lo" accept
ct state new tcp dport $local_tcp_ports accept
ct state new icmp type echo-request accept
log prefix "--nftables-drop-input--"
}
chain forward {
type filter hook forward priority filter; policy drop;
ct state established,related accept
ct state new ip saddr $localnets accept
log prefix "--nftables-drop-forward--"
}
chain output {
type filter hook output priority filter; policy drop;
ct state established,related accept
ct state new oifname "lo" accept
ct state new accept
log prefix "--nftables-drop-output--"
}
}
table inet nat {
chain postrouting {
type nat hook postrouting priority 100; policy accept;
oif $wandev ip saddr $lan snat to $wanip
oif $wandev ip saddr $server snat to $wanip
oif $wandev ip saddr $mgmt snat to $wanip
# DMZ wird genattet, außer zu 10.88.0.0/16 und 10.82.89.0/24
oif $wandev ip saddr $dmz ip daddr != { 10.88.0.0/16, 10.82.89.0/24 } snat to $wanip
}
}
Unsere Netze dürfen auf die Firewall andere nicht
- Wir wollen das unsere Clients und die Server vorerst nach aussen alles dürfen.
#!/usr/sbin/nft -f define wandev = enp0s3 define dmzdev = enp0s9 define landev = enp0s8 define serverdev = enp0s10 define wanip = 192.168.5.213 define lan = 172.17.213.0/24 define server = 172.16.213.0/24 define mgmt = 172.18.213.0/24 define dmz = 10.88.213.0/24 define local_tcp_ports = { 22 } define localnets = { $lan , $server , $dmz, $server} define host = 192.168.10.200 flush ruleset table inet filter { chain input { type filter hook input priority filter; policy drop; ct state established,related accept ct state new iifname "lo" accept ct state new iif $landev ip saddr $lan tcp dport $local_tcp_ports accept ct state new iif $dmzdev ip saddr $dmz tcp dport $local_tcp_ports accept ct state new iif $serverdev ip saddr $server tcp dport $local_tcp_ports accept ct state new iif $wandev ip saddr $host tcp dport $local_tcp_ports accept ct state new icmp type echo-request accept log prefix "--nftables-drop-input--" } chain forward { type filter hook forward priority filter; policy drop; ct state established,related accept ct state new saddr $localnets accept log prefix "--nftables-drop-forward--" } chain output { type filter hook output priority filter; policy drop; ct state established,related accept ct state new oifname "lo" accept ct state new accept log prefix "--nftables-drop-output--" } } table inet nat { chain postrouting { type nat hook postrouting priority 100; policy accept; oif $wandev ip saddr $lan snat to $wanip oif $wandev ip saddr $server snat to $wanip oif $wandev ip saddr $mgmt snat to $wanip # DMZ wird genattet, außer zu 10.88.0.0/16 und 10.82.89.0/24 oif $wandev ip saddr $dmz ip daddr != { 10.88.0.0/16, 10.82.89.0/24 } snat to $wanip } }
Regeln von aussen nach innen
- Die Regel die eingefügt wurde bedeutet folgendes:
- Ein Paket welches in die Schnittstelle enp0s3 reingeht und den Rechner über enp0s9 verlässt.
- und die Absendeadresse Host hat, sowie an die Zieladresse des Nameserver und an den Zielport 22 gerichtet ist.
- wird durch gelassen und in den Conntrack Tabelle aufgenommen.
#!/usr/sbin/nft -f
define wandev = enp0s3
define landev = enp0s9
define serverdev = enp0s8
define mgmtdev = enp0s10
define wanip = 192.168.5.213
define lan = 172.17.213.0/24
define server = 172.16.213.0/24
define mgmt = 172.18.213.0/24
define dmz = 10.88.213.0/24
define local_tcp_ports = { 22 }
define localnets = { $lan , $server , $dmz, $server }
define host = 192.168.10.200
define ns = 10.88.213.21
flush ruleset
table inet filter {
chain input {
type filter hook input priority filter; policy drop;
ct state established,related accept
ct state new iifname "lo" accept
ct state new iifname $landev ip saddr $lan tcp dport $local_tcp_ports accept
ct state new iifname $dmzdev ip saddr $dmz tcp dport $local_tcp_ports accept
ct state new iifname $serverdev ip saddr $server tcp dport $local_tcp_ports accept
ct state new icmp type echo-request accept
log prefix "--nftables-drop-input--"
}
chain forward {
type filter hook forward priority filter; policy drop;
ct state established,related accept
ct state new iif $wandev oif $dmzdev ip saddr $host ip daddr $ns tcp dport 22 accept
ct state new ip saddr $localnets accept
log prefix "--nftables-drop-forward--"
}
chain output {
type filter hook output priority filter; policy drop;
ct state established,related accept
ct state new oifname "lo" accept
ct state new accept
log prefix "--nftables-drop-output--"
}
}
table inet nat {
chain postrouting {
type nat hook postrouting priority 100; policy accept;
oif $wandev ip saddr $lan snat to $wanip
oif $wandev ip saddr $server snat to $wanip
oif $wandev ip saddr $mgmt snat to $wanip
# DMZ wird genattet, außer zu 10.88.0.0/16 und 10.82.89.0/24
oif $wandev ip saddr $dmz ip daddr != { 10.88.0.0/16, 10.82.89.0/24 } snat to $wanip
}
}
Man kann die Variablen auch auslagern
- Wichtig sind die Anführungszeichen
include "/etc/nftables.var"