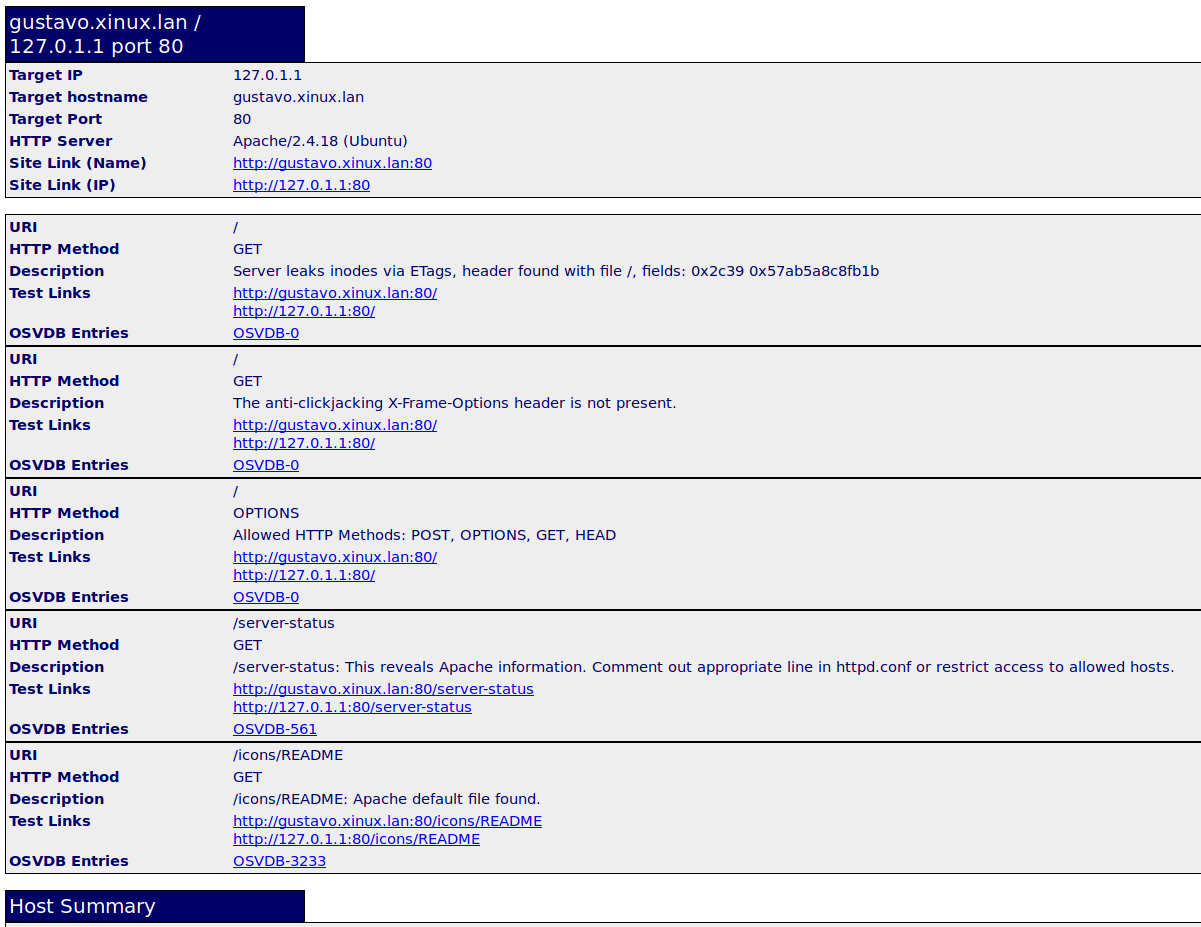
Nikto: Unterschied zwischen den Versionen
Zur Navigation springen
Zur Suche springen
| Zeile 9: | Zeile 9: | ||
*apt-get install nikto | *apt-get install nikto | ||
=Anwendung= | =Anwendung= | ||
| − | *nikto -h | + | *nikto -h opfer.secure.local -p 80 |
<pre> | <pre> | ||
| − | + | - Nikto v2.1.6 | |
| − | - Nikto v2.1. | ||
--------------------------------------------------------------------------- | --------------------------------------------------------------------------- | ||
| − | + Target IP: | + | + Target IP: 10.0.10.104 |
| − | + Target Hostname: | + | + Target Hostname: opfer.secure.local |
+ Target Port: 80 | + Target Port: 80 | ||
| − | + Start Time: | + | + Start Time: 2021-08-04 15:35:03 (GMT2) |
--------------------------------------------------------------------------- | --------------------------------------------------------------------------- | ||
| − | + Server: Apache/2.4. | + | + Server: Apache/2.4.7 (Ubuntu) |
| − | |||
+ The anti-clickjacking X-Frame-Options header is not present. | + The anti-clickjacking X-Frame-Options header is not present. | ||
| + | + The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS | ||
| + | + The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type | ||
+ No CGI Directories found (use '-C all' to force check all possible dirs) | + No CGI Directories found (use '-C all' to force check all possible dirs) | ||
| − | + Allowed HTTP Methods: POST, OPTIONS | + | + Apache/2.4.7 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch. |
| − | + OSVDB- | + | + Server may leak inodes via ETags, header found with file /, inode: 1d4, size: 5c81e4a62d19e, mtime: gzip |
| + | + Cookie PHPSESSID created without the httponly flag | ||
| + | + Retrieved x-powered-by header: PHP/5.5.9-1ubuntu4.29 | ||
| + | + Allowed HTTP Methods: GET, HEAD, POST, OPTIONS | ||
| + | + /test.php: Output from the phpinfo() function was found. | ||
| + | + /config.php: PHP Config file may contain database IDs and passwords. | ||
| + | + OSVDB-3233: /test.php: PHP is installed, and a test script which runs phpinfo() was found. This gives a lot of system information. | ||
+ OSVDB-3233: /icons/README: Apache default file found. | + OSVDB-3233: /icons/README: Apache default file found. | ||
| − | + | + | + /login.php: Admin login page/section found. |
| − | + End Time: | + | + OSVDB-3092: /test.php: This might be interesting... |
| + | + 7863 requests: 0 error(s) and 14 item(s) reported on remote host | ||
| + | + End Time: 2021-08-04 15:35:50 (GMT2) (47 seconds) | ||
--------------------------------------------------------------------------- | --------------------------------------------------------------------------- | ||
+ 1 host(s) tested | + 1 host(s) tested | ||
</pre> | </pre> | ||
| + | |||
=Weiteres= | =Weiteres= | ||
*-h = target host | *-h = target host | ||
Version vom 4. August 2021, 13:36 Uhr
Erklärung
- Nikto Web Scanner ist ein Webserver-Scanner,
- Er testet Webserver auf gefährliche Dateien/CGIs
- Sowie veraltete Serversoftware und andere Probleme testet.
- Er führt auch generische und servertypspezifische Prüfungen durch.
- Außerdem erfasst und gibt alle empfangenen Cookies aus.
Installation
- apt-get install nikto
Anwendung
- nikto -h opfer.secure.local -p 80
- Nikto v2.1.6 --------------------------------------------------------------------------- + Target IP: 10.0.10.104 + Target Hostname: opfer.secure.local + Target Port: 80 + Start Time: 2021-08-04 15:35:03 (GMT2) --------------------------------------------------------------------------- + Server: Apache/2.4.7 (Ubuntu) + The anti-clickjacking X-Frame-Options header is not present. + The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type + No CGI Directories found (use '-C all' to force check all possible dirs) + Apache/2.4.7 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch. + Server may leak inodes via ETags, header found with file /, inode: 1d4, size: 5c81e4a62d19e, mtime: gzip + Cookie PHPSESSID created without the httponly flag + Retrieved x-powered-by header: PHP/5.5.9-1ubuntu4.29 + Allowed HTTP Methods: GET, HEAD, POST, OPTIONS + /test.php: Output from the phpinfo() function was found. + /config.php: PHP Config file may contain database IDs and passwords. + OSVDB-3233: /test.php: PHP is installed, and a test script which runs phpinfo() was found. This gives a lot of system information. + OSVDB-3233: /icons/README: Apache default file found. + /login.php: Admin login page/section found. + OSVDB-3092: /test.php: This might be interesting... + 7863 requests: 0 error(s) and 14 item(s) reported on remote host + End Time: 2021-08-04 15:35:50 (GMT2) (47 seconds) --------------------------------------------------------------------------- + 1 host(s) tested
Weiteres
- -h = target host
- -p = port
- -l = List all available plugins
- -F = Format (z.B. HTML, TXT, XML)
- -o = Write output to this file (z.B. webscan.html)
- -s = Force ssl mode on port